Targeted Phishing Attacks in the Financial Industry: Fire-3 Phishing Kit
[Thanks to Justin Trujillo (Cyber Security Analyst) from loanDepot for alerting us of this particular incident, and for co-authoring this article]
Financial companies are heavily targeted with various more or less targeted phishing attempts. The attacks are often trying to collect e-mail credentials for business-email-compromise (BEC) attacks. The attacker will log in to the victim’s cloud-based email account to either add a “Forward” address or read the users e-mail. Once an email asking for payment instructions arrives, the attacker will respond with fake instructions.
It isn’t often that we not only get a hold of the email triggering the attack but also a copy of the full phishing kit used by the attacker.
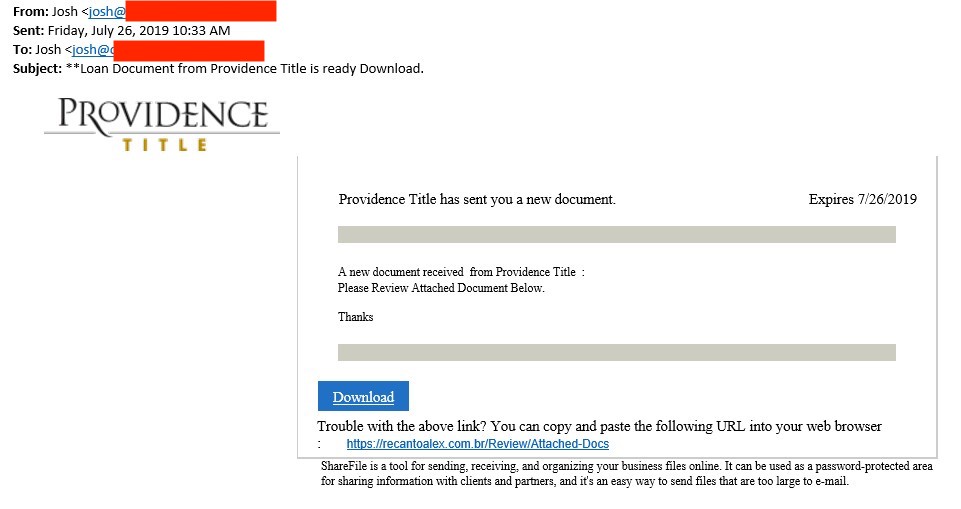
The email, in this case, is very typical for this type of attack.
The from address used an existing domain name that was likely unrelated to the attack and spoofed. The domain uses a generic SPF record for Outlook 365, so it likely was a nice “From” domain to use and to slip past filters. As far as I can tell, the domain was not related to "Providence Title", and the actual Providence Title company is not directly involved here but just used to make the email look more convincing.
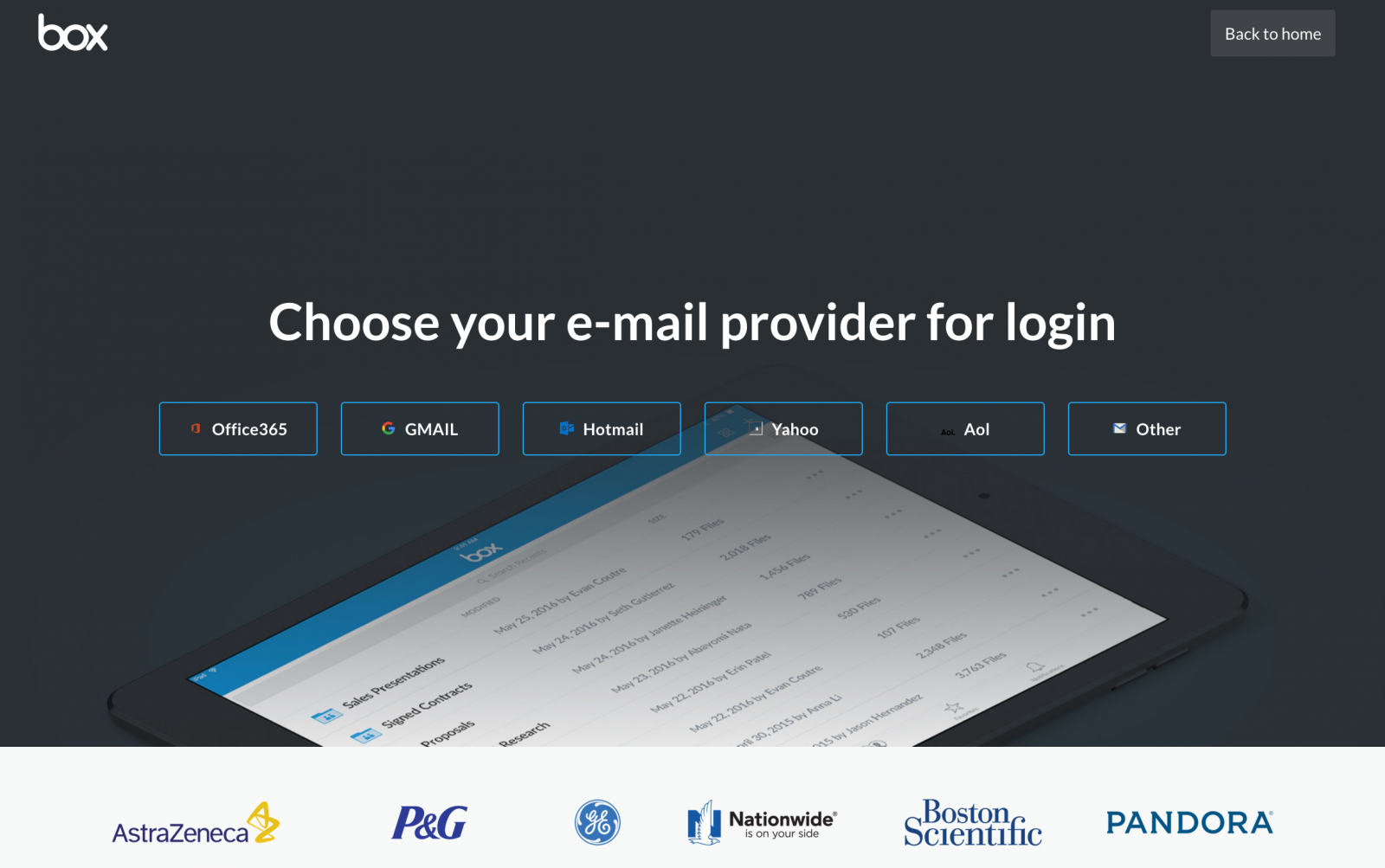
