Qakbot infection with Cobalt Strike
Introduction
On Tuesday 2021-03-02, I generated a Qakbot (Qbot) infection on a Windows host in one of my Active Directory (AD) test environments, where I saw Cobalt Strike as follow-up activity. I've seen Cobalt Strike from Qakbot infections before. Below are two that I documented in December 2020.
- https://www.malware-traffic-analysis.net/2020/12/07/index.html
- https://www.malware-traffic-analysis.net/2020/12/15/index.html
I haven't documented one for the ISC yet, so today's diary reviews my Qakbot infection with Cobalt Strike seen on Tuesday 2021-03-02.
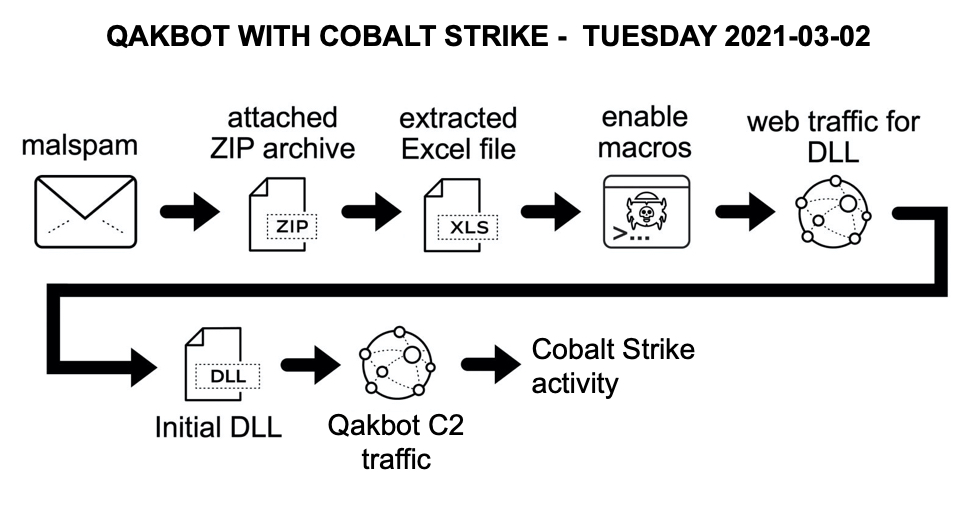
Shown above: Flow chart for the Qakbot infection with Cobalt Strike from Tuesday 2021-03-02.
Images
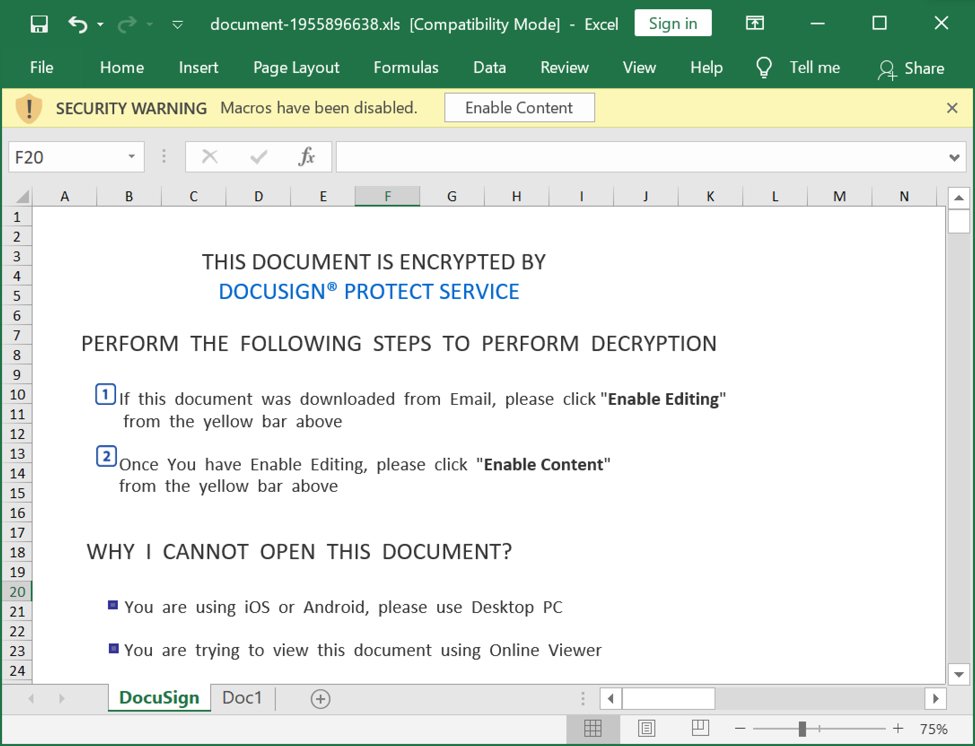
Shown above: Spreadsheet extracted from a zip archive attached to malspam pushing Qakbot.
