Diving into a Google Sweepstakes Phishing E-mail
I was recently forwarded another phishing e-mail to examine. This time, it was an e-mail that claimed to be from Google. The e-mail included a pdf file, and instructed the recipient download the file for further information. Figure 1 below shows the headers, while Figure 2 shows the content of the e-mail message.
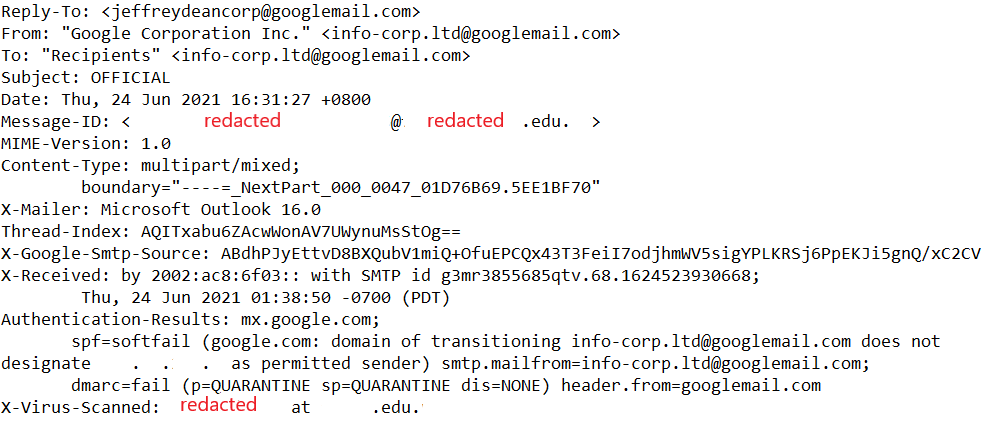
Figure 1: E-Mail Headers
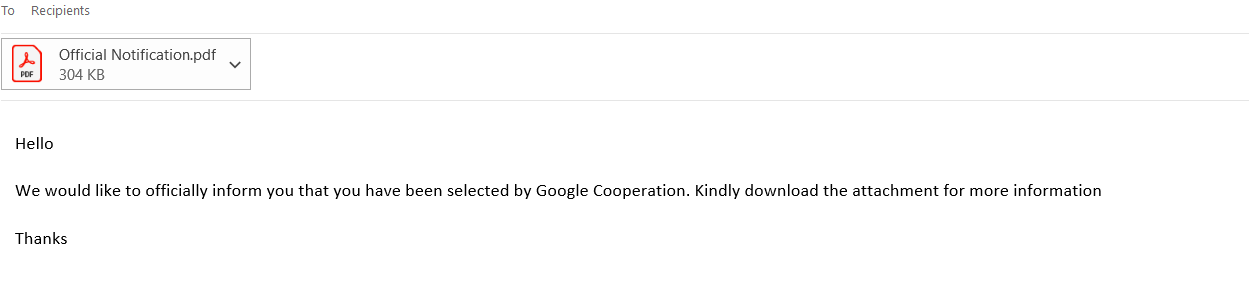
Figure 2: Contents of Phishing E-Mail
With reference to Figure 1, the e-mail was sent via an academic institution’s e-mail system (details redacted to protect privacy of the affected asset owner). We can also see that the perpetrator attempted to use legitimate looking e-mail addresses (e.g., “info-corp.ltd”).
We can see that the e-mail appeared to be quite sparse (Figure 2), and subtly nudged the recipient to open the pdf file for additional details. Before opening unknown pdf files, let’s dissect it and see if there is any malicious code embedded within the file. I used Didier’s pdfid.py and pdf-parser.py to perform the analysis.
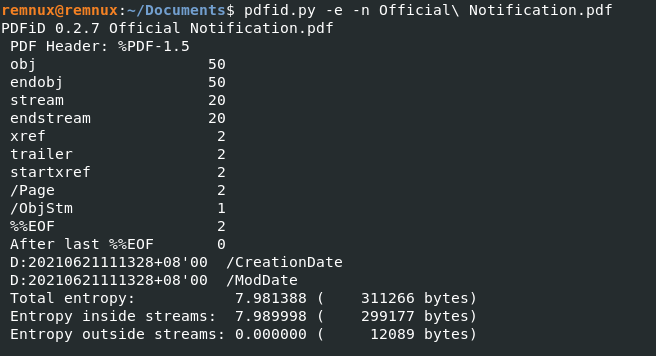
Figure 3: Analysis of Official Notification.pdf via pdfid.py
Looking at the output (as shown in Figure 3), we can see that the file is pretty tame. We would see some additional outputs such as /JS, /JavaScript, /AA or /OpenAction if the pdf file had malicious functionality embedded inside. I was also curious if any metadata could be obtained so as to have some insight on the perpetrator. Using pdf-parser.py, I looked through the objects within the pdf file and discovered object 36 containing some data. Figure 4 shows the output of object 36 (the -c flag displays the content, and -w displays the raw output). It appears that the author’s name was “hp”, and the file was created with Microsoft Word 2013. The file timestamps showed that it was created on June 21 2021 at 11:13:28 (+8 GMT). Unfortunately, there was nothing much else of interest. Although the author’s name (in this case, the author’s name would also reflect the name of the user account), program that created the pdf file and time zone setting could be retrieved, it could be something that the perpetrator had deliberately set up/created. Nevertheless, it is still useful Open Source Information (OSINT) that should be noted down to track down phishing campaigns.
