Jaff ransomware gets a makeover
Introduction
Since 2017-05-11, a new ransomware named "Jaff" has been distributed through malicious spam (malspam) from the Necurs botnet. This malspam uses PDF attachments with embedded Word documents containing malicious macros. Victims must open the PDF attachment, agree to open the embedded Word document, then enable macros on the embedded Word document to infect their Windows computers.
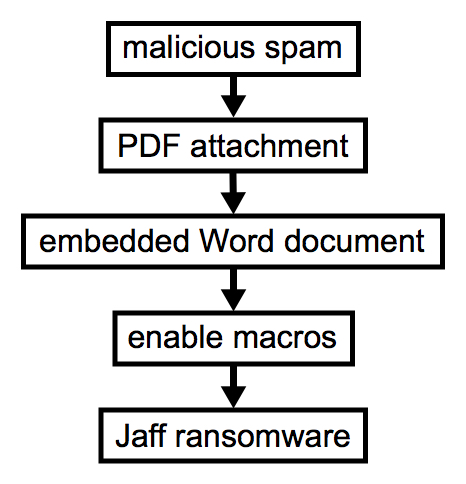
Shown above: Flow chart for this infection chain.
Prior to Jaff, we've seen waves of malspam using the same PDF attachment/embedded Word doc scheme to push Locky ransomware. Prior to that, this type of malspam was pushing Dridex.
With all the recent news about WannaCry ransomware, people might forget Jaff is an ongoing threat. Worse yet, some people might not know about it at all since its debut about 2 weeks ago. Jaff has already gotten a makeover, so an infected host looks noticeably different now. With that in mind, today's diary reviews a wave of malspam pushing Jaff ransomware from Tuesday 2017-05-23.
The emails
This specific wave of malspam used a fake invoice theme. It started on Tuesday 2017-05-23 as early as 13:22 UTC and lasted until sometime after 20:00 UTC. I collected 20 emails for today's diary.
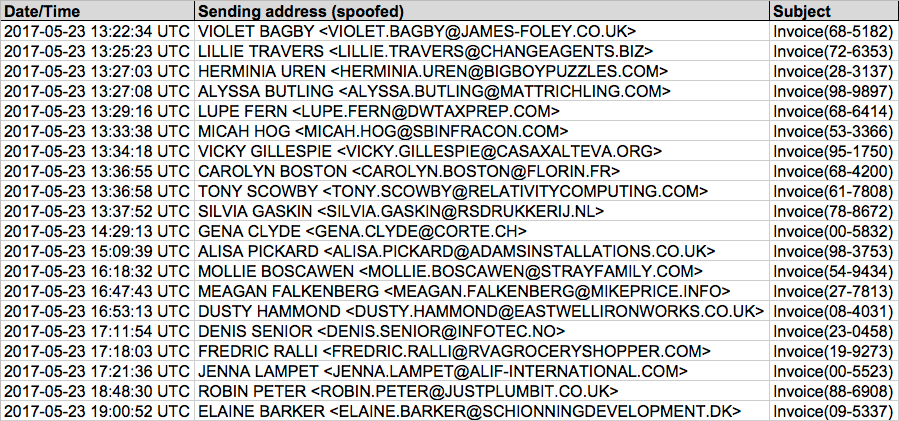
Shown above: Image from the spreadsheet tracker for this malspam (1 of 2).
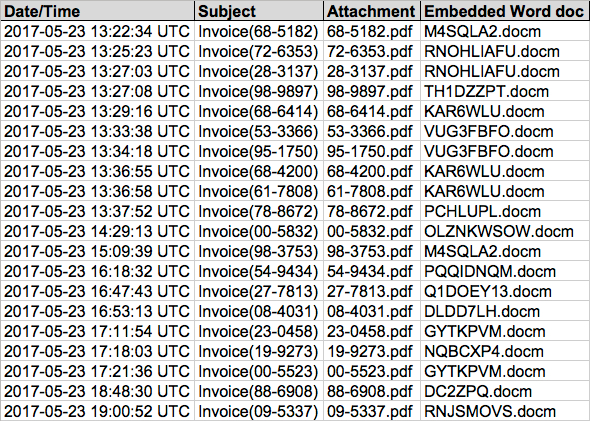
Shown above: Image from the spreadsheet tracker for this malspam (2 of 2).
