Keeping an Eye on Tor Traffic
Do you know the amount of Tor traffic hitting your network? Do you know what people are doing from this anonymized network? Most IDS solutions have built-in rules to report traffic generated from/to Tor exit nodes. This is a common event triggered by rules like this one (from the Emerging Threats feed):
alert ip [185.97.32.18,186.212.145.191,187.20.170.159,188.120.231.199,188.126.81.155,188.129.46.116,188.138.1.217,188.138.9.41,188.138.9.49,188.209.52.109] any -> $HOME_NET any (msg:"ET TOR Known Tor Exit Node Traffic group 29"; reference:url,doc.emergingthreats.net/bin/view/Main/TorRules; threshold: type limit, track by_src, seconds 60, count 1; classtype:misc-attack; flowbits:set,ET.TorIP; sid:2520056; rev:2583;)
This is very interesting to know when some traffic is coming (or leaving) your infrastructure from the Tor network. Tor traffic can be completely legit (more and more people take care of their privacy) but it can also be a sign of reconnaissance or ongoing attack from bad guys. IDS are usually deployed behind firewalls (internal side) and do not see the traffic dropped by the firewall. The dropped traffic has a real value from a security point of view. If most “next-generation” firewalls are able to detect Tor traffic, they do not report the traffic from/to Tor exit nodes by default. I was curious to know how my own infrastructure was reached by such hosts. It means many public resources, servers, VPS and my home network. How to achieve this? I performed this with Splunk but the same is easily doable within other log management solutions like the ELK stack or SIEM products.
The first step is to get a list of the Tor nodes. This list is changing all the time and sites provide this data for free. I’m using: https://www.dan.me.uk/torlist/?exit.
Keep in mind that for performance reason, you are rate-limited (no need to fetch the list every x minutes). In my case I setup an hourly cron job that generates a CSV file:
#!/bin/bash URL='https://www.dan.me.uk/torlist/?exit' OUTPUT='/opt/splunk/var/run/splunk/tor_exit_nodes.csv' echo "src_ip,desc" >$OUTPUT wget -O - "$URL" 2>/dev/null | while read L do echo $L,TorExitNode >>$OUTPUT done
Note: I add a second field “desc” with a default value “TorExitNode” to be able to perform the lookup in Splunk.
