nslookup's Debug Options
A friend was having unexpected results with DNS queries on a Windows machine. I told him to use nslookup's debug options.
When you execute a simple DNS query like "nslookup example.com. 8.8.8.8", you get an answer like this (notice that in my nslookup query, I terminated the FQDN with a dot: "example.com.", I do that to prevent Windows from adding suffixes):
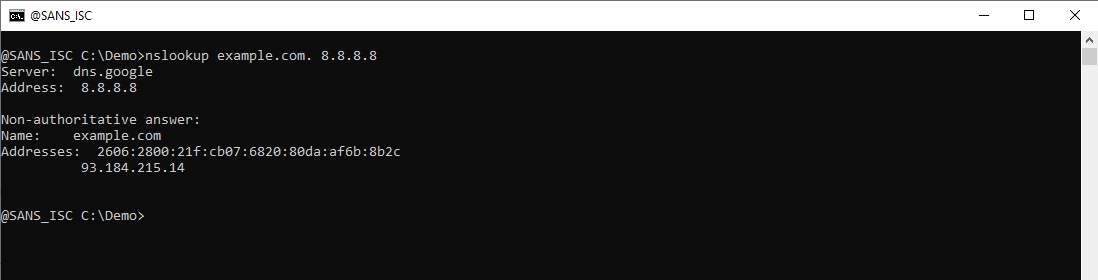