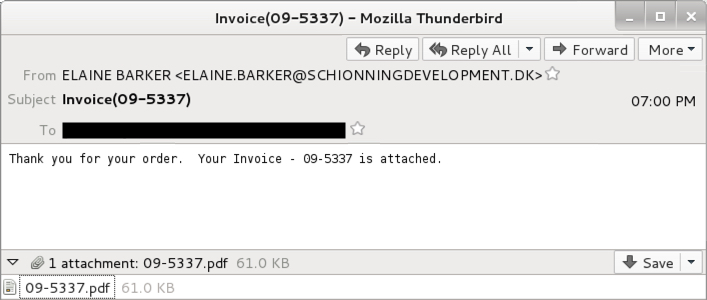
Shown above: Screenshot from one of the emails.
As stated earlier, these emails all have PDF attachments, and each one contains an embedded Word document. The Word document contains malicious macros designed to infect a Windows computer.
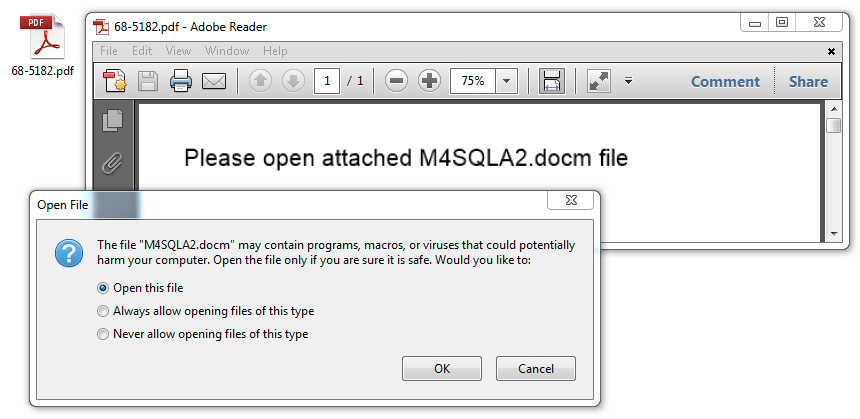
Shown above: Opening one of the PDF attachments reveals an embedded Word document.
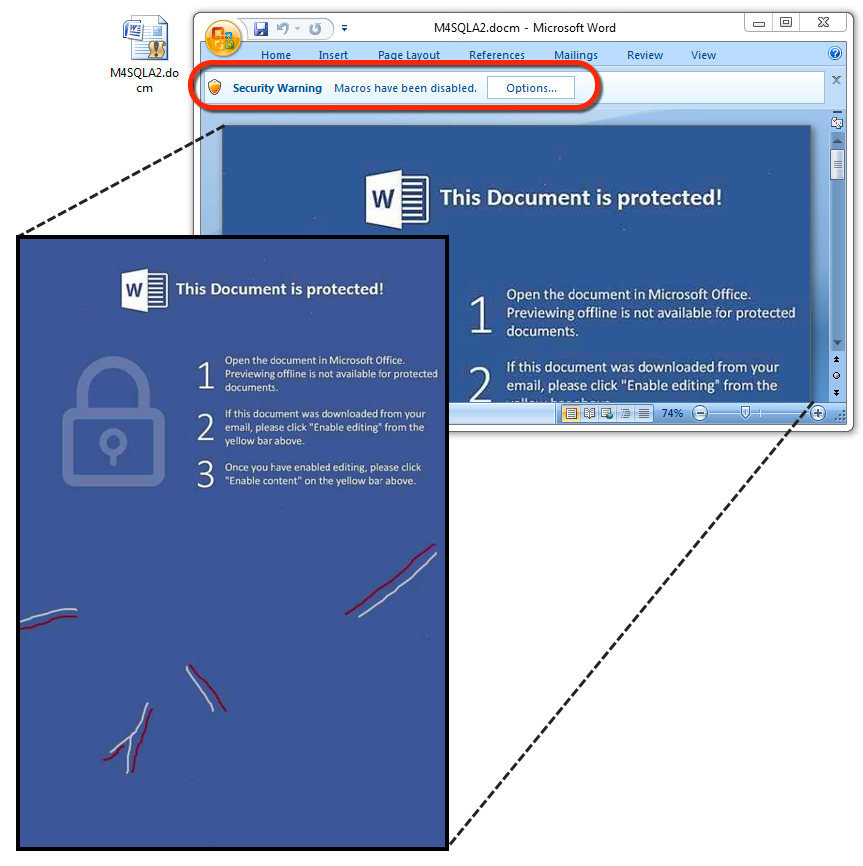
Shown above: The embedded Word document with malicious macros.
