EternalBlue 5 years after WannaCry and NotPetya
We are about two months past the 5-year anniversary of WannaCry outbreak[1] and about a week past the 5-year anniversary of NotPetya outbreak[2]. Since both WannaCry and NotPetya used the EternalBlue[3] exploit in order to spread, I thought that it might be interesting to take a look at how many internet-facing systems still remain vulnerable to it.
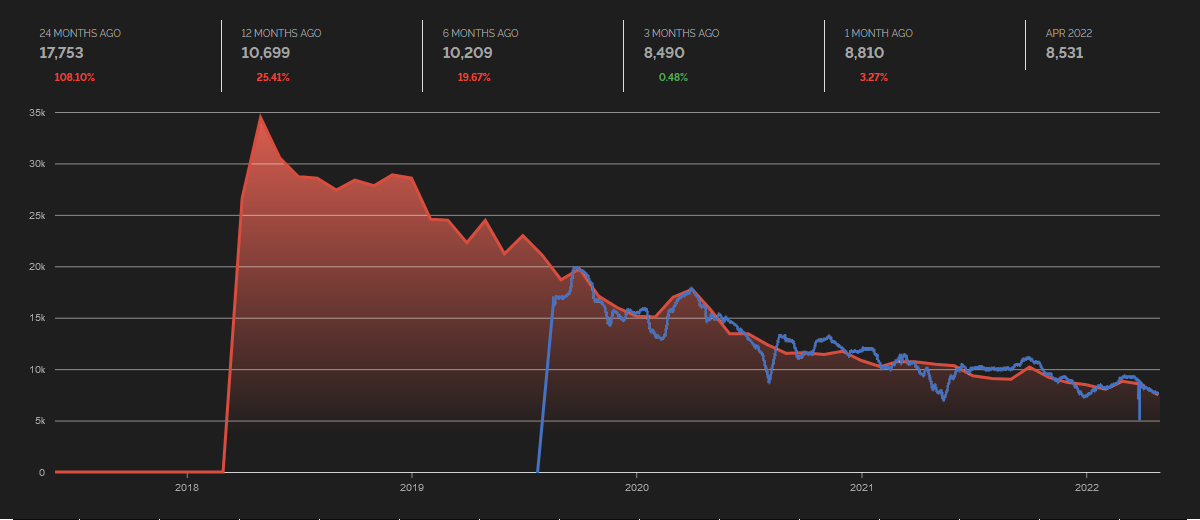
A quick search on Shodan Trends shows us that although the situation has gotten much better over the last few years, and it still seems to be slowly improving, more than 5,000 vulnerable machines (exactly 5,565 at the time of writing) are still accessible from the internet.
The blue line in the chart shows a more detailed view of the situation – it was created using Shodan data gathered daily using my TriOp tool[4].
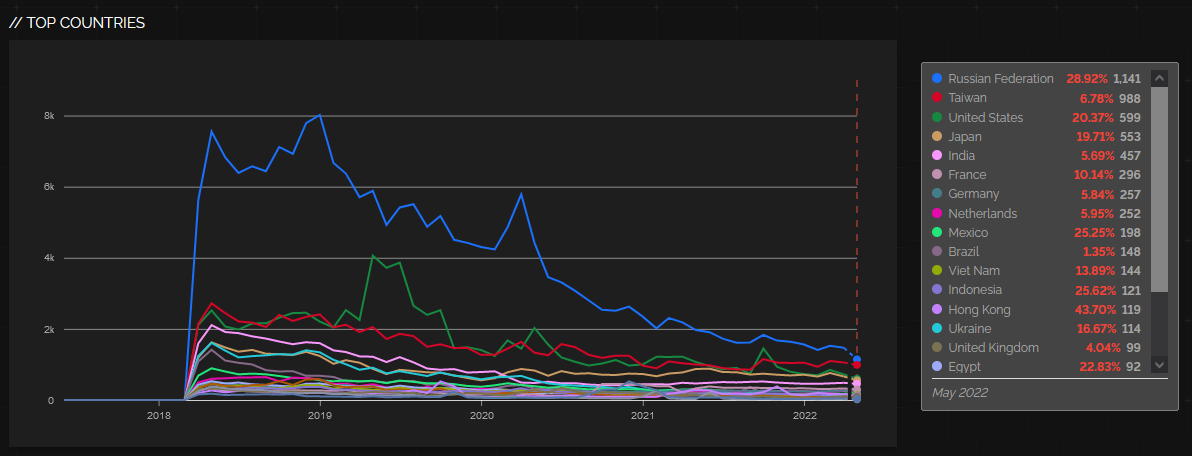
At the end of May, most vulnerable systems were to be found in Russia, Taiwan, United States, Japan and India[5].
At the time of writing, these countries are still at the top when it comes to systems affected by EternalBlue, though the corresponding numbers are somewhat lower (742 externally facing systems in Russia, 735 in Taiwan, 475 in the US, 391 in Japan and 327 in India).
It should be mentioned that some of the detected systems are undoubtedly honeypots and are therefore not really vulnerable. But even half of the detected systems fell into this category (and it will probably be significantly less than that), it would still leave thousands of systems affected by a 5-years old critical vulnerability.
And not just any vulnerability – one, that was used to spread two of the most famous computer worms in history and which was therefore heavily covered even by mainstream media. One doesn’t have to be too imaginative to get a good idea of how many systems that are missing patches for less well known vulnerabilities are left exposed online. Hopefully, it won’t bite us too much when someone decides to take advantage of them...
[1] https://en.wikipedia.org/wiki/WannaCry_ransomware_attack
[2] https://en.wikipedia.org/wiki/Petya_and_NotPetya
[3] https://en.wikipedia.org/wiki/EternalBlue
[4] https://untrustednetwork.net/en/triop/
[5] https://trends.shodan.io/search?query=vuln%3AMS17-010#facet/country
-----------
Jan Kopriva
@jk0pr
Nettles Consulting


Comments
Anonymous
Jul 5th 2022
3 years ago
Anonymous
Jul 6th 2022
3 years ago