You see the result of a reverse DNS lookup (8.8.8.8 is dns.google) and you get 2 IP addresses for example.com in your answer: an IPv6 address and an IPv4 address.
If my friend would have been able to run packet capture on the machine, he would have seen 3 DNS queries and answers:
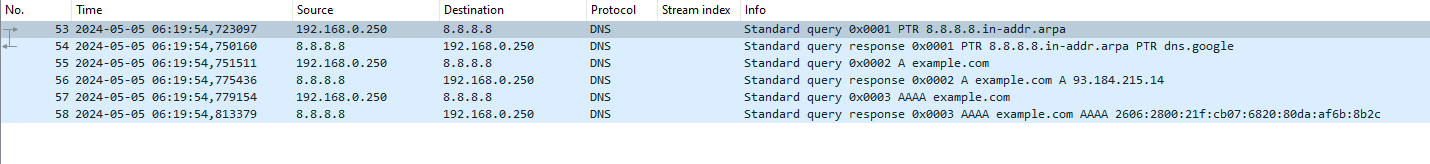
A PTR query to do a reverse DNS lookup for 8.8.8.8, an A query to lookup IPv4 addresses for example.com, and an AAAA query to lookup IPv6 addresses for example.com.
One can use nslookup's debug options to obtain equivalent information, without doing a packet capture.
Debug option -d displays extra information for each DNS response packet:
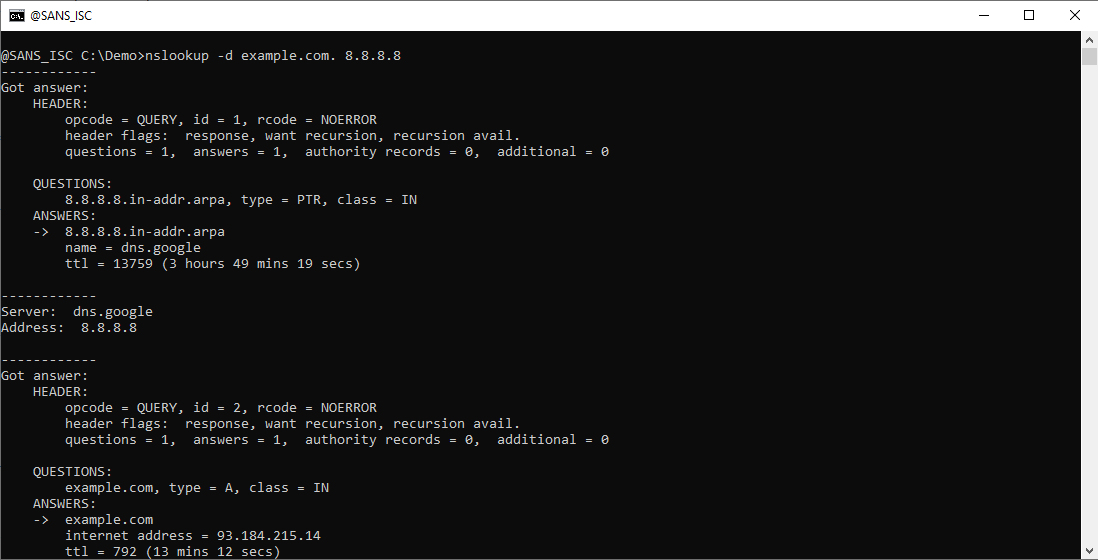
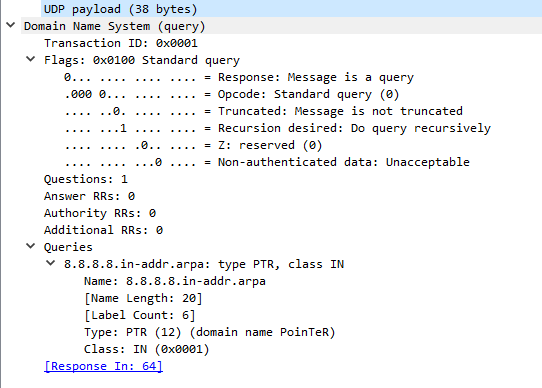
Here is nslookup's parsed DNS response packet for the PTR query:
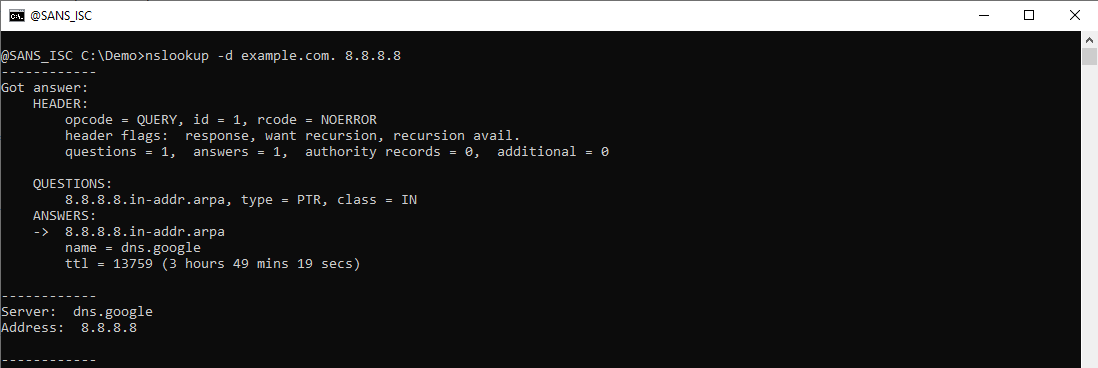
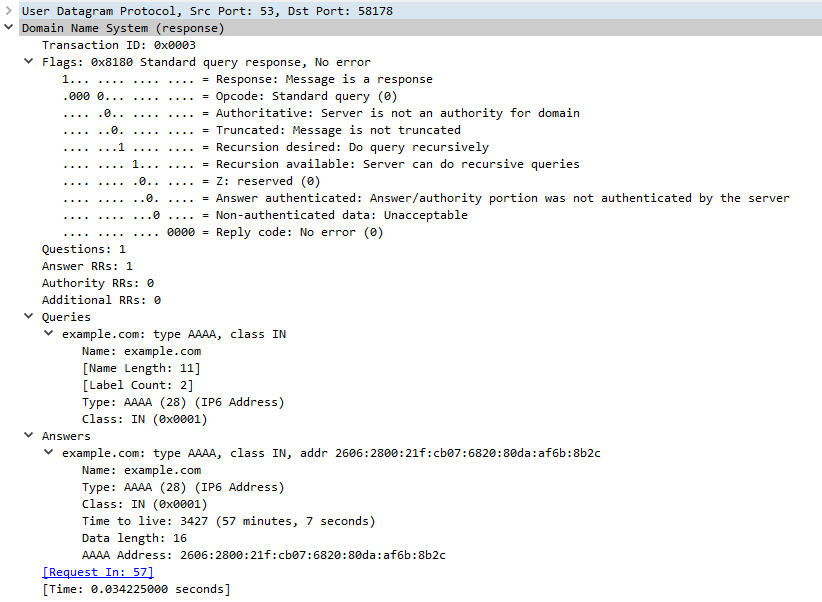