The traffic
Follow the entire infection chain, and you'll see minimal network traffic compared to other types of malware. The Word macros generate an initial URL to download an encoded Jaff binary, then we see one other URL for post-infection callback from an infected host. The initial HTTP request for Jaff returns an encoded binary that's been XORed with the ASCII string I6cqcYo7wQ. Post-infection traffic merely returns the string "Created" from the server after an infected host checks in.
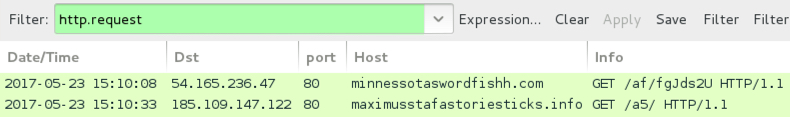
Shown above: Pcap from an infection filtered in Wireshark.

Shown above: Encoded binary for Jaff ransomware retrieved by the Word macros.
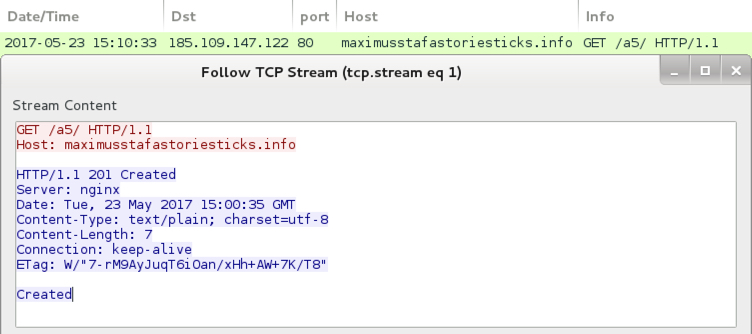
Shown above: Post-infection traffic from an infected host.
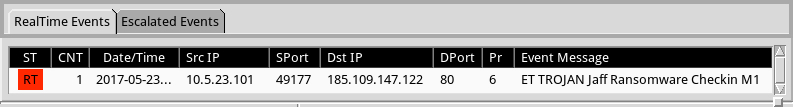
Shown above: Alerts on the traffic using Security Onion with Suricata and the EmergingThreats Open ruleset.
The infected Windows host
The encoded binary from this wave of malspam was stored to the user's AppData\Local\Temp directory as lodockap8. Then it was decoded and stored as levinsky8.exe in the same directory. These file names change every day with each new wave of malspam.
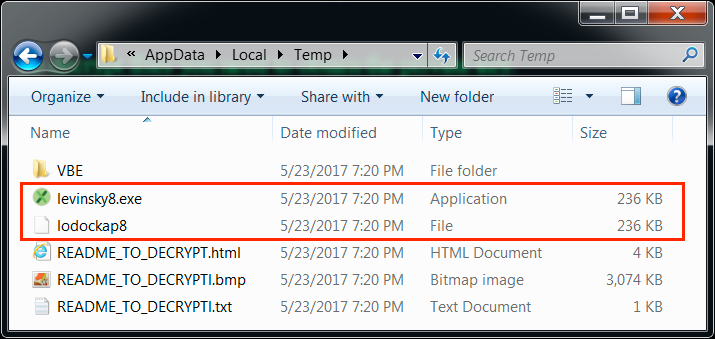
Shown above: The user's AppData\Local\Temp directory from an infected host on 2017-05-23.
