Data exfiltration and the use of anonymity providers
Crime analysts take particular care in identifying how a culprit removes stolen goods from the crime scene. This process can reveal how thoroughly the theft was planned, and how well resourced the attacker was. Tracking some digital data theft incidents, we’ve noticed an interesting switch in the modus operandi of a number of threat agents.
In the past, stolen data was usually moved from the compromised network onto networks under different legal jurisdiction, often in East Asia. As of May of this year, however, we noticed these gradually swapping out for networks within the EU and the US. This seemed a bit awkward.
Certain hosts started tunneling data to the network of an Indiana based provider of anonymity services, SecureIX. This provider allows users to set up a PPTP VPN connection to its servers, then hiding all their traffic behind a SecureIX IP address. The service is intended for well-meaning users who wish to remain anonymous while surfing. However, the for-a-fee SecureIX service also allows users to run services through such IP address. Hosts compromised by the attackers were configured to ship data to a specific port on a SecureIX IP, from where it was tunneled back to the attacker.
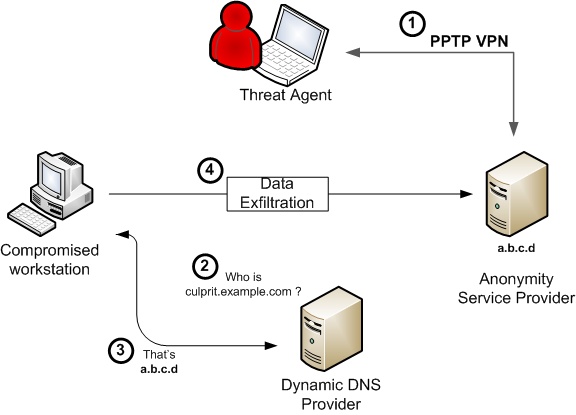
It’s important to understand that organizations such as SecureIX are not rogue service providers. As is the case with dynamic dns services, their services can however be abused by various criminal elements. However, their Terms of Service state:
- You remain solely responsible for your actions, and you agree to indemnify and hold harmless SecureIX, and any related businesses.
- You agree to only engage in lawful activities. Our service provides security, not immunity from local, state or federal laws.
- You understand that your privacy, although very important to us, can not be guaranteed.
This implies that the goal of the attackers is mainly to make analysts’ life more difficult. In the case of a prosecution, SecureIX would disclose the data it has on them. While it is still operational, on June 8th, the proprietors of SecureIX announced their service was now for sale.
Only two weeks after this announcement, something interesting happened. All hostnames previously pointing to SecureIX, suddenly resolved to the IP address space of Relakks. Relakks provides the same services, but from Sweden.
This organization was founded in collaboration with Sweden’s Pirate Party, and allows users to anonymously surf the internet. They provide identical service to SecureIX, but the legal implications are somewhat different, as they mention on their website:
“For Swedish authorities to force RELAKKS to hand over traffic data including your RELAKKS IP at a specific point in time, they will have to prove a case with the minimum sentence of two years imprisonment. Regarding inquires from other parties than Swedish authorities RELAKKS will never hand over any kind of information.”
While I am not a lawyer, this appears accurate under Swedish legislation.
Knowing that these attacks most likely originate from outside the country, there is some potential to investigate through means of the recent wiretapping laws that will be active in the country as of 2009. While this law is somewhat convoluted, it seems that in certain cases, it would potentially be possible for Swedish authorities to intercept traffic originating from abroad towards RELAKKS, and originating from RELAKKS towards foreign IP addresses.
Theoretically, this could allow for traffic pattern (not content, as traffic to and from the provider would likely carry different ciphertext) analysis and as such the identification of a “loop” through Swedish IP space. It’s unlikely such extensive investigation would be undertaken for cases such as this, where damages are difficult to identify, let alone prove.
So, this makes law enforcement’s life somewhat harder. On the other hand, for network administrators this may be an asset. Each of the attacks connected out from the compromised corporate network onto the following ranges:
66.175.214/24 (SecureIX)
66.175.215
66.175.216
83.233.180/24 (Relakks)
83.233.181
83.233.182
83.233.183
83.233.168
83.233.169
These are relatively small networks, and I would recommend any organization that has been affected by targeted attacks in the past to carefully review egress connections towards these networks.
Note that we are not advertising this as a blocklist: these services have very legitimate purposes, and many people use them for exactly what they are intended for: to browse the internet anonymously. While it’s completely benign for a client to use one of these services to connect to your corporate web service, a host on your network should probably not be initiating connections to the above.
"Is Troy Burning", a presentation on targeted attacks I gave at SANSFire covers to some degree the various DNS configurations similar threat agents use to maintain stealthy access to networks. If you see anything of interest regarding this modus operandi, we would be very interested in hearing from you.
--
Maarten Van Horenbeeck
maarten at daemon.be


Comments