UDP port 1900 DDoS traffic
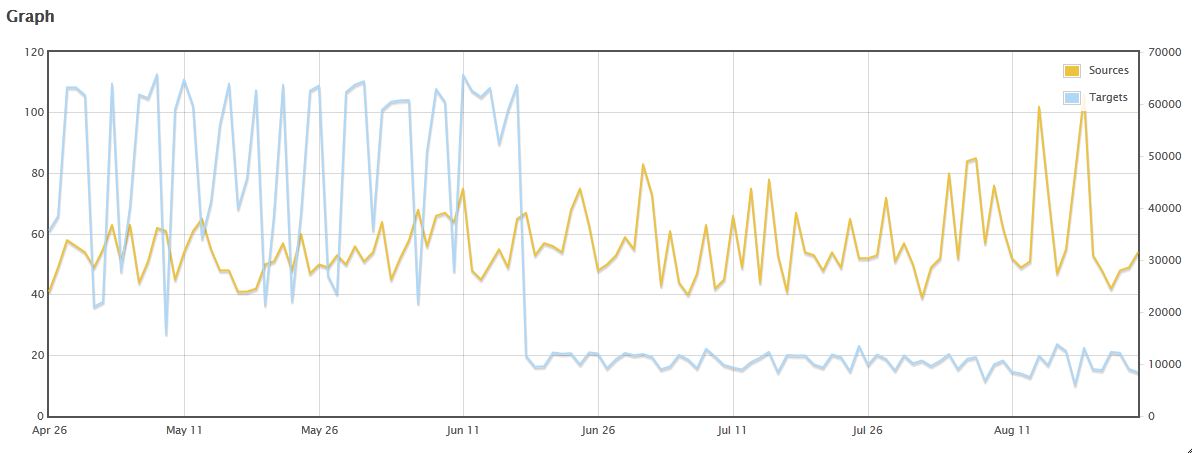
I guess this is my day for asking for feedback from our readers. Again, I'm going to ask "Got packets?" On 22 Aug, one of our readers (Paul) commented on the Port 1900 page that he was seeing a DDoS on port 1900, with packet sizes of 300 bytes. This is a development we've been watching at $dayjob, too, but I was wondering if anyone (including Paul) has packets so we can try to figure out what the amplification mechanism might actually be (if you have the packets, please share via the contact page). What we're seeing in Dshield data is a little odd and different from what I'm seeing at $dayjob. You'll note below that there were a more targets until they suddenly dropped off on 18 Jun. On the other hand, the sources seem to be trending upward (at least, peaking higher). Unfortunately, we only have source and target counts in the Dshield data, not byte volumes. Compare that with what we're seeing at the $dayjob as shown in the webcast we do weekly there (from 39:55 in this video -- watch to about 47:00 if you want to see our discussion of all the reflective DoS ports we're watching).
References:
[1] https://isc.sans.edu/port.html?port=1900
[2] http://techchannel.att.com/play-video.cfm/2014/8/14/AT&T-ThreatTraq-1-Billion-Accounts-Hacked
---------------
Jim Clausing, GIAC GSE #26
jclausing --at-- isc [dot] sans (dot) edu
| Reverse-Engineering Malware: Malware Analysis Tools and Techniques | Online | Japan Standard Time | Mar 9th - Mar 14th 2026 |


Comments
Anonymous
Aug 26th 2014
1 decade ago
Anonymous
Aug 27th 2014
1 decade ago
Anonymous
Aug 27th 2014
1 decade ago
Anonymous
May 22nd 2015
1 decade ago
Date flow start Duration Proto Src IP Addr:Port Dst IP Addr:Port Out Pkt In Pkt Out Byte In Byte Flows
2015-05-21 17:32:25.217 0.000 UDP 175.213.180.136:1900 <-> x.x.x.x:59860 0 250 0 74250 1
2015-05-21 17:32:04.928 0.000 UDP 220.81.19.12:1900 <-> x.x.x.x:3718 0 250 0 87250 1
2015-05-21 17:33:29.050 0.000 UDP 75.128.89.170:1900 <-> x.x.x.x:59585 0 250 0 84500 1
2015-05-21 17:33:02.444 0.000 UDP 95.81.254.194:1900 <-> x.x.x.x:5262 0 250 0 90750 1
2015-05-21 17:31:56.313 0.000 UDP 66.211.122.130:1900 <-> x.x.x.x:42917 0 250 0 89500 1
2015-05-21 17:32:39.476 0.000 UDP 24.239.53.249:1900 <-> x.x.x.x:64858 0 250 0 81250 1
2015-05-21 17:33:00.749 0.000 UDP 104.162.232.26:1900 <-> x.x.x.x:51886 0 250 0 78500 1
2015-05-21 17:32:07.785 0.000 UDP 204.15.156.117:1900 <-> x.x.x.x:6433 0 250 0 83250 1
So the packets were of slightly varying size.
Anonymous
May 22nd 2015
1 decade ago
Any chance you have full packet capture? IF so....https://isc.sans.edu/contact.html
Rick
Anonymous
May 22nd 2015
1 decade ago