Phishing page with trivial anti-analysis features
Anti-analysis features in phishing pages – especially in those, which threat actors send out as e-mail attachments – are nothing new[1,2]. Nevertheless, sometimes the way that these mechanisms are implemented may still leave one somewhat mystified. This has happened to me a few weeks ago when I found what appeared to be a generic phishing message in one of my spam traps.
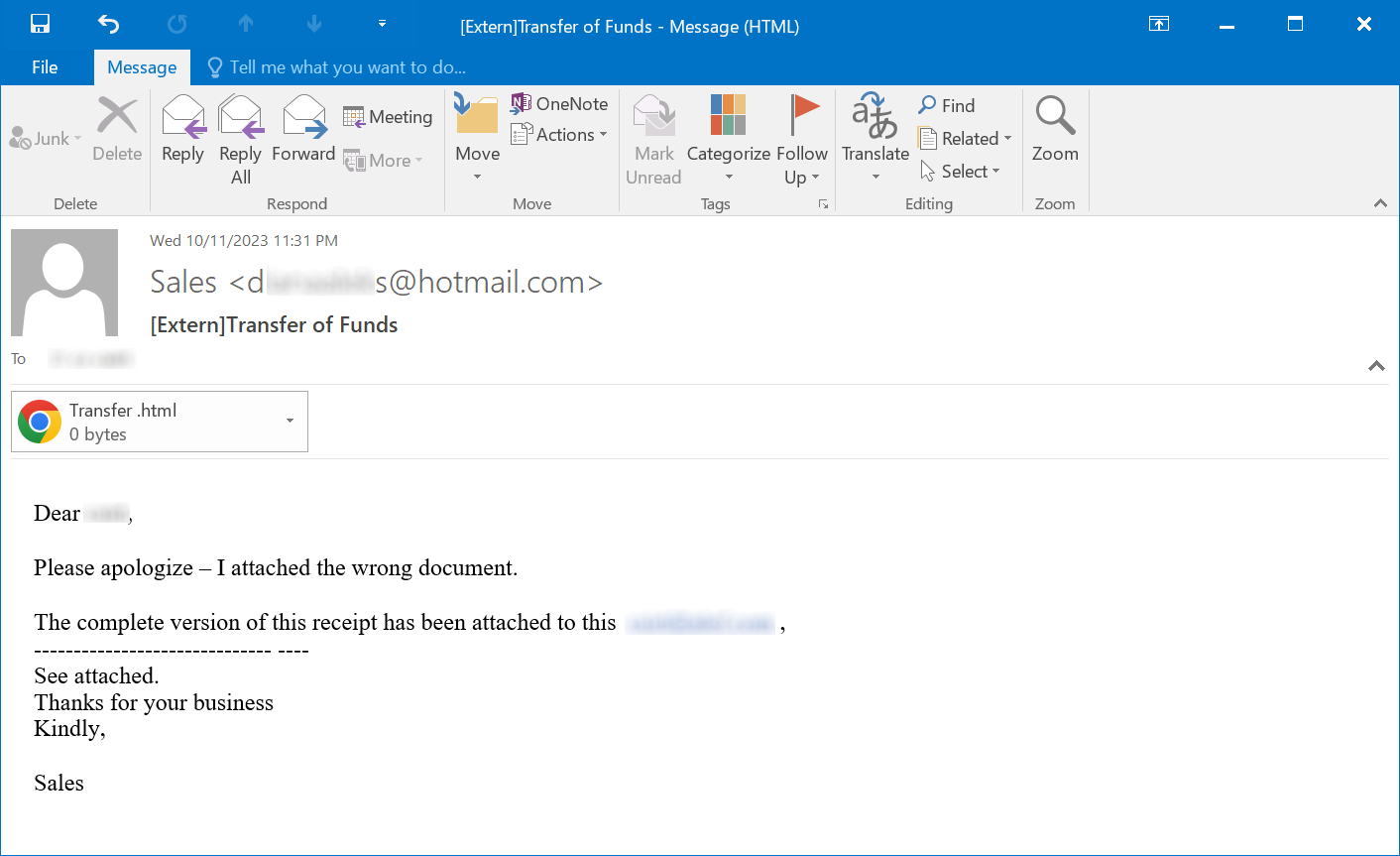