On Tuesday 2017-05-23, Jaff ransomware had a makeover. Prior to that, an infected Windows host looked like this:
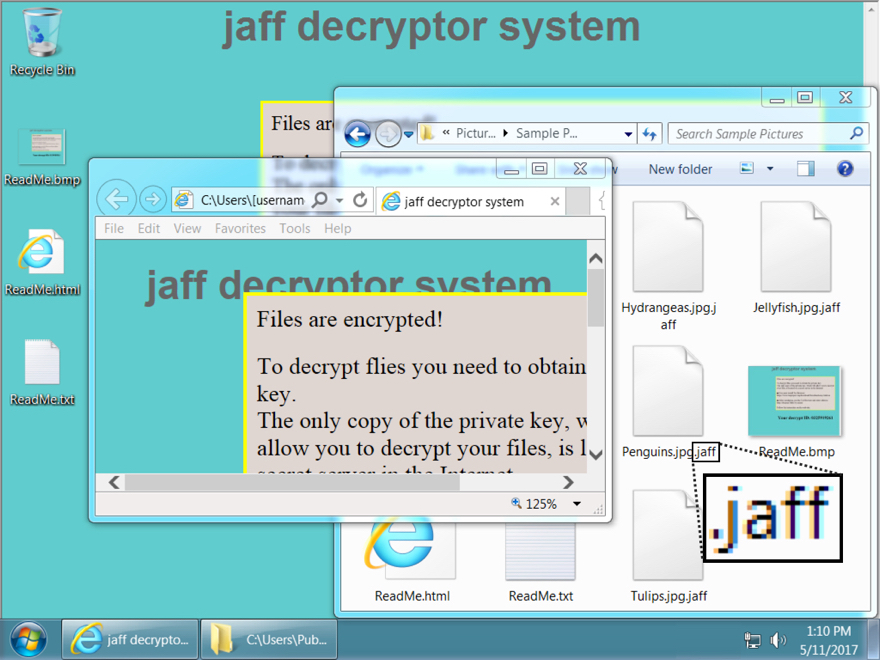
Shown above: Desktop of a Windows host infected with a Jaff ransomware sample before 2017-05-23.
The Windows host infected with a Jaff ransomware sample I saw on 2017-05-23 looked like this:
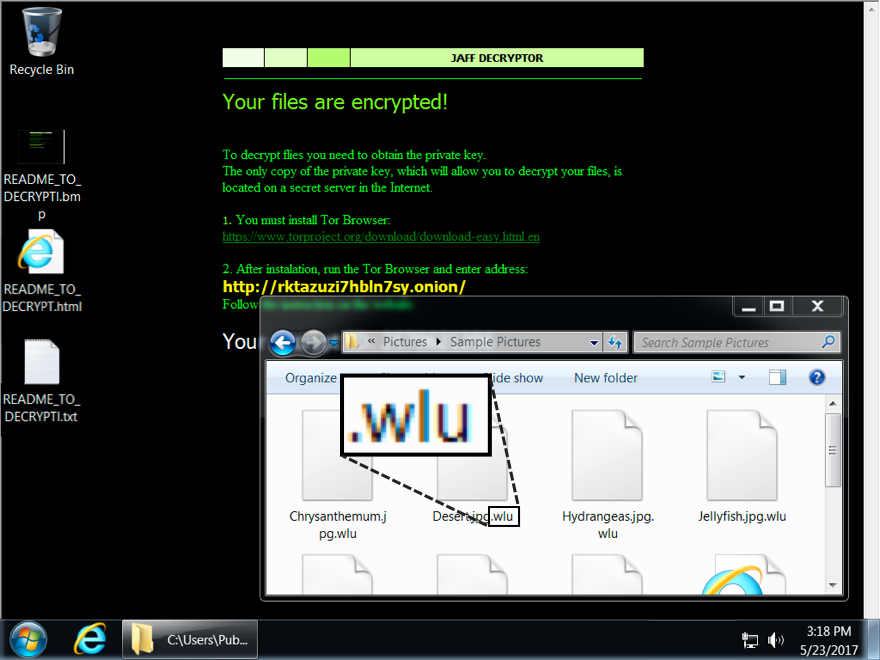
Shown above: Desktop of a Windows host infected with a Jaff ransomware sample from 2017-05-23.
