TA551 (Shathak) continues pushing BazarLoader, infections lead to Cobalt Strike
Introduction
TA551 (also known as Shathak) represents e threat actor behind malspam that has pushed different families of malware over the past few years. TA551 previously distributed Ursnif, Valak, and IcedID.
TA551 stopped sending IcedID sometime in June 2021 and began pushing Trickbot.
By July 2021, TA551 stopped sending Trickbot and began pushing BazarLoader (sometimes called BazaLoader). TA551 continues to push BazarLoader, and Cobalt Strike is often follow-up malware for these infections.
Today's diary reviews a TA551 BazarLoader infection followed by Cobalt Strike on Tuesday 2021-08-10.
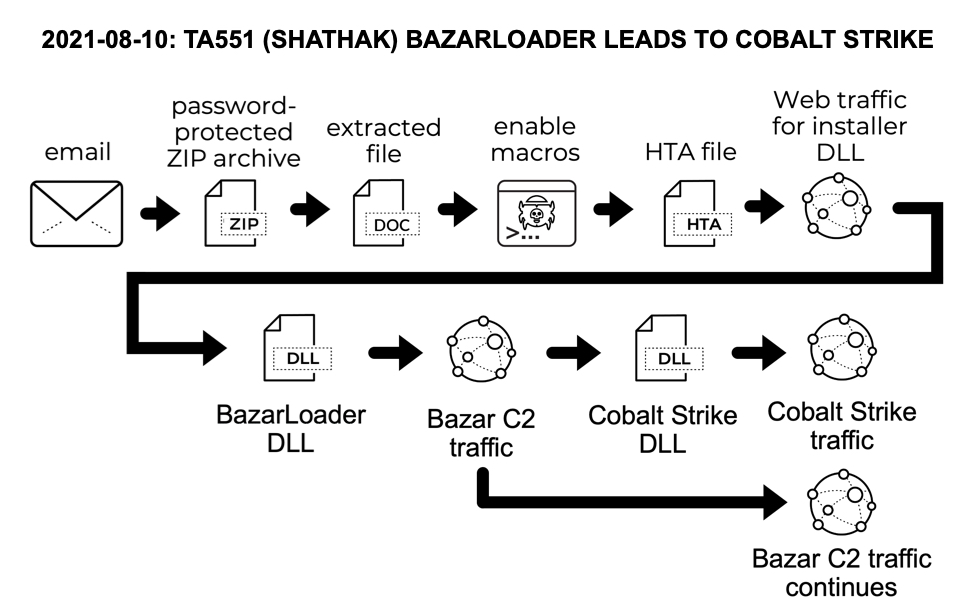
Shown above: Flow chart for the chain of events in the infection on 2021-08-10.
From email to document
Examples of TA551 emails from Tuesday 2021-08-10 are not yet publicly available, but a recent example was submitted to VirusTotal from a wave last week on 2021-08-04. These emails have different passwords each day, and we often see different passwords for different emails during the same day. These emails spoof replies to previously valid emails, but they no longer include message text from the email chain. We only see subject lines and spoofed sending addresses from the previously valid emails.
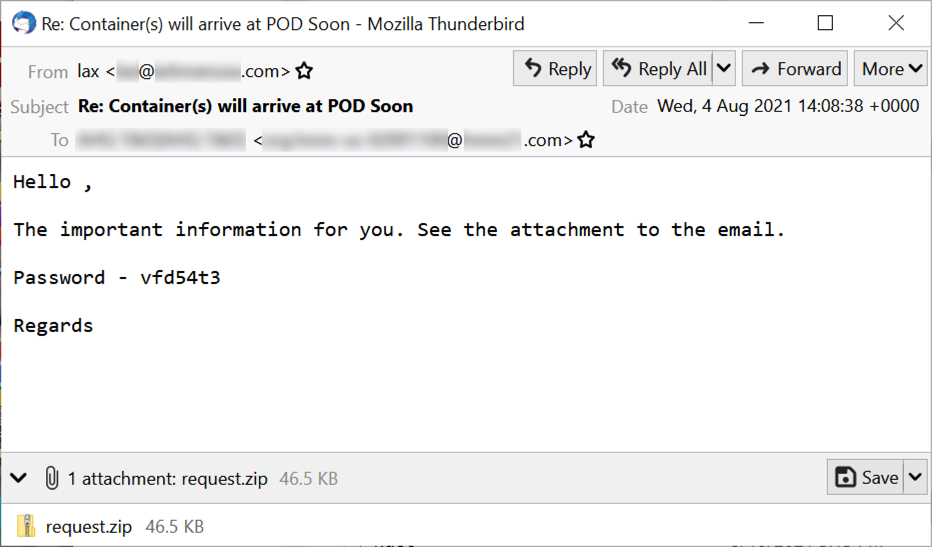
Shown above: An example of TA551 malspam from 2021-08-04.