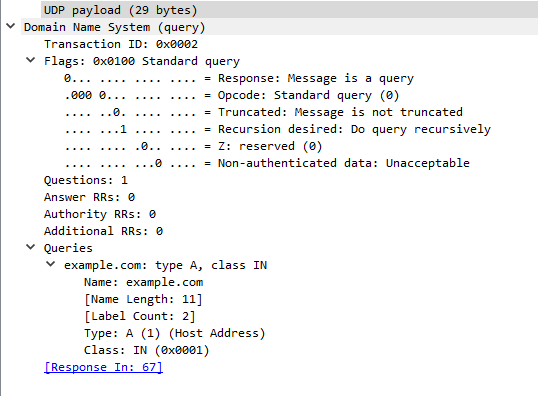
Here is Wireshark's dissection of this packet:
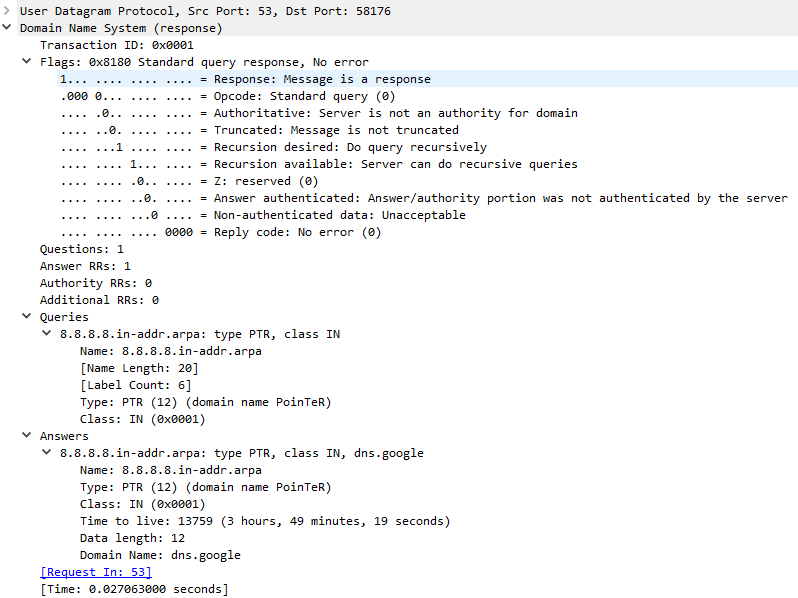
You can see that the debug output contains the same packet information as Wireshark's, but presented in another form.
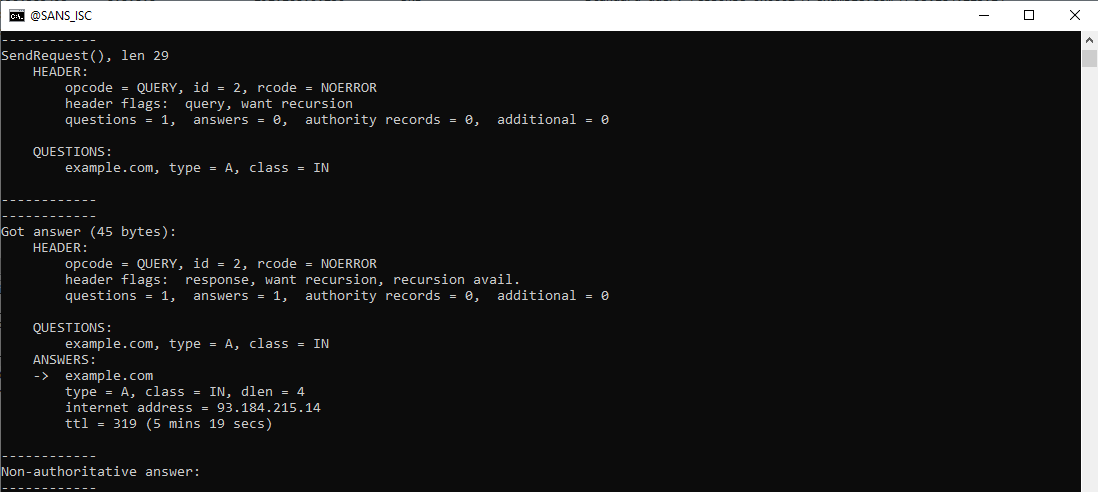
The same applies for the A query:
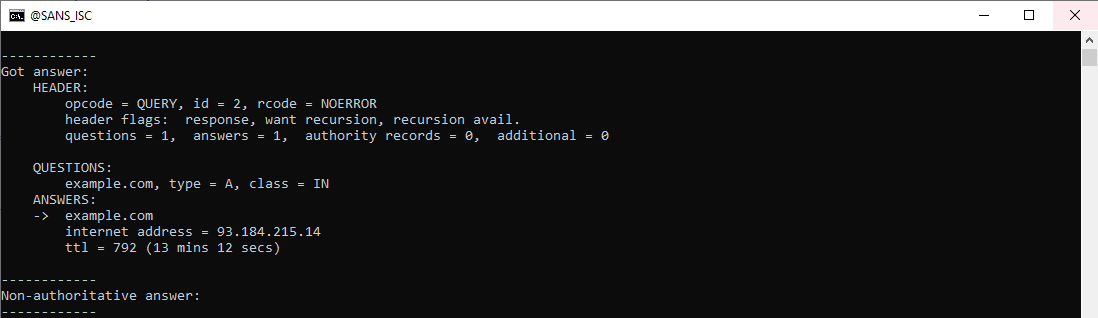
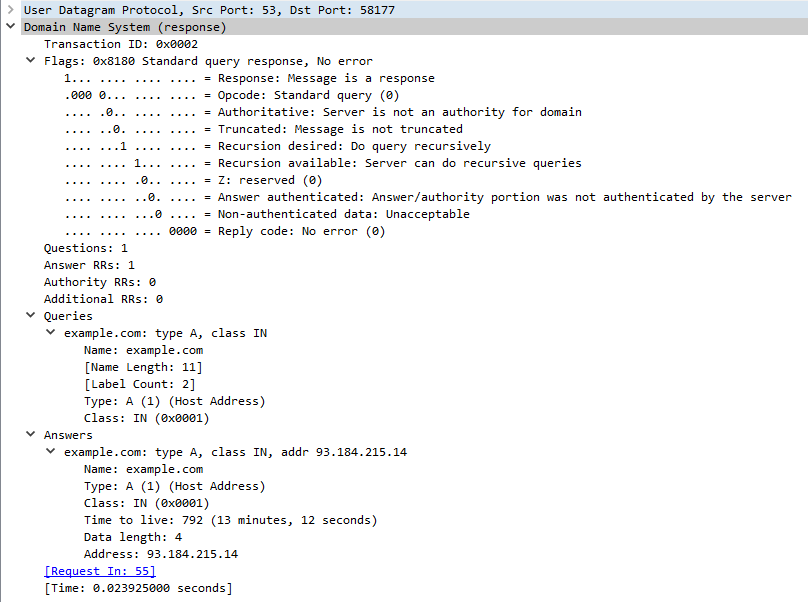
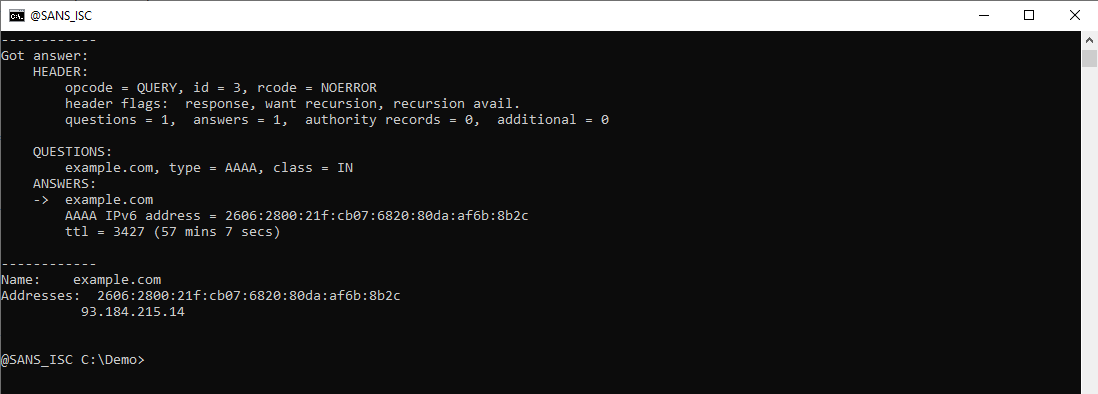
