Shipping dangerous goods
For the past several months, I've been tracking a campaign that sends rather odd-looking emails like this
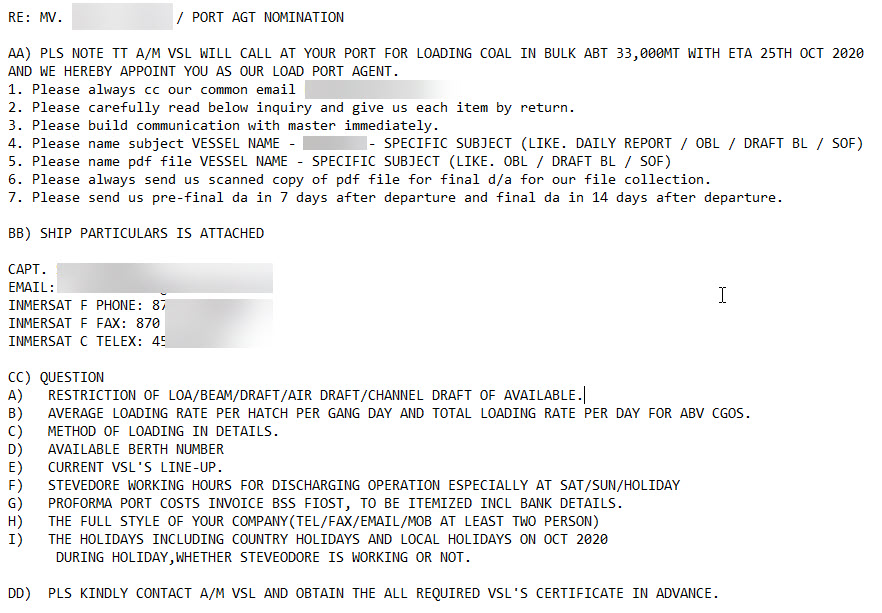
The sender (from) address on these emails is usually impersonating an existing shipping or logistics company. The ships mentioned in the emails actually exist, and according to marinetraffic.com, the vessels are in fact traveling in the area and with cargo that makes the content of such harbor berthing reservation and cargo manifest emails seem plausible.
Between two to five emails of this style arrive in one of my spam traps every weekday. The scammers don't work on the weekends, and sometimes, they take a full week off. But they inevitably come back, and try again. Most emails are received between 2am and 4am UTC, which - assuming the mails are sent during the local morning - could suggest that the sender is sitting somewhere between Bangkok and Shanghai. The sending email servers are everywhere, but show some clustering in Malaysia.
The emails themselves display a casual familiarity with marine jargon, tonnages, draft, cargo types, DWT, routing, ETAs and marine radio procedures. They would be mildly entertaining to read, before getting filed in the spam folder ... if it weren't for the attachment.
Sized between 500k and 1.5m, the attachment type of choice by the bad guys for the past several months has been a ".cab". Virustotal detection for the samples varies, and ranges from "none" at time of receipt, to 50+ engines a couple days later.
Two recent samples from this campaign
https://www.virustotal.com/gui/file/ba81b061a2dd678c1035ab99f70e36ce23446fa7f59a449722eac51dcb856d88/detection
https://www.virustotal.com/gui/file/40f23fd166724fa53a78234c4cdef2a8f95c2fc1e52bcd7b381efaa23cea6bc1/detection
The malware in question happens to be Agent Tesla spyware. Since April, my sandbox collected several hundred distinct Agent Tesla samples from this actor. Agent Tesla exfiltrates stolen data via HTTPS, and more commonly, over email (SMTPS, tcp/587). While the former (HTTPS) destinations tend to be rather random, the latter (email) destinations are often hosted on email domains that also belong to shipping companies. This indicates to me that the campaign is likely successful to some extent, and over the months in fact has managed to steal valid email credentials (and probably more than that) from firms in the shipping and logistics sector.
Indicators for the emails:
- look for emails with *.cab attachment, with the email subject in all-uppercase
Indicators post-compromise:
- look for outbound attempts to tcp/587 destined for email servers other than your own
Current tcp/587 C&C domains used are mail.trinityealtd[.]com and smtp.hyshippingcn[.]com, but these destinations are changing daily.
The campaign has a lot of commonalities with what BitDefender reported in April for the Oil&Gas industry https://labs.bitdefender.com/2020/04/oil-gas-spearphishing-campaigns-drop-agent-tesla-spyware-in-advance-of-historic-opec-deal/.
If you have additional information on this campaign, please let us know, or share in the comments below.
Update: Latest three samples from today, and their corresponding SMTP C2:
f00fadbb5208ce7cdfe655c99c3d0c
15f65230fb7dafdad1ca727fa7a3dd
e0be943cd75bbab62768510aaa1547


Comments