Attachments are currently named request.zip or info.zip. Potential victims would open these password-protected zip archives on a vulnerable Windows host using the password supplied in the message text. The extracted document uses a template that tells potential victims to enable macros.

Shown above: Extracting the malicious TA551 Word doc from the attached zip archive.
Shown above: Screenshot of document extracted from the zip archive.
Kicking off an infection
On a vulnerable Windows host, a victim would enable macros on the extracted document. Using an example from 2021-08-10, the document dropped an HTA file in the same directory as the document. This HTA file contains HTML and script designed to retrieve a malicious DLL to infect a vulnerable Windows host with BazarLoader.
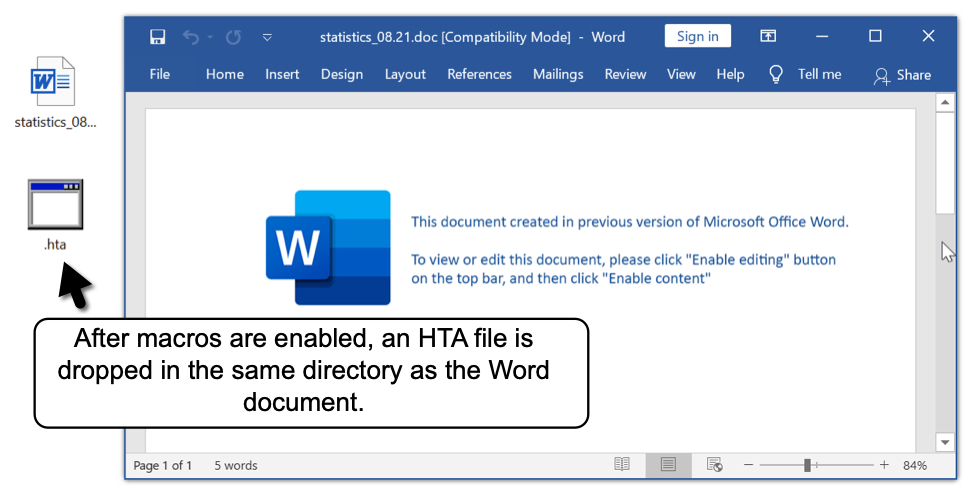
Shown above: HTA file dropped after enabling macros.
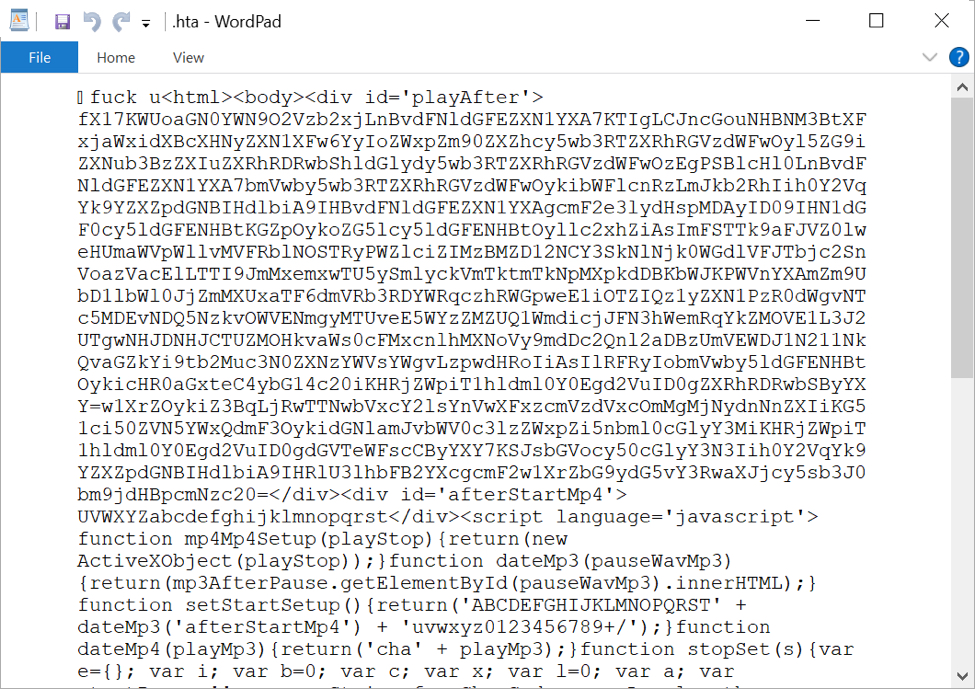
Shown above: HTA file opened in Wordpad to show some of the malicious script.
BazarLoader to Cobalt Strike
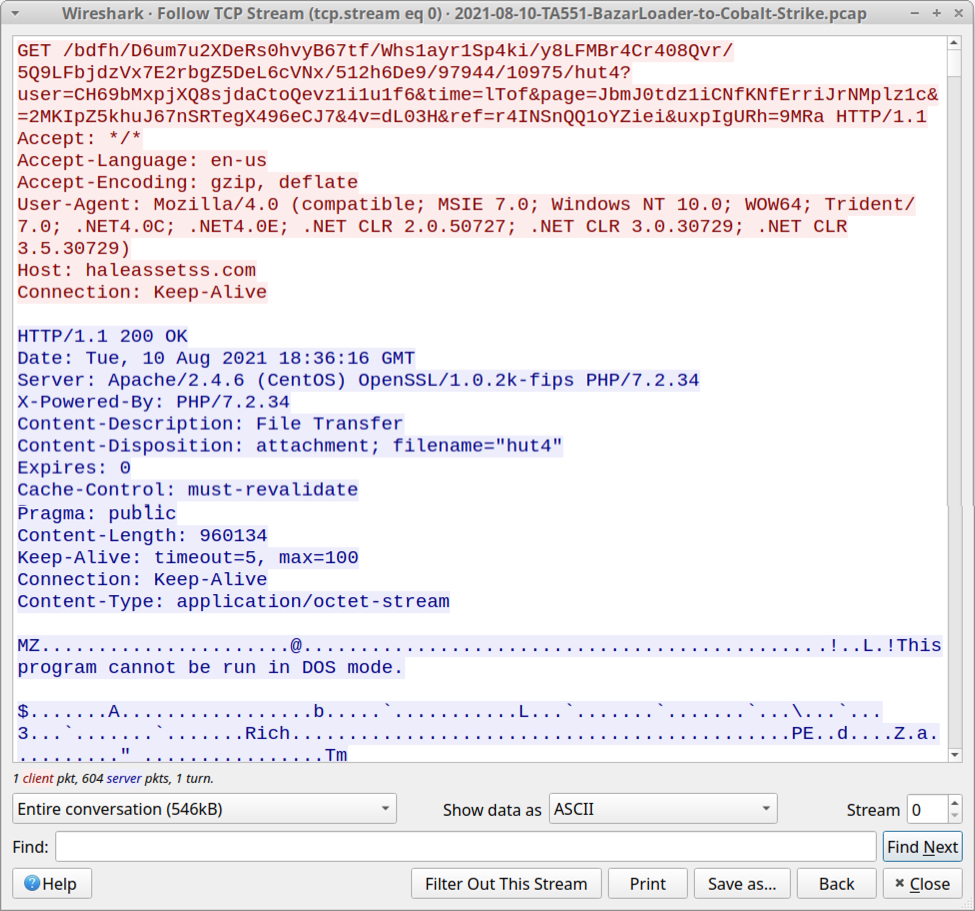
Shown above: TCP stream showing the vulnerable host retrieving a malicious DLL for BazarLoader
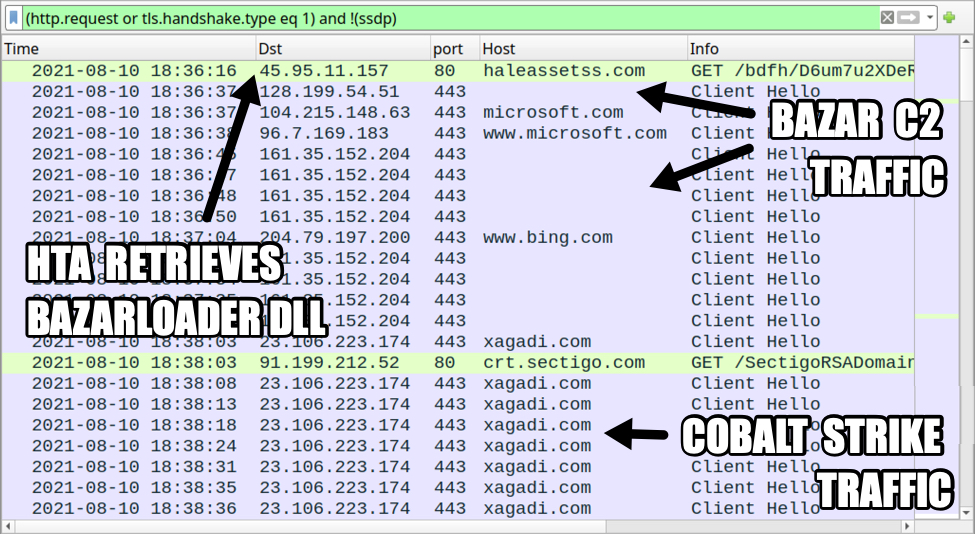
Shown above: Traffic from the infection filtered in Wireshark.
After the infected host retrieved a DLL for BazarLoader, HTTPS traffic began for Bazar Command and Control (C2) activity. A malicious DLL for Cobalt Strike was sent through Bazar C2 traffic, then HTTPS traffic to xagadi[.]com began over 23.106.223[.]174 for Cobalt Strike.
Cobalt Strike tunneling through HTTPS