Encrypted files had been previously appended with the .jaff file extension. On Tuesday 2017-05-23, encrypted files from my infected host were appended with a .wlu file extension. My infected host asked for 0.35630347 bitcoin as a ransom payment.
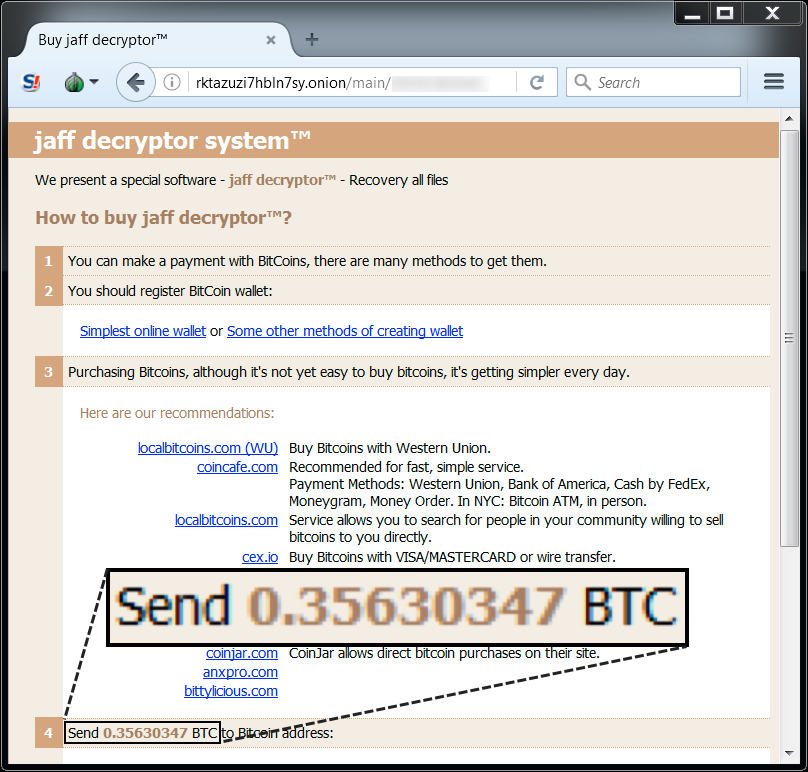
Shown above: Jaff decryptor from a Windows host infected on 2017-05-23.
Indicators of Compromise (IoCs)
The following are examples of email subject lines and attachment names from Tuesday 2017-05-23:
- Subject: Invoice(00-5523) -- Attachment name: 68-5182.pdf
- Subject: Invoice(00-5832) -- Attachment name: 72-6353.pdf
- Subject: Invoice(08-4031) -- Attachment name: 28-3137.pdf
- Subject: Invoice(09-5337) -- Attachment name: 98-9897.pdf
- Subject: Invoice(19-9273) -- Attachment name: 68-6414.pdf
- Subject: Invoice(23-0458) -- Attachment name: 53-3366.pdf
- Subject: Invoice(27-7813) -- Attachment name: 95-1750.pdf
- Subject: Invoice(28-3137) -- Attachment name: 68-4200.pdf
- Subject: Invoice(53-3366) -- Attachment name: 61-7808.pdf
- Subject: Invoice(54-9434) -- Attachment name: 78-8672.pdf
- Subject: Invoice(61-7808) -- Attachment name: 00-5832.pdf
- Subject: Invoice(68-4200) -- Attachment name: 98-3753.pdf
- Subject: Invoice(68-5182) -- Attachment name: 54-9434.pdf
- Subject: Invoice(68-6414) -- Attachment name: 27-7813.pdf
- Subject: Invoice(72-6353) -- Attachment name: 08-4031.pdf
- Subject: Invoice(78-8672) -- Attachment name: 23-0458.pdf
- Subject: Invoice(88-6908) -- Attachment name: 19-9273.pdf
- Subject: Invoice(95-1750) -- Attachment name: 00-5523.pdf
- Subject: Invoice(98-3753) -- Attachment name: 88-6908.pdf
- Subject: Invoice(98-9897) -- Attachment name: 09-5337.pdf
The following are examples of spoofed email senders from Tuesday 2017-05-23:
- ALISA PICKARD <ALISA.PICKARD@ADAMSINSTALLATIONS.CO.UK>
- ALYSSA BUTLING <ALYSSA.BUTLING@MATTRICHLING.COM>
- CAROLYN BOSTON <CAROLYN.BOSTON@FLORIN.FR>
- DENIS SENIOR <DENIS.SENIOR@INFOTEC.NO>
- DUSTY HAMMOND <DUSTY.HAMMOND@EASTWELLIRONWORKS.CO.UK>
- ELAINE BARKER <ELAINE.BARKER@SCHIONNINGDEVELOPMENT.DK>
- FREDRIC RALLI <FREDRIC.RALLI@RVAGROCERYSHOPPER.COM>
- GENA CLYDE <GENA.CLYDE@CORTE.CH>
- HERMINIA UREN <HERMINIA.UREN@BIGBOYPUZZLES.COM>
- JENNA LAMPET <JENNA.LAMPET@ALIF-INTERNATIONAL.COM>
- LILLIE TRAVERS <LILLIE.TRAVERS@CHANGEAGENTS.BIZ>
- LUPE FERN <LUPE.FERN@DWTAXPREP.COM>
- MEAGAN FALKENBERG <MEAGAN.FALKENBERG@MIKEPRICE.INFO>