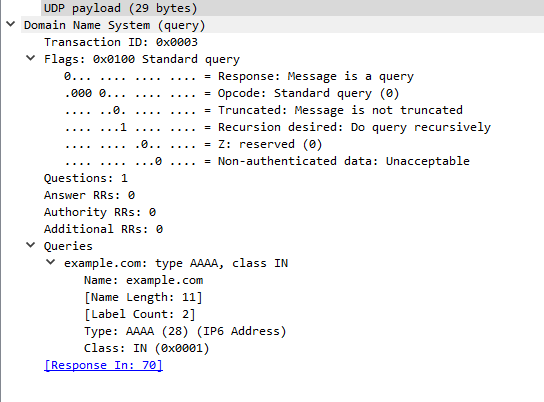
And the AAAA query:
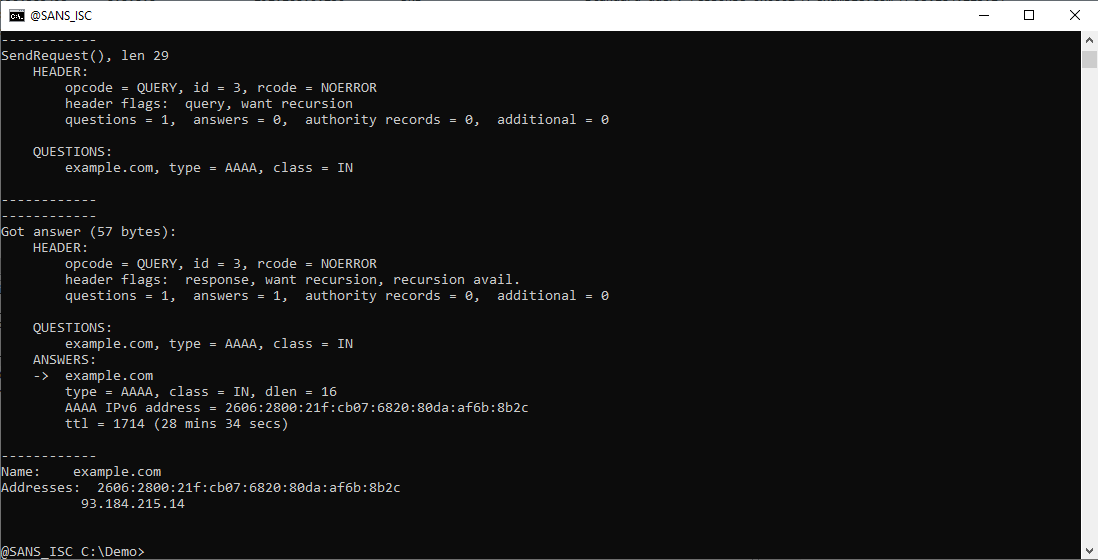
If you also want to see the DNS query packets, you can use debug option -d2:
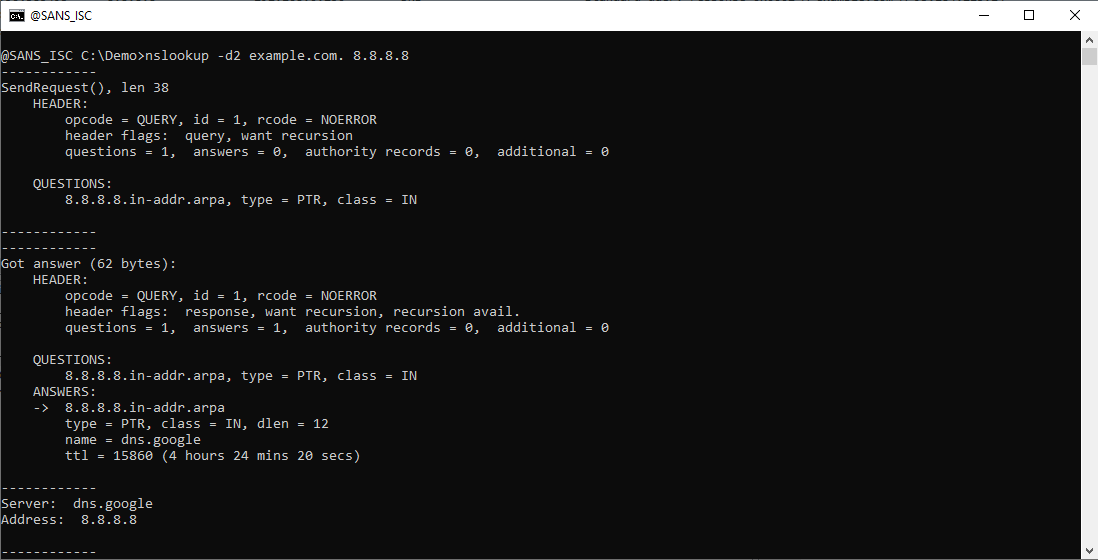
Besides the parsed DNS query, you now also see the length in bytes of each DNS packet (the UDP payload).
Here is the A query:
And here is the AAAA query:
Didier Stevens
Senior handler
blog.DidierStevens.com


Comments