The next step is to configure Splunk and create a lookup table to search for IP addresses from the CSV files. With the huge amount of IP addresses in the CSV, I decided to use a KV (keyword-value lookup table) to speed up searches. Have a look at the Splunk documentation for details. Now we can use the lookup table and start searching for Tor exit nodes which hit my firewalls. This is achieve using the following query:
index=firewall | dedup src_ip | lookup tor_exit_nodes src_ip | where desc="TorExitNode"
For the last 24 hours, it reported 53 unique Tor exit nodes:

Here is an overview of hits per exit node:
index=firewall | lookup tor_exit_nodes src_ip | where desc="TorExitNode"| stats count by src_ip
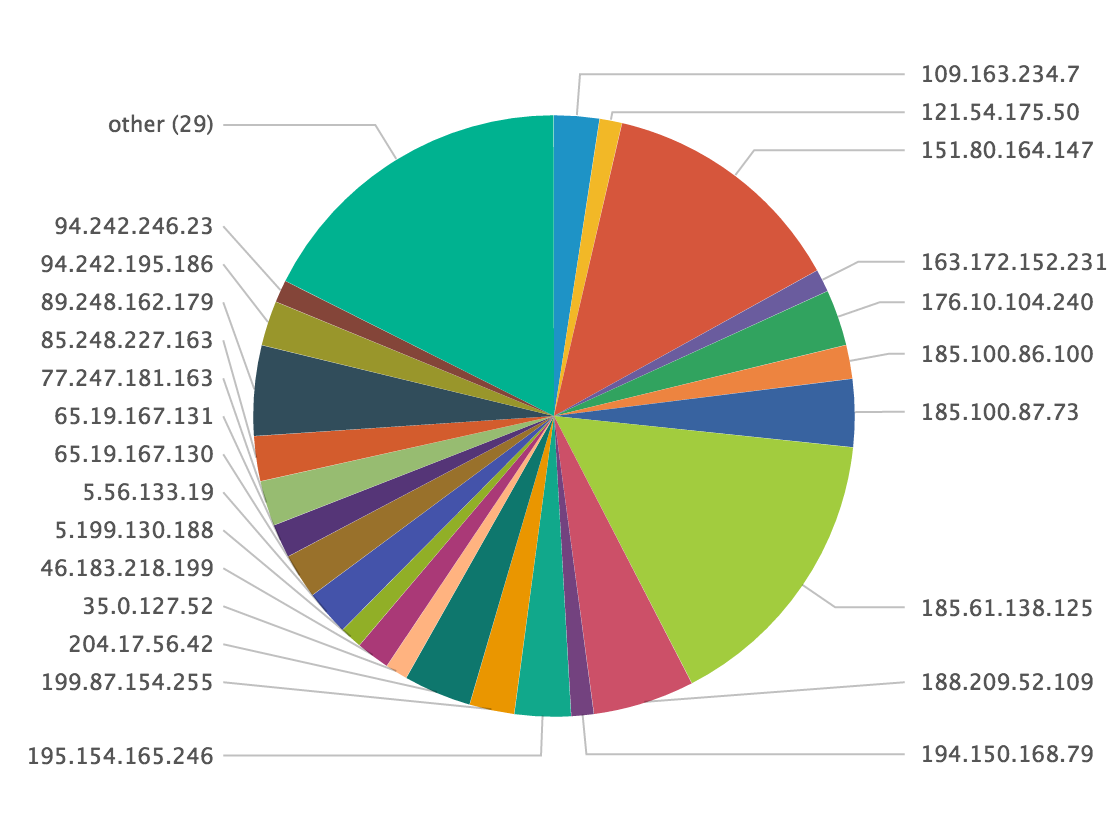
Where are located these nodes?
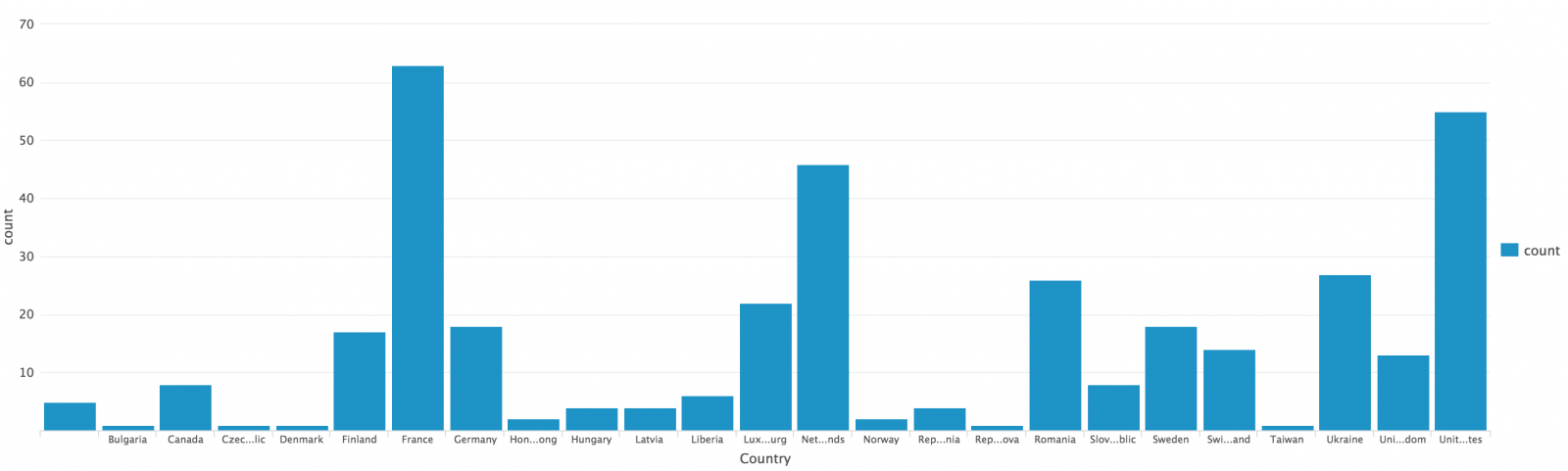
index=firewall | lookup tor_exit_nodes src_ip | where desc="TorExitNode"| iplocation src_ip | stats count by Country
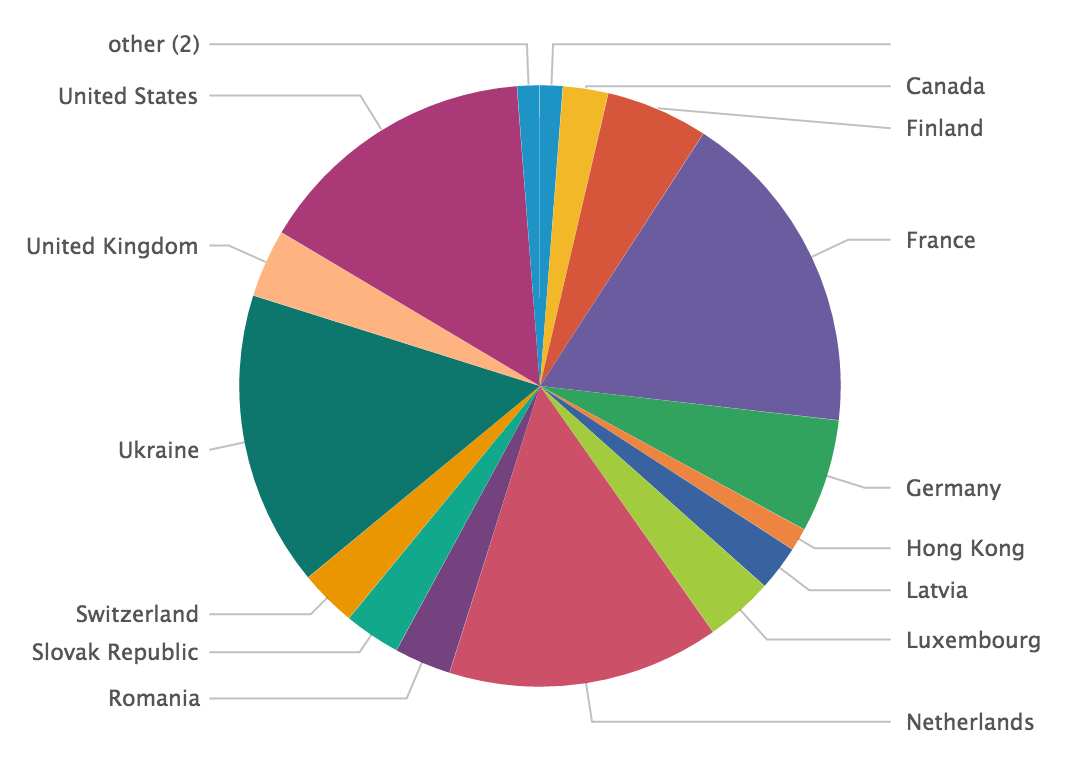
Over 30 days, I got traffic from many countries. I was surprised to see France in top position:
And finally, more important: which ports are probed?
index=firewall | lookup tor_exit_nodes src_ip | where desc="TorExitNode"| stats count by dest_port
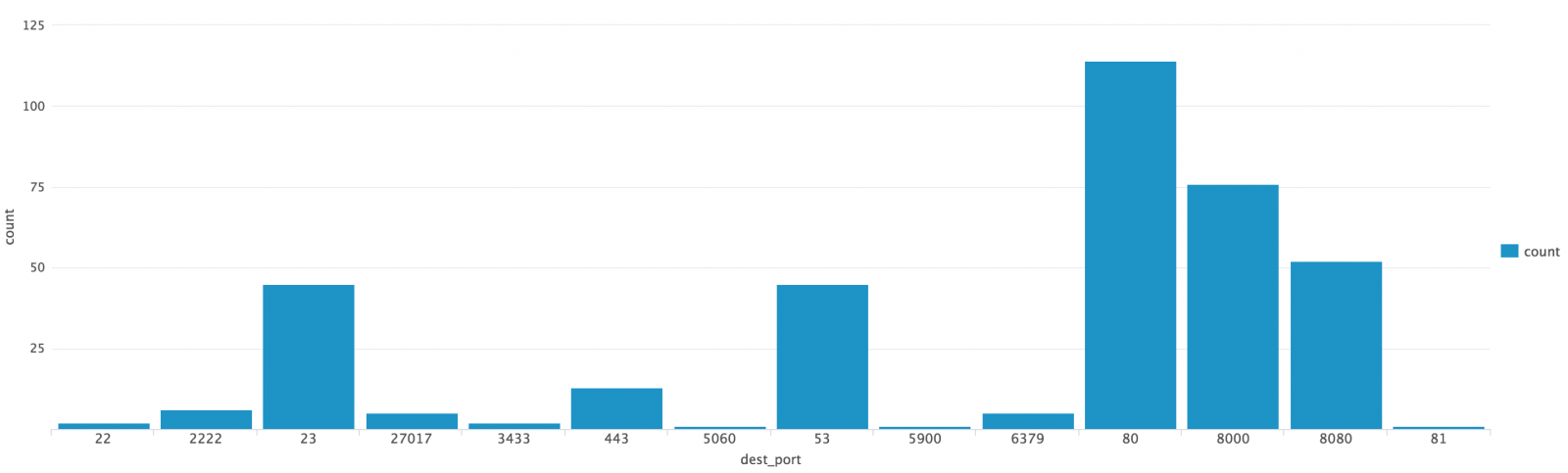
Based on the graph, we can see that the traffic is mainly reconnaissance: ssh ports / telnet and web services. A special mention for VNC (5900) and SIP (5060)!