- MICAH HOG <MICAH.HOG@SBINFRACON.COM>
- MOLLIE BOSCAWEN <MOLLIE.BOSCAWEN@STRAYFAMILY.COM>
- ROBIN PETER <ROBIN.PETER@JUSTPLUMBIT.CO.UK>
- SILVIA GASKIN <SILVIA.GASKIN@RSDRUKKERIJ.NL>
- TONY SCOWBY <TONY.SCOWBY@RELATIVITYCOMPUTING.COM>
- VICKY GILLESPIE <VICKY.GILLESPIE@CASAXALTEVA.ORG>
- VIOLET BAGBY <VIOLET.BAGBY@JAMES-FOLEY.CO.UK>
The following are examples of SHA256 hashes for the PDF attachments from Tuesday 2017-05-23:
- 0218178eec35acad7909a413d94d84ae3d465a6ea37e932093ec4c7a9b6a7394
- 0a326eb9a416f039be104bb5f199b7f3442515f88bd5c7ad1492b1721c174b8e
- 21da9eeded9581f6f032dea0f21b45aa096b0330ddacbb8a7a3942a2026cc8ca
- 4458f43127bb514b19c45e086d48aba34bf31baf1793e3d0611897c2ff591843
- 66320f4e85e3d6bd46cf00da43ca421e4d50c2218cb57238abb2fb93bef37311
- 7dd248652f2b42f3e1ad828e686c8ba458b6bb5b06cea46606ceccdd6b6e823c
- 8a474cdd4c03dd4a6ba6ad8945bf22f74f2f41830203f846d5437f02292bb037
- 956e43ece563fd46e6995fae75a0015559f0a63af5059290a40c64b906be5b9b
- 9beb67a68396375f14099055b712e22673c9a1d307a76125186127e289ab41a2
- b2b9c02080ae6fbe1845c779e31b5f6014ec20db74d21bd9dd02c444a0d0dd9b
- c126e731c1c43d52b52a44567de45796147aca1b331567ed706bf21b6be936b4
- cde2ff070e86bc1d72642cb3a48299080395f1df554e948fd6e8522579dfe861
- daf01a1f7e34e0d47ecdfcef5d27b2f7a8b096b4e6bc67fb805d4da59b932411
- e477300e8f8954ee95451425035c7994b984d8bc1f77b4ccf2a982bb980806fe
The following are examples of SHA256 hashes and file names for the embedded word documents from Tuesday 2017-05-23:
- 084ee31e69053e66fafe6e1c2a69ffec015f95801ce6020f7765c56d6f3c23ff - PQQIDNQM.docm
- 0855061389b62ec6a9b95552357ff7571ae5c034b304978a533c6cba06c3f9e8 - GYTKPVM.docm
- 1f2598dc7a7b8f84307d8c2fa41f5550c320f8192cd41e50b47570d3836e6fcc - RNJSMOVS.docm
- 2dbf9e1c412aa1ffd32a91043642eb9cc80772c87dbbce3dd098c57d917277fb - DLDD7LH.docm
- 3f95a7eeb1965193a4e92862c10897e04708b37b793b8e45f890d019358214c0 - DC2ZPQ.docm
- 56cd249ff82e9bb96a73262090bc6a299ead64d6c75161520e745c2066f22430 - KAR6WLU.docm
- 795d8312749c122fa10a93c9f3aa1c0f4ffc081714c0ddb66c141334f8ef0633 - M4SQLA2.docm
- 8906d10a48487d8240bddd0c0cb5c076e88104c86bdf871b0143d74b6df3cc98 - NQBCXP4.docm
- 91aa966e837c4144a1294aa912a2162397f3a6df98cf336891d234e267cd919f - RNOHLIAFU.docm
- 933fcc1bf90716abf7c4eaf29b520d2276df895fb4dd5a76be2a55028a4da94e - PCHLUPL.docm
- a98782bd10004bef221e58abcecc0de81747e97910b8bbaabfa0b6b30a93b66b - Q1DOEY13.docm
