UDDIs are back? Attackers rediscovering old exploits.
Looking at our "first seen URLs" today, I noticed the following odd request:
/uddiexplorer/SearchPublicRegistries.jsp?operator=http://127.0.0.1:65535&rdoSearch=name&txtSearchname=sdf&txtSearchkey=&txtSearchfor=&selfor=Business+location&btnSubmit=Search
UDDIs are a concept that had great promise but never quite made it. I would consider it dead at this point, but I wouldn't be surprised to find it in some enterprise systems. A "UDDI" (Universal Description, Discovery, and Integration) is a directory of web services. The idea behind is to automatically find web services belonging to an organization, including the associated documentation (WSDLs), to more or less automate the creation of clients for these web services. It was kind of a neat concept that never lived up to its promise.
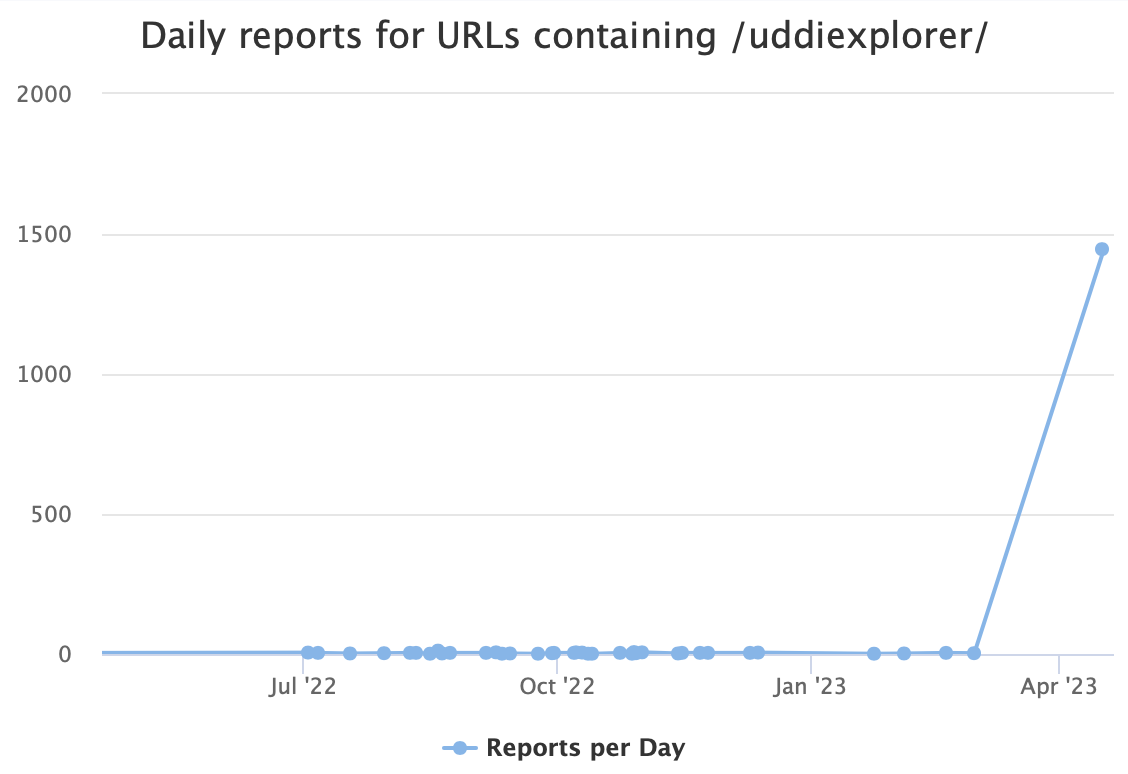
This URL suddenly appears quite popular, with 1,446 scans today. In the past, we have seen occasional scans for similar "uddiexplorer" URLs. This time, the only IP scanning for them is 115.60.149.84. It appears to be a "random" Chinese ADSL IP address that only scans port 7001, a port typically assigned to WebLogic.
Back then, WebLogic suffered from an easily exploitable SSRF vulnerability, CVE-2014-4210. The almost ten-year-old vulnerability still appears to be attracting some attacks. Some attacks still appear to find this an attractive target. But the short lifetime of each scan likely shows that these scans are not successful.
We had small scans, with less than a dozen reports from our sensors, on March 1st and February. The "interesting part" is the "operator" parameter, which is the URL the attacker is trying to hit via SSRF. For example:
/uddiexplorer/SearchPublicRegistries.jsp?btnSubmit=Search&operator=http://cfveknb47rnbba000010ojuk6ku7xf$
zu.oast.site&rdoSearch=name&selfor=Business+location&txtSearchfor&txtSearchkey&txtSearchname=sdf
is an attempt to detect exploitability via OAST.
The graph below shows recent attempts containing the string "uddiexplorer":
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments