Prowler v3: AWS & Azure security assessments
As a current Google Cloud Platform defender, and former Microsoft Azure defender, I appreciate any tool or capability intended to provide multi-cloud protection. As noted via LinkedIn, Toni announced the release of Prowler v3 just before Christmas. Prowler v3 is a complete overhaul of Prowler, fully rewritten it in Python. Prowler is an open source security tool to perform AWS and Azure security best practices assessments, audits, incident response, continuous monitoring, hardening and forensics readiness. Prowler v3 is now multi-cloud with Azure added as the second supported cloud provider. Prowler is significantly faster as well, now able to scan an entire AWS account across all regions 37 times faster than before.
Prowler v3 change log:
- Python: No more bash, now all in Python. 'pip install prowler-cloud' then run 'prowler'
- Performance improvements: an account that took 2.5 hours to scan in v2 now only takes 4 minutes to scan in v3
- Developers and Community: easier to contribute with new checks and new compliance frameworks, as well as unit tests and native logging features
- Multi-cloud: Currently AWS and Azure, the team plans to include GCP and OCI soon and would appreciate contributors
- Checks and Groups: all checks are now more comprehensive and we provide resolution actions in most of them
- Compliance: full support for CIS 1.4, CIS 1.5 and the new Spanish ENS in this release, more to come soon!
- Consolidated output formats: now both CSV and JSON reports come with the same attributes. HTML, CSV and JSON are created every time you run `prowler`
- Quick Inventory: fine tuned the Quick Inventory feature to get a list of all resources in your AWS accounts within seconds
- Document site: https://docs.prowler.cloud
To test Prowler, I installed, configured, and ran it against my AWS account with ease from my Mac mini running Python 3.9.12, as follows:
- pip install prowler-cloud
- prowler -v to confirm success and installed version
- ulimit -n 1000 to avoid file descriptor limits, macOS Ventura's default value for file descriptors is 256
- aws configure to use AWS IAM security credentials properly. This requires AWS CLI, which, if you did the 2022 SANS Holiday Hack Challenge over the holidays, you should be quite familiar with. Yes, I recovered the Cloud Ring ;-)
- prowler aws
Results are produced in CSV, HTML, and JSON, as well as a results table to the terminal. As you can see below, my results are terrible, and I have some attention to pay to my rarely used AWS account, current billing = .87 cents a month ;-).
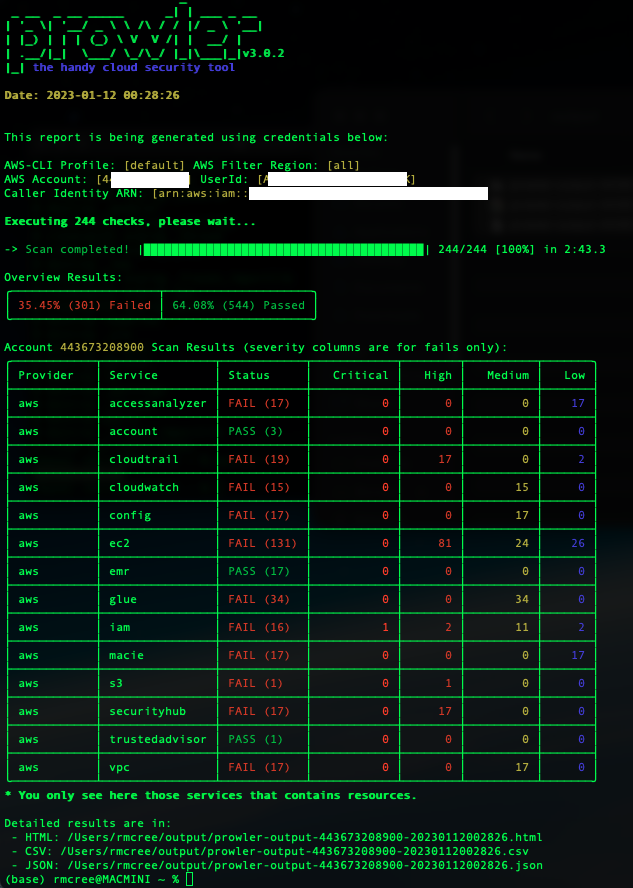
May I be the first to recommend you read all the Prowler resources, and immediately audit accounts and subscriptions in your care. I have in, my many years of cloud defense, seen the worst of the worst in cloud compromise, customer runaway spend, and cloud abuse, often the result of easily prevented misconfigurations and weak permissions. Go do! I look forward to the GCP version.
Cheers…until next time.
Russ McRee | @holisticinfosec | infosec.exchange/@holisticinfosec | LinkedIn.com/in/russmcree


Comments
I'm finding that the Azure support is not nearly as mature as the AWS feature set.
Is that what you find too?
I'm not sure what this gets me in the Azure space that's better than the Azure Security Center, HAWK [ https://github.com/T0pCyber/hawk ], Sparrow [ https://github.com/cisagov/Sparrow ], or the CRT [ https://github.com/CrowdStrike/CRT ].
What am I missing?
MrCarney
Jan 17th 2023
3 years ago
Russ McRee
May 6th 2023
2 years ago