Finally, we can get info about a specific protocol (ex: HTTP). Here we see all HTTP errors (code > 200):
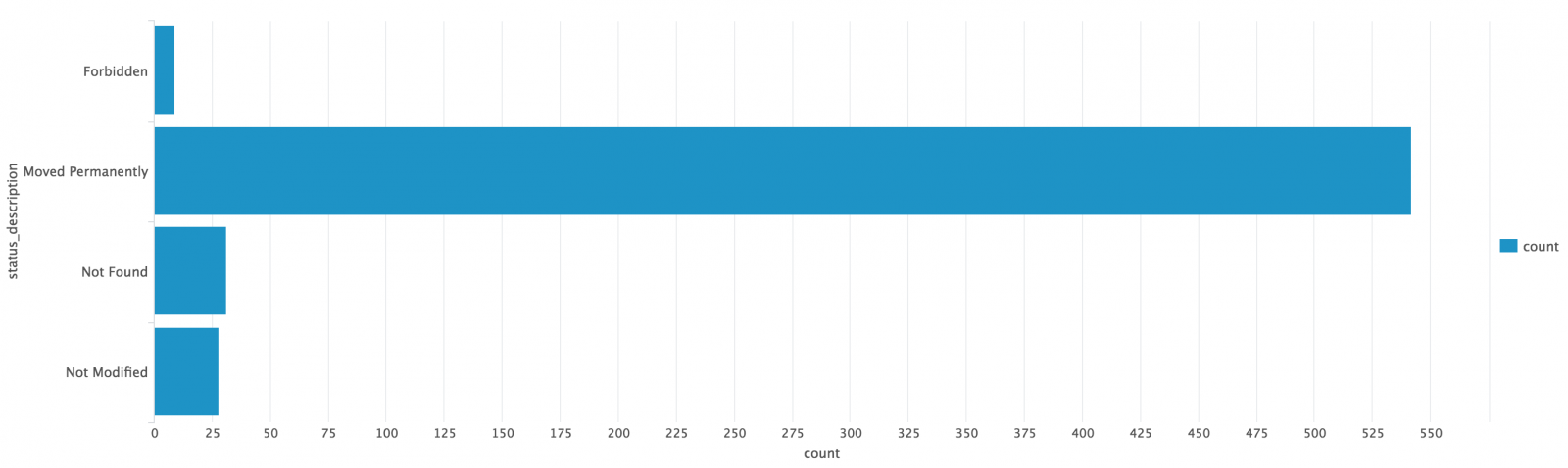
You can imagine plenty of useful queries to get extra values from your logs. If your web server is scanned, something weird may occur but it it's performed from Tor, you can increase the incident level.
My next class:
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |
×
![modal content]()
Diary Archives


Comments
Anonymous
May 26th 2016
9 years ago
Last year, the same kind of approach was explained: How to integrate the DShield Top-20 in a Palo Alto Networks firewall:
https://isc.sans.edu/forums/diary/Subscribing+to+the+DShield+Top+20+on+a+Palo+Alto+Networks+Firewall/19365/
Anonymous
May 26th 2016
9 years ago
Anonymous
May 27th 2016
9 years ago