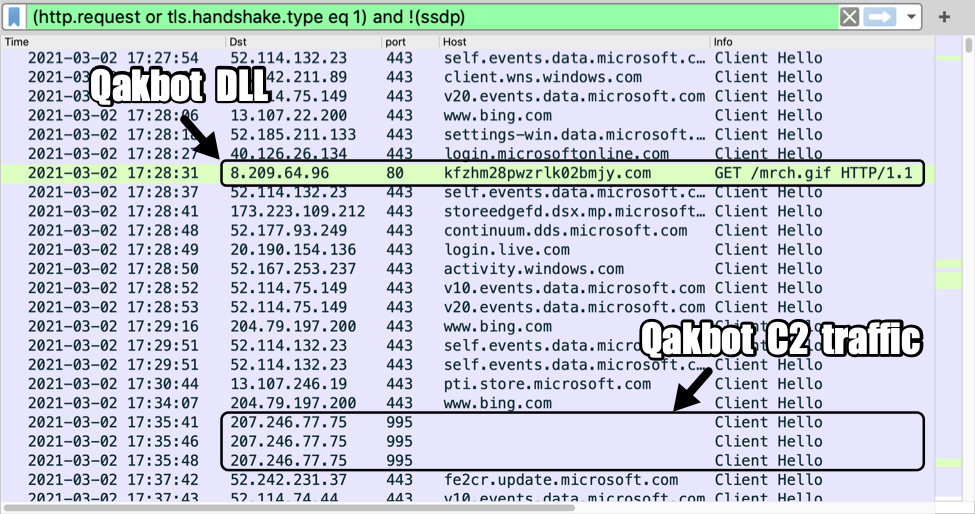
Shown above: Traffic from the infection filtered in Wireshark (image 1 of 3).
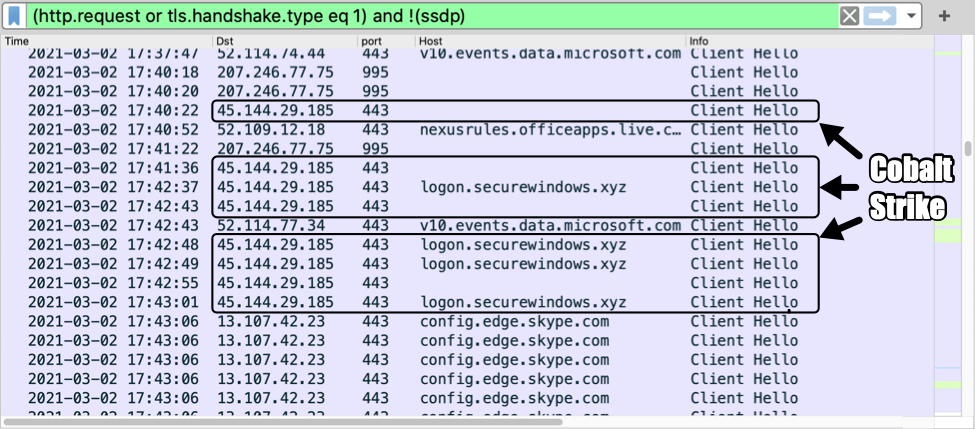
Shown above: Traffic from the infection filtered in Wireshark (image 2 of 3).
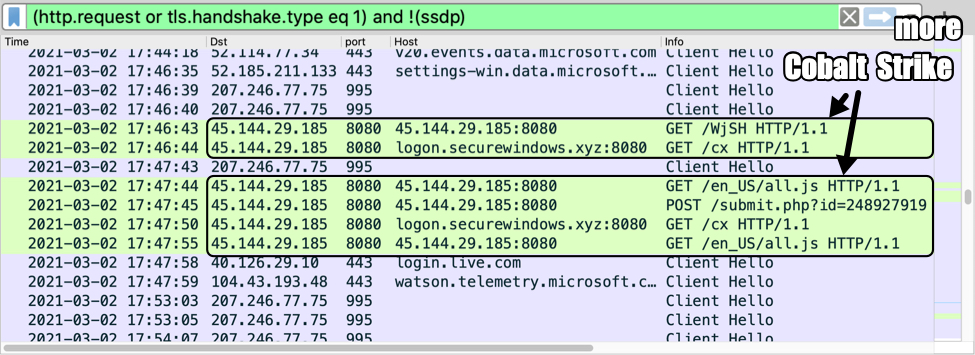
Shown above: Traffic from the infection filtered in Wireshark (image 3 of 3).