- ae244ca170b6ddc285da0598d9e108713b738034119bae09eaa69b0c5d7635f8 - TH1DZZPT.docm
- bc0b2fbe4225e544c6c9935171a7d6162bc611a82d0c6a5f3d62a3f5df71cf8c - OLZNKWSOW.docm
- c702deaa2fe03f188a670d46401e7db71628e74b0e5e2718a19e2944282e05cd - VUG3FBFO.docm
The following is the sample of Jaff ransomware I saw on Tuesday 2017-05-23:
- SHA256 hash: 557306dc8005f9f6891939b5ceceb35a82efbe11bd1dede755d513fe6b5ac835
- File size: 241,664 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\levinsky8.exe
The following are URLs generated by malicious macros from the embedded Word documents. They're used to download the encoded Jaff ransomware binary:
- billiginurlaub.com - GET /fgJds2U
- david-faber.de - GET /fgJds2U
- elateplaza.com - GET /fgJds2U
- electron-trade.ru - GET /fgJds2U
- fjjslyw.com - GET /fgJds2U
- hr991.com - GET /fgJds2U
- jinyuxuan.de - GET /fgJds2U
- khaosoklake.com - GET /fgJds2U
- minnessotaswordfishh.com - GET /af/fgJds2U
- oliverkuo.com.au - GET /fgJds2U
- pcflame.com.au - GET /fgJds2U
- tdtuusula.com - GET /fgJds2U
- williams-fitness.com - GET /fgJds2U
The following is post-infection traffic from my infected Windows host:
- 185.109.147.122 port 80 - maximusstafastoriesticks.info - GET /a5/
- rktazuzi7hbln7sy.onion (tor domain for the decryption instructions)
Final words
Much of this malspam is easy to spot among the daily deluge of spam most organizations receive. However, this PDF attachment/embedded Word doc scheme is likely an attempt to bypass spam filtering.
As always, if your organization follows best security practices, you're not likely to get infected. For example, software restriction policies that deny binary execution in certain Windows directories can easily stop this infection chain. Even without software restriction policies, the intended victim receives warnings from both Adobe reader and Microsoft Word during the infection process.
So why do we continue to see this malspam on a near-daily basis? I suppose as long as it's profitable for the criminals behind it, we'll continue to see this type of malspam. If anyone knows someone who's been infected with Jaff ransomware, feel free to share your story in the comments section.
Emails, malware samples, and pcaps associated with the 2017-05-23 Jaff ransomware malspam can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments
Anonymous
May 24th 2017
8 years ago
Anonymous
May 25th 2017
8 years ago