Using Shodan Monitoring
Back in March, Shodan started a new service called Shodan Monitor(1). What this service does is notify you of ports that are open on the network you specify. When you initially setup your network, you put in your CIDR to monitor and then select notification triggers where you will get emails for any of these categories that show up on the specified network. In the notification emails, you get a link to be able to whitelist systems. I’m finding that the uncommon ports to be chatty for large networks, and tend to whitelist many of these.
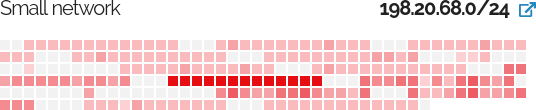
They have a heat map that shows you what hosts has the most open ports. You can hover over them and see what system have the largest footprint on the Internet.
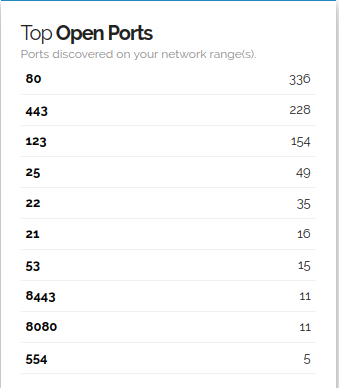
The Initial dashboard shows you the top port breakdown, notable ports and possible vulnerabilities for your networks you are watching.
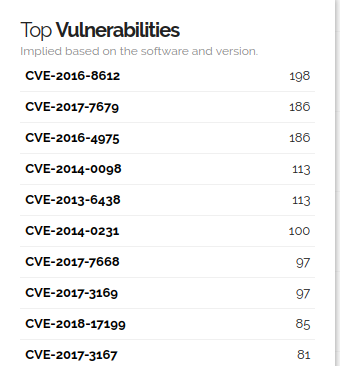
While this list could be useful, it’s only gathering these details based on banner information, which web applications have lots of backported patches which make this less valuable for web.
While you can and should script this within you organization using Nmap, this is great way to validate and see what attackers are seeing from outside with little effort. Has anyone found other cool uses of this service yet?
(1) https://monitor.shodan.io/


Comments
Anonymous
May 21st 2019
6 years ago
Anonymous
May 21st 2019
6 years ago
Anonymous
May 21st 2019
6 years ago
Anonymous
May 22nd 2019
6 years ago
Anonymous
May 26th 2019
6 years ago