cmd.so Synology Scanner Also Found on Routers
Yesterday, we talked about a scanner looking for Synology devices that was running on a ARM CPU equipped DVR. Looking at a few other sources of these scans, we did see a couple that didn't originate from similar DVRs. The first guess was that the scan originated from a device that was sitting behind a NAT gateway and wasn't exposed. At this point, it could have been "anything", even a good old infected Windows PC.
To our surprise, at least in one case it turned out that a binary by the same name, "cmd.so", was running on the NAT router itself. In addition, a second process was running that looked just like the bitcoin miner we saw running in the infected DVRs. Sadly, we were not able to retrieve the binaries, but the processlist looks similar enough to make us believe that this is the same basic binary just compiled for MIPS in this case (the router in question uses a MIPS CPU).
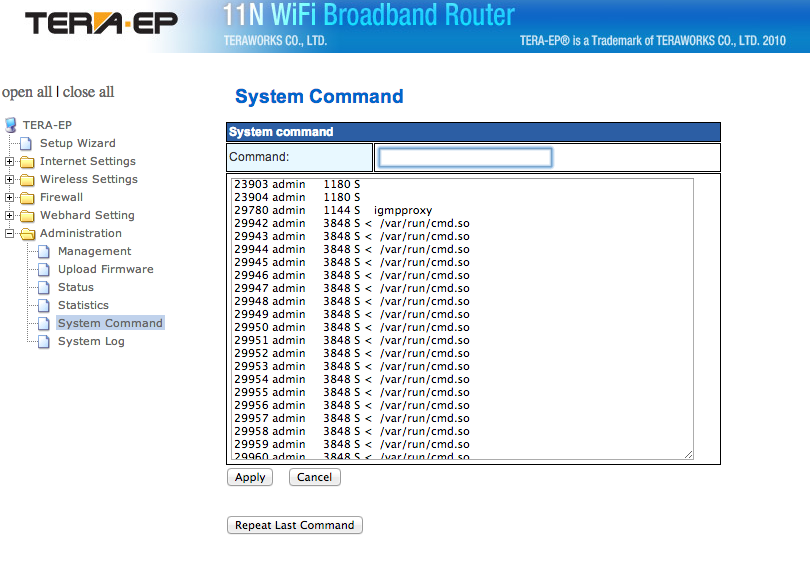
The first image shows the processlist with "cmd.so". In this case, the binary was dropped in /var/run, not /dev, likely due to the different architecture of the router allowing write access to /var/run. The screen show shows a partial output of the "ps" command executed using the routers web based admin interface.
Figure 1: Partial Process List with "cmd.so". Click on image for larger version.
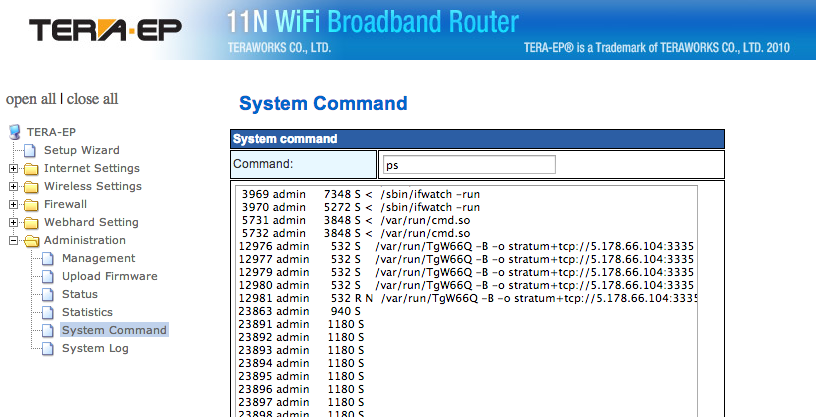
Figure 2: Partial "ps" output showing the suspected bitcoin miner. In this case, it is called TgW66Q.
The process we think is a copy on minerd uses the same command line parameters as the process we identified as minerd on the DVR.
If you got a router like this, take a look what you find. We do still need a copy of the respective executables to confirm our suspicion.
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments
Anonymous
Apr 2nd 2014
1 decade ago