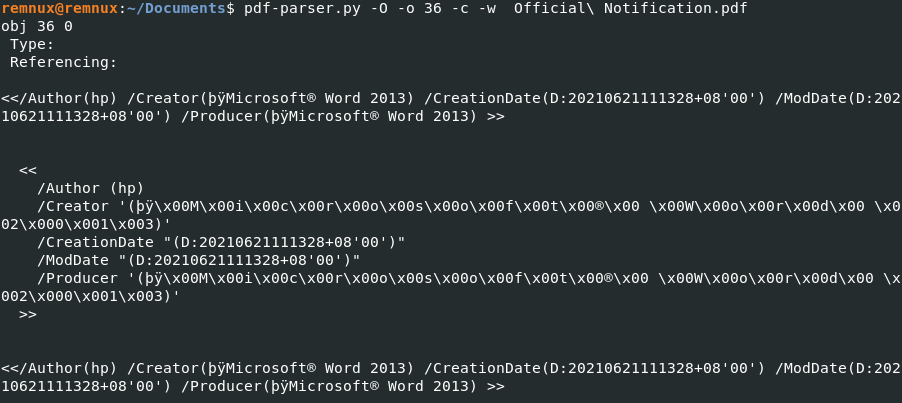
Figure 4: Metadata of Official Notification.pdf via pdf-parser.py
After noting down these details, I examined the contents of the pdf file. Figures 5 and 6 show an excerpt of the content, and the perpetrator have taken quite a bit of care to ensure that the document looked legitimate. The address used was a legitimate address used by Google UK, and reference numbers were also used to make it look more official. Finally, the document purportedly states that the recipient has won £1,950,000.00 (~US$2,710,110.00), along with some Google hardware. However, there were evidently some suspicious areas. For example, it was highly unlikely that a contact from Google would be using the domain “goocoperate.com” for correspondence. A quick check on that domain name showed that “goocoperate.com” was registered on September 29 2020, and directed the visitor to the default site landing page of the hosting provider.
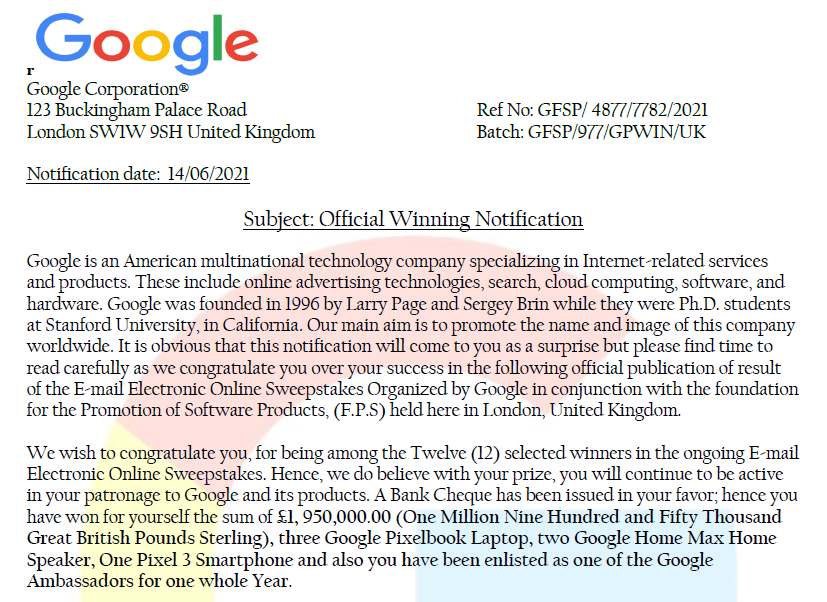
Figure 5: Content of Official Notification.pdf (Part 1)

Figure 6: Content of Official Notification.pdf (Part 2)
The style of phishing is not new, and it looks like the phishing mail has been upgraded. I did some research and the previous “prize” offered was £950,000.00 (US$1,320,310.00). Victims who wrote back to them would be persuaded to pay for the bank and delivery charges, and never receive the purported prize money. It appears that this tactic has worked well, or else the perpetrators would not have bothered to refresh the “congratulatory” letter and also increase the prize winnings. Thankfully, the pdf file was not weaponized, though it remains to be seen that it would stay that way. As mentioned in my previous diary, always verify the authenticity of the e-mail you receive when in doubt [1]. Don’t forget to look out for your loved ones, and remind them about the various phishing e-mails/messages they might receive.
Update: I forgot to further classify this e-mail as an advance fee scam after the analysis. It could seem as that in the first place, but we can never know if the perpetrators add a little bonus in the pdf files.
Indicators of Compromise (IOCs):
Official Notification.pdf (304KB)
MD5: 15ff78d798d1c32f6017a99f1b675ce3
SHA1: 7749a3d4be7505abca3000d1c3e3a4afdd428d04
References:
[1] https://isc.sans.edu/diary/27356
-----------
Yee Ching Tok, ISC Handler
Personal Site
Twitter


Comments