Another Day - Another Ransomware Sample
Catching ransomware is pretty easy these days. I setup a procmail filter that will extract all e-mails with compressed JavaScript attachments. Whatever is left in the morning after AV decimated the folder I will usually take a quick look at.
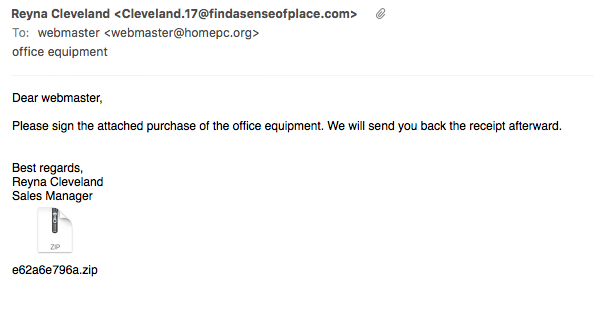
Today, I got a bunch of e-mails with the subject "office equipment":
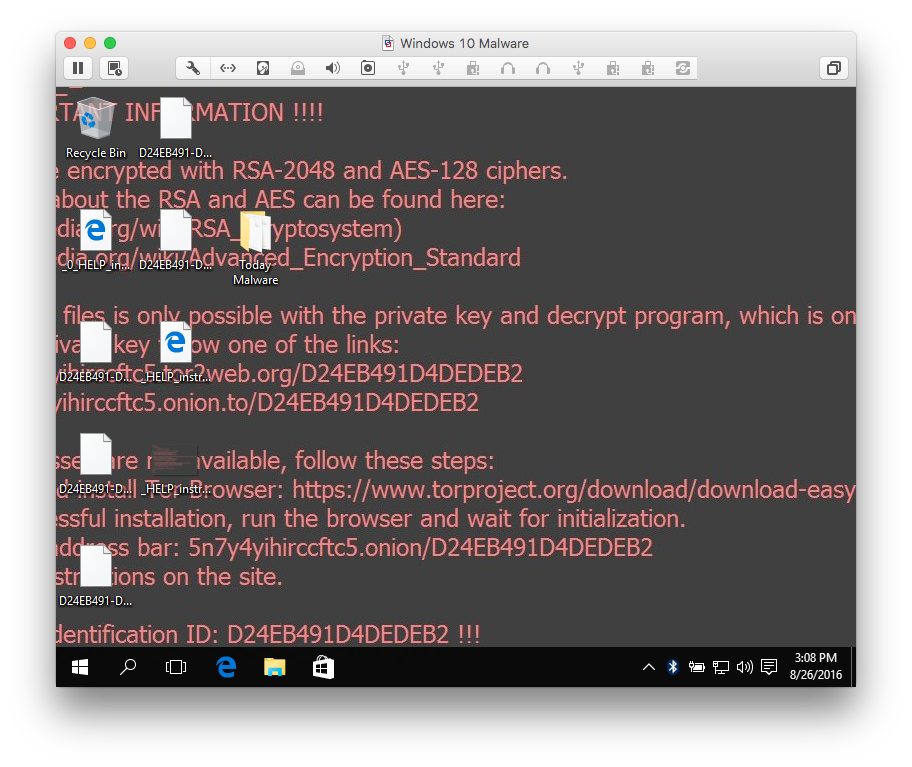
Sure enough. I run it in a virtual machine and end up with the usual crypto ransomware screen:
This time, the malware doesn't even try to hide. One of the hostnames used by this run is "brothermalw.ws". In addition, the samples all use the exact same user agent string, which doesn't match the browser installed on the infected system (It was Windows 10, but the malware used an IE 7.0 user agent string):
Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 10.0; Trident/7.0; .NET4.0C; .NET4.0E; .NET CLR 2.0.50727; .NET CLR 3.0.30729; .NET CLR 3.5.30729)
So pretty easy to now pull out the URLs that the malware connect to from bro:
zcat http* | bro-cut method host uri user_agent | grep 'Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 10.0; Trident/7.0; .NET4.0C; .NET4.0E; .NET CLR 2.0.50727; .NET CLR 3.0.30729; .NET CLR 3.5.30729)' | awk '{print $1 , $2 , $3}' | sort -u
GET 210.240.104.2 /upp0nqa
GET brothermalw.ws /06qbbzy7 <---------- Yes... they are not even trying to hide the fact that this is malware ;-)
POST 51.254.55.171 /data/info.php
GET baer-afc2.homepage.t-online.de /4yhgvna
GET realm-of-rage.heimat.eu /ut1s5
GET rejoincomp2.in /1tdqo6
GET www.dsalchi.org /uk0lo
GET www.galleriacolonna.org /yhcx6y
POST 138.201.191.196 /data/info.php
POST 188.127.249.203 /data/info.php
POST 51.254.55.171 /data/info.php
POST nkyhrjiaeqcmtqth.pw /data/info.php
As so often, "/data/info.php" may actually also do a pretty good job in detecting these infections. Snort already alerts on the requests to ".pw" hosts.
Indicators of compromise: The IPs and the host names appear to be too ephemeral to be useful as IoCs. I would suggest the "/data/info.php" URL. I don't see that used a lot in non-malicious requests.
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments
Anonymous
Aug 26th 2016
9 years ago
brothermalw.ws 213.229.74.92, 104.232.35.136 IPv6 Associated Address: 66%
baer-afc2.homepage.t-online.de 80.150.6.138 2003:2:2:15:80:150:6:138 IPv6 Associated Address: 100%
rejoincomp2.in 104.232.35.136, 213.229.74.92 IPv6 Associated Address: 66%
www.galleriacolonna.org 213.205.40.169 IPv6 Associated Address: 66%
nkyhrjiaeqcmtqth.pw 91.226.92.208 IPv6 Associated Address: 50%
210.240.104.2 IPv6 Associated Address: 50%
51.254.55.171 IPv6 Associated Address: 50%
138.201.191.196 IPv6 Associated Address: 50%
188.127.249.203 IPv6 Associated Address: 50%
51.254.55.171 IPv6 Associated Address: 50%
Joe Klein
Anonymous
Aug 26th 2016
9 years ago
Anonymous
Aug 27th 2016
9 years ago
Anonymous
Aug 27th 2016
9 years ago
Anonymous
Aug 29th 2016
9 years ago
Anonymous
Aug 30th 2016
9 years ago
Anonymous
Aug 30th 2016
9 years ago