The victim, in this case, is a company providing home loans. Receiving documents from a title company is likely part of everyday business. In this case, the document is not attached to the email. Instead, it claims to be reachable via a cloud storage service. Clicking on the link leads to a lookalike “Box” page:
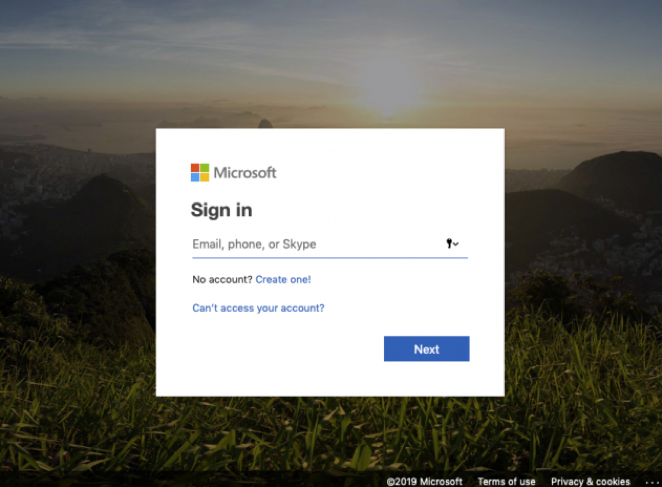
The page offers logins for pretty much any major cloud-based email service. The logins are done pretty well. Here is the Office 365 version of the login:
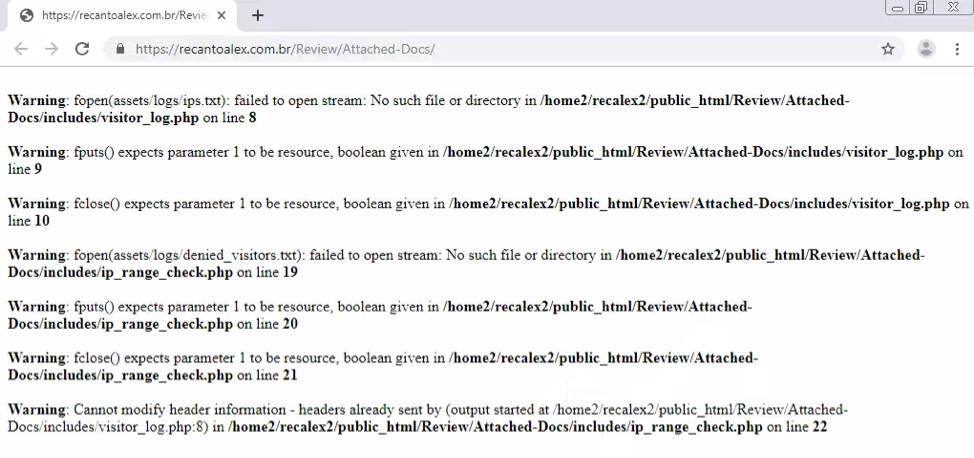
In a lucky break for us, the attacker made a mistake this time around. The landing page didn’t work correctly.
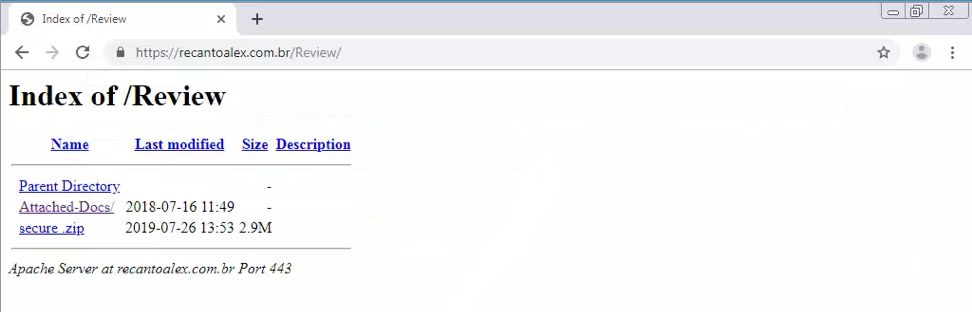
These are classic PHP error messages, revealing the location of files. It appears that the directory the log file was supposed to be stored in was deleted and the PHP page did not properly handle the error. Taking things further and going back a directory, we can see what’s inside the index:
Looks like the “Attached-Docs/” file was the phishing landing page, but “secure.zip” seemed out of place. “Parent Directory” just takes us back to the hacked website, but “secure.zip” downloads an actual zip file. The zip file was password less, and that’s where we see that file name:
In Justin’s own words “I had seen this file reference pop up more times than I could count during phishing investigations. I opened the file and discovered the complete phishing kit. This kit included all the HTML, CSS, JavaScript and image files used for the phishing pages, as well as some PHP code.”
The fire-3 folder contains a few files of interest:
CONTROLS.php: Any credentials harvested are exfiltrated via email. This file includes the email address receiving the data: 1resultboxx@gmail.com . (I contacted the address for comment but didn’t receive any answer yet)
Includes/blocklist.dat: A list of blocklisted networks. This is the usual list of security company and cloud service IPs that are blocked from accessing the site. There is also an “unknown” IP section that suggests the attacker had been updated the list based on previous campaigns.
Includes/netcraft_check.php: This file checks the user agent to block access from Netcraft (not sure if that user agent is actually used by Netcraft).
assets/logs/ips.txt: Unfortunately, this file was blank due to broken functions, but any IP addresses and user agents are logged to this file in an access log like format.
It looks like we are not the first once to come across this phishkit. A tweet by IpNigh from about a week ago did point to the same email address used in this phish. However, the phishing page looked a bit different and the attacker attempted to impersonate Dropbox, not Box.com. @IpNigh is a bot that will post phishing page information to Twitter.
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
Twitter|
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |



Comments