PE files and debug info
Windows executables (PE files) can contain debug information, like the absolute pathname of the PDB file. A PDB file (Program DataBase) contains debug information and is produced by the linker.
This PDB pathname can be used as an IOC. Parts of the PDB pathname can be used as IOCs too. For example, if the project is stored in the user profile, the path will contain the username. I've successfully used this to track malware created by actors.
Extracting the PDB pathname can be as simple as grepping for string .pdb:
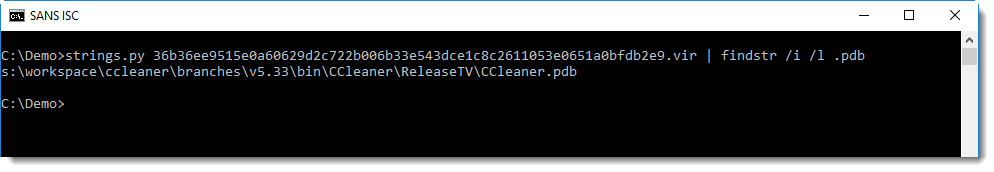
You can also open the PE file in a hex editor, and search for RSDS:
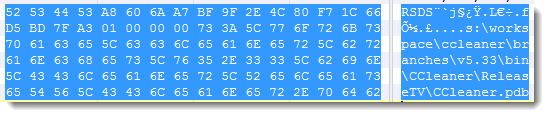
PE file parsers like pecheck.py can extract and parse this codeview information:
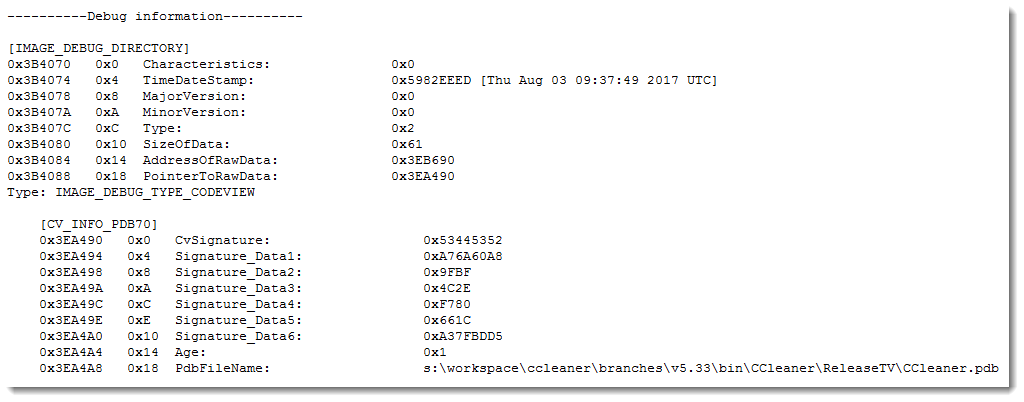
The structure starts with signature RSDS (0x53445352), is followed by a GUID (16 bytes), a counter (4 bytes) and then the PDB pathname.
This unique GUID can be found in the PDB file too, and creates a unique link between the PE file and the PDB file.
Didier Stevens
Microsoft MVP Consumer Security
blog.DidierStevens.com DidierStevensLabs.com


Comments