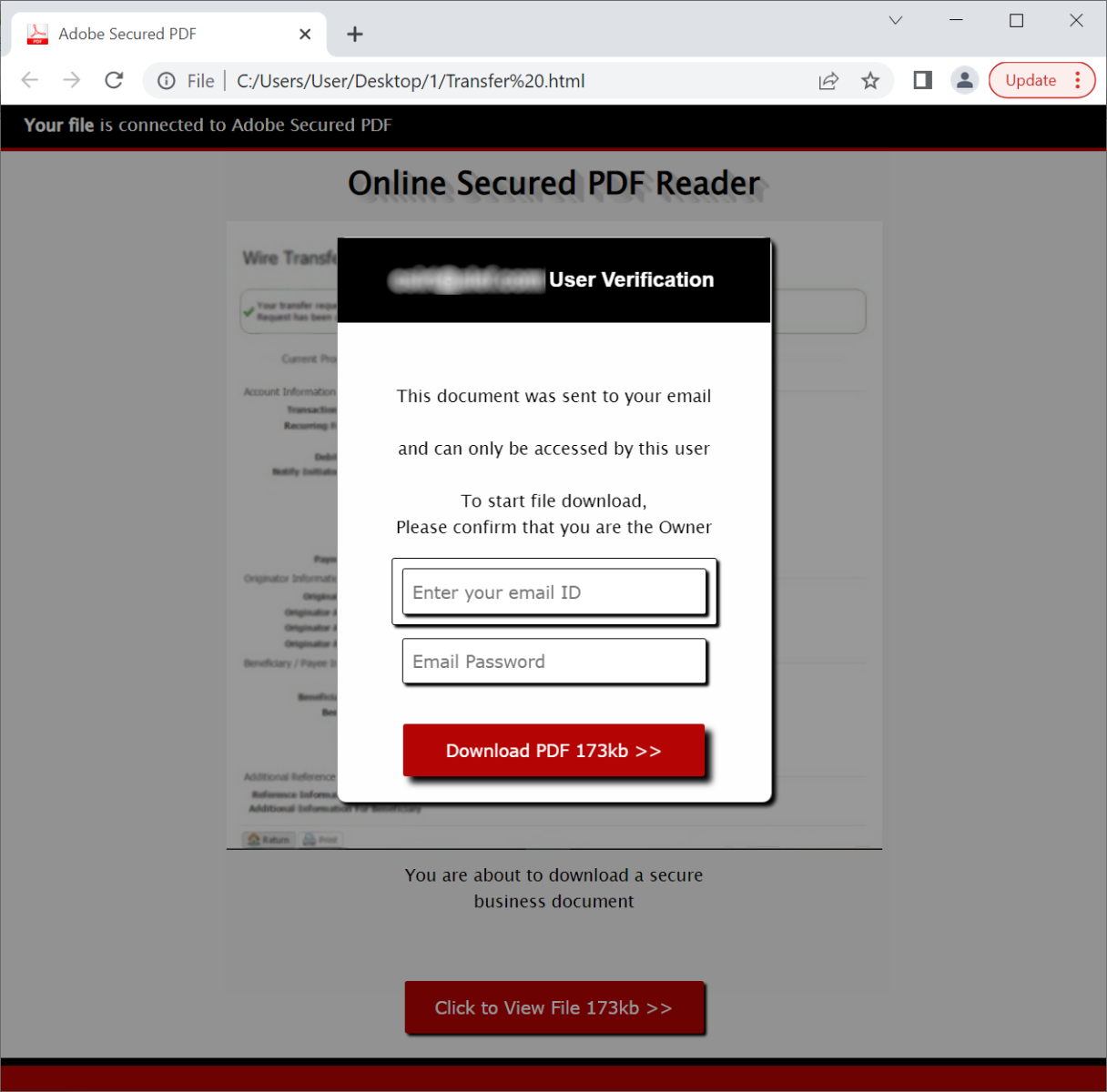
After opening the attachment in a text editor, I was expecting to see either obfuscated or clear text HTML and JavaScript code, intended to display a fake login form, which would send any credentials that one might input to an attacker-controlled server, since this is what HTML phishing attachments usually contain.
In this, I was not wrong, as the attachment did, indeed, contain a fake login form.
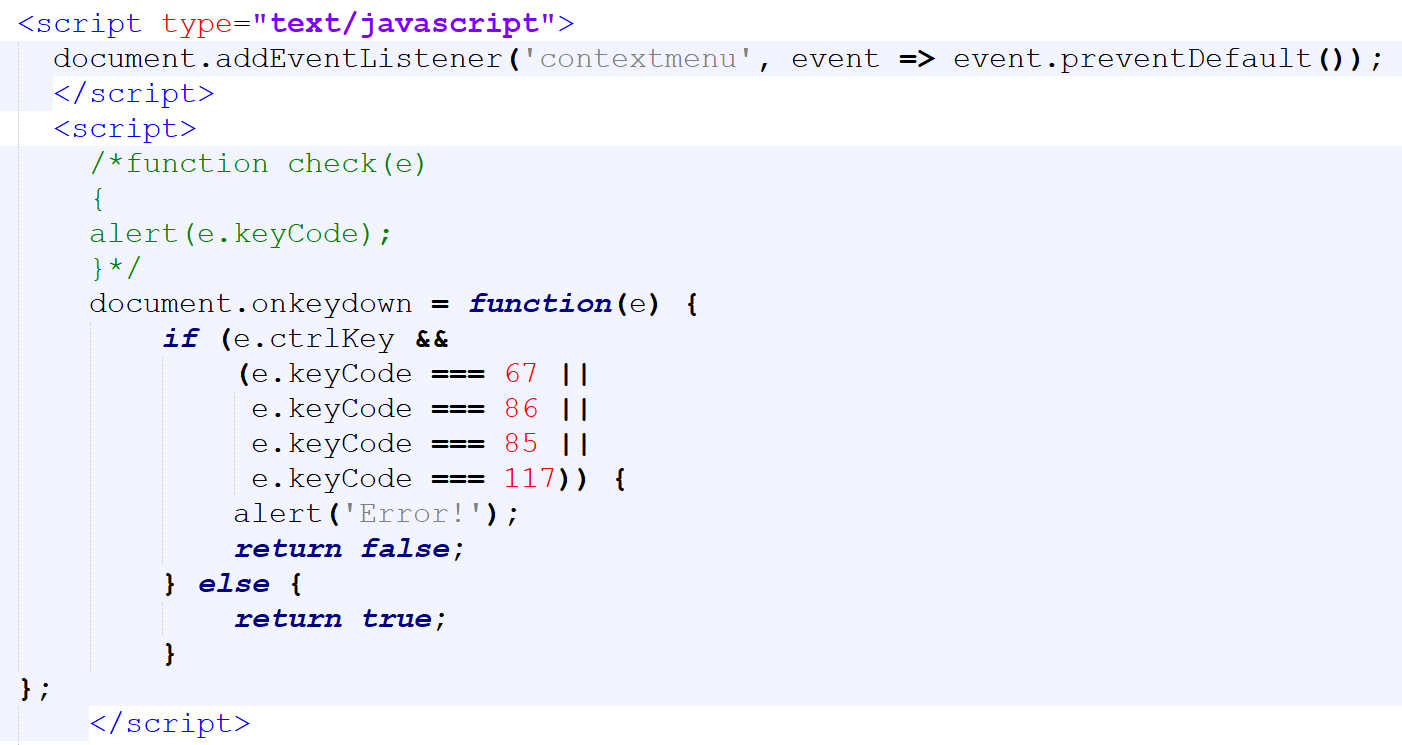
Nevertheless, while I was going through the HTML code (which was not obfuscated in any way), before I viewed it in a browser, my eye was caught by an unexpected piece of JavaScript code.
JavaScript in the first tag serves to prevent a context menu from being displayed when one clicks a page with the right mouse button. And script in the second tag effectively blocks the use of shortcuts ctrl+c, ctrl+v and ctrl+u.
Since the last shortcut mentioned is used in modern browsers to display the source code of a web page, my thinking is that blocking ctrl+c is in fact intended to prevent the use of ctrl+shift+c, which is commonly used to display developer tools.
Both of these scripts certainly do work, and if one were to open the phishing attachment in a browser, they would block the ability to view the source code or open developer tools, however, as far as their anti-analysis effect goes, they can be trivially bypassed by simply saving the page and opening it in a text editor, as I have done…
This, as I mentioned before, has left me somewhat mystified. My thinking is that if any recipient was suspicious enough to want to view a source code of a HTML page, they would be unlikely to input their credentials in it in any case (perhaps especially if the page didn’t behave in the usual manner). And, as we have shown, for preventing any more "advanced" analysis attempts, these scripts are pretty much useless. Therefore, although this approach is certainly interesting, it is also somewhat arbitrary and ineffective, which means that we can be fairly sure that it won’t be the “next big thing” when it comes to phishing.
[1] https://isc.sans.edu/diary/Phishing+with+a+selfcontained+credentialsstealing+webpage/25580
[2] https://isc.sans.edu/diary/HTML+phishing+attachments+now+with+antianalysis+features/28702
-----------
Jan Kopriva
@jk0pr
Nettles Consulting


Comments