Malware Sample Delivered Through UDF Image
I found an interesting phishing email which was delivered with a malicious attachment: an UDF image (.img). UDF means “Universal Disk Format” and, as said by Wikipedia[1], is an open vendor-neutral file system for computer data storage. It has supplented the well-known ISO 9660 format (used for burning CD & DVD) that was also used in previous campaign to deliver malicious files[2].
Here is a copy of the mail:
From: <redacted> To: <redacted> Subject: Overdue Invoice Valued customer, Attached is your invoice as scheduled, your credit/debit card will be charged. Your bill will be delivered along with your ordered items(s). Please review the receipt at your earliest convenience and get back to us in case of anomalies. Thank you for your continued patronage. Warm regards.
The attached files was called "invoice#003.img" with the SHA256 hash: 886338ebc04e728338874b07365d4fd337998e1786893b680065358e815a6d02. At the moment, the file is flagged by 23 AV on Virustotal[3]. To read the content of the archive safely, you can use the ‘loop’ driver on a Linux system:
# mount -o loop /tmp/invoice\#003.img /mnt/malicious/ # ls -l /mnt/malicious total 1296 -r-xr-xr-x 1 nobody nogroup 1325568 Apr 14 23:45 invoice#003.exe # shasum -a 256 /tmp/malicious/invoice* b3aef0e1d7a71edbc858a81e66f354be1974aafdd4449f2972e4dae1c82f2b8a /mnt/malicious/invoice#003.exe
Here, the VT score is 35[4], it’s a classic malware written in AutoIT, nothing special. It tries to connect to kingdevil[.]ddns[.]net:4156.
Let’s have a look at the UDF image:
00008220: 2020 2020 2020 2020 2020 2020 2020 2020 00008230: 2020 2020 2020 2020 2020 2020 2020 494d IM 00008240: 4742 5552 4e20 5632 2e35 2e38 2e30 202d GBURN V2.5.8.0 - 00008250: 2054 4845 2055 4c54 494d 4154 4520 494d THE ULTIMATE IM 00008260: 4147 4520 4255 524e 4552 2120 2020 2020 AGE BURNER! 00008270: 2020 2020 2020 2020 2020 2020 2020 2020 00008280: 2020 2020 2020 2020 2020 2020 2020 2020 00008290: 2020 2020 2020 2020 2020 2020 2020 2020 000082a0: 2020 2020 2020 2020 2020 2020 2020 2020 000082b0: 2020 2020 2020 2020 2020 2020 2020 2020 000082c0: 2020 2020 2020 2020 2020 2020 2020 2020 000082d0: 2020 2020 2020 2020 2020 2020 2020 2020 000082e0: 2020 2020 2020 2020 2020 2020 2020 2020 000082f0: 2020 2020 2020 2020 2020 2020 2020 2020 00008300: 2020 2020 2020 2020 2020 2020 2020 2020 00008310: 2020 2020 2020 2020 2020 2020 2020 2020 00008320: 2020 2020 2020 2020 2020 2020 2032 3031 201 00008330: 3930 3431 3530 3034 3635 3430 300c 3230 9041500465400.20 00008340: 3139 3034 3135 3030 3436 3534 3030 0c30 19041500465400.0 00008350: 3030 3030 3030 3030 3030 3030 3030 3000 000000000000000. 00008360: 3030 3030 3030 3030 3030 3030 3030 3030 0000000000000000 00008370: 0001 0049 6d67 4275 726e 2076 322e 352e ...ImgBurn v2.5. 00008380: 382e 3000 0000 0000 0000 0000 0000 0000 8.0.............
ImgBurn is a well-known Windows tool used to create CD/DVD images[5] and guess what? A stock Windows handle this type of file without any extra tool:
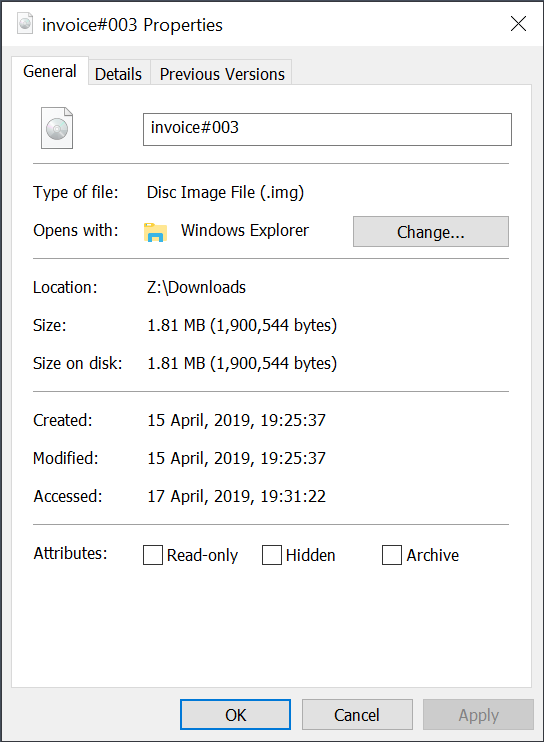
So be careful with .img files! They should also be added to the list of prohibited file extensions in your mail relays or change the file association in your Windows environments to NOT open them Windowd Explorer.
[1] https://en.wikipedia.org/wiki/Universal_Disk_Format
[2] https://isc.sans.edu/forums/diary/Malicious+iso+Attachments/22636
[3] https://www.virustotal.com/#/file/886338ebc04e728338874b07365d4fd337998e1786893b680065358e815a6d02/relations
[4] https://www.virustotal.com/#/file/b3aef0e1d7a71edbc858a81e66f354be1974aafdd4449f2972e4dae1c82f2b8a/detection
[5] https://www.imgburn.com
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments
Anonymous
Apr 18th 2019
6 years ago