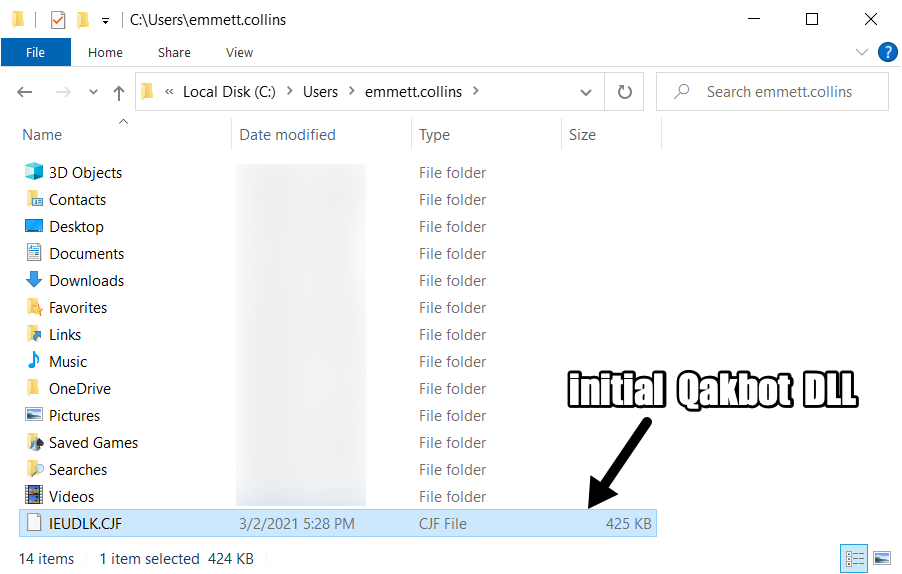
Shown above: Initial DLL saved a the victim's Windows host.
Shown above: Artifact saved to disk during the Qakbot infection.
Shown above: Registry updates caused by Qakbot.
Indicators of Compromise (IOCs)
Malware from the infected Windows host:
SHA256 hash: 16a0c2f741a14c423b7abe293e26f711fdb984fc52064982d874bf310c520b12
- File size: 87,552 bytes
- File name: document-1955896638.xls
- File description: Excel spreadsheet with macro for Qakbot (Qbot)
- Any.Run analysis: https://app.any.run/tasks/713d7a1f-6905-4ddd-92e4-84c0bbc97f89
- Cape analysis: https://capesandbox.com/analysis/121176/
- Triage analysis: https://tria.ge/210302-1lphqmv2px
SHA256 hash: 24753d9f0d691b6d582da3e301b98f75abbdb5382bb871ee00713c5029c56d44
- File size: 434,744 bytes
- File location: hxxp://kfzhm28pwzrlk02bmjy[.]com/mrch.gif
- File location: C:\Users\[username]\IEUDLK.CJF
- File description: Initial DLL for Qakbot (Qbot) retrieved by Excel macro
- Any.Run analysis: https://app.any.run/tasks/957a9919-b411-4724-b49f-8c9a1a4c95ab
- Cape analysis: https://capesandbox.com/analysis/120925/
- Triage analysis: https://tria.ge/210302-y9rqfzcq5x
Traffic to retrieve the initial Qakbot DLL:
- 8.209.64[.]96 port 80 - kfzhm28pwzrlk02bmjy[.]com - GET /mrch.gif
Qakbot C2 traffic:
- 207.246.77[.]75 port 995 - HTTPS traffic
Cobalt Strike traffic:
- 45.144.29[.]185 port 443 - HTTPS traffic
- 45.144.29[.]185 port 443 - logon.securewindows[.]xyz - HTTPS traffic
- 45.144.29[.]185 port 8080 - 45.144.29[.]185:8080 - GET /WjSH
- 45.144.29[.]185 port 8080 - logon.securewindows[.]xyz:8080 - GET /cx
- 45.144.29[.]185 port 8080 - 45.144.29[.]185:8080 - GET /en_US/all.js
- 45.144.29[.]185 port 8080 - 45.144.29[.]185:8080 - POST /submit.php?id=248927919
Final words
A pcap of the infection traffic and the associated malware can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments