USB cleaning device for the masses
For so long, USB keys have been a nice out-of-band infection vector. People like goodies and people like to plug those small pieces of plastic into their computers. Even if good solutions exists (like BitLocker - the standard solution provided by Microsoft), a lot of infrastructure are not protected against the use of rogue USB keys for many good or obscure reasons.
There are also multiple reasons to receive USB keys: from partners, customers, contractors, vendors, etc. The best practice should be to scan any suspicious device against malicious documents but how to achieve this in a safe AND not boring way. If you propose a tool that is easy to use, you will increase your chances to have it adopted by more people!
The CIRCL (Computer Incident Response Center Luxembourg) is coming from a very small country but they are very active and renowned. They developed a tool to sanitize USB keys. It's so easy that even non-tech people can use it! The project is called "CIRCLean". It's a piece of software that you install on an inexpensive Raspberry computer. You connect the suspicious device in the USB port A, a clean USB device in port B, power the box and wait for the process to be completed (depending on the amount of data to analyze). One picture is worth a thousand words:
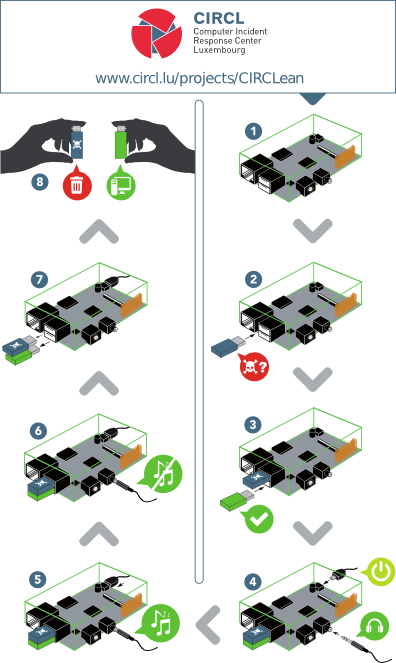
What does it do? Multiple operations are performed on files, based on their MIME type. Example: Word files are converted to PDF then to HTML. Other files are renamed and prepended with a "DANGEROUS_" prefix. Once sanitized (or non dangerous), files are copied to the destination USB key. The code is available on their github repository.
Xavier Mertens
ISC Handler - Freelance Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments
Anonymous
Oct 29th 2015
1 decade ago
It shouldn't need to, as you're not going to be plugging the questionable device into your computer.
However, it would be great if it *could* detect such modifications so that you could be informed to destroy the USB stick.
Anonymous
Oct 29th 2015
1 decade ago
Anonymous
Oct 29th 2015
1 decade ago
It shouldn't need to, as you're not going to be plugging the questionable device into your computer.
However, it would be great if it *could* detect such modifications so that you could be informed to destroy the USB stick.[/quote]
With respect, you cannot rely on that.
As I understand it, the ultimate problem with a malicious USB controller is that it allows attackers choice as to when and where to present malicious material & when not.
Of course the copy process can protect targets down the line from such duplicity, so it does help.
But, the CIRCLean device becomes one of "your computer"s too. It will be a target for malware. It may have a much restricted attack surface, but if it became popular then it would be single well understood target for a malware author. If necessary the CIRCLean device could be attacked by a malicious controller, once the scanner was owned it could potentially infect other USB controllers, plus the bonus of being able to infect other clean material it scans.
All that said, the process of transforming documents to less dangerous document formats could be a very worthwhile gain for run of the mill work.
People may think this nit picking, but I did not want leave this unremarked.
Overall, CIRCLean looks like a very worthwhile tool
Anonymous
Oct 30th 2015
1 decade ago
Anonymous
Apr 4th 2016
9 years ago
Anonymous
Apr 4th 2016
9 years ago