In recent weeks, we've noticed HTTPS traffic acting as a tunnel for Cobalt Strike activity. Cobalt Stike URLs within this HTTPS traffic spoof commonly-used domains like bing.com or google.
Images below show decrypted HTTPS traffic from Any.Run's sandbox analysis of the Cobalt Strike binary found on our infected lab host. The pcap from this sandbox analysis has a decryption key, so we can see the actual URLs spoofing bing.com within HTTPS traffic to xagadi[.]com.
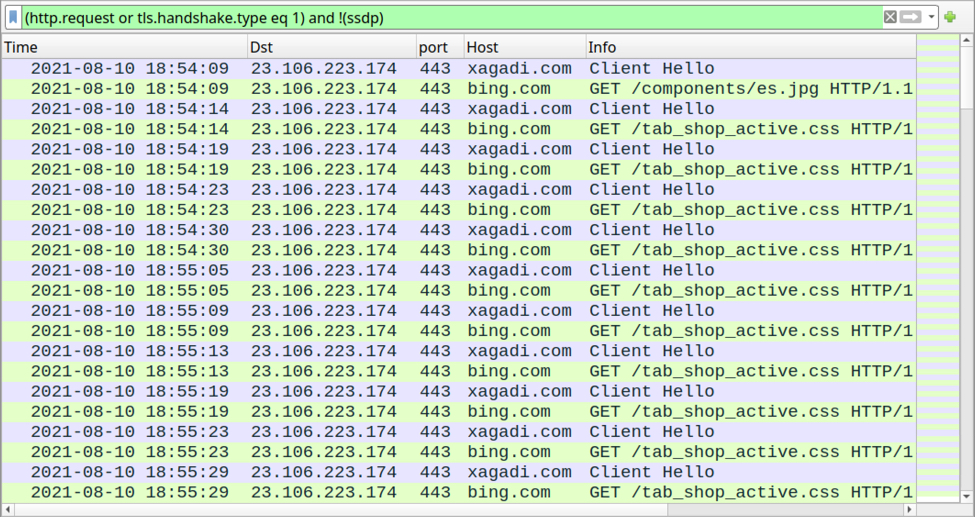
Shown above: Decrypted HTTPS traffic from any.run's sandbox analysis of Cobalt Strike sample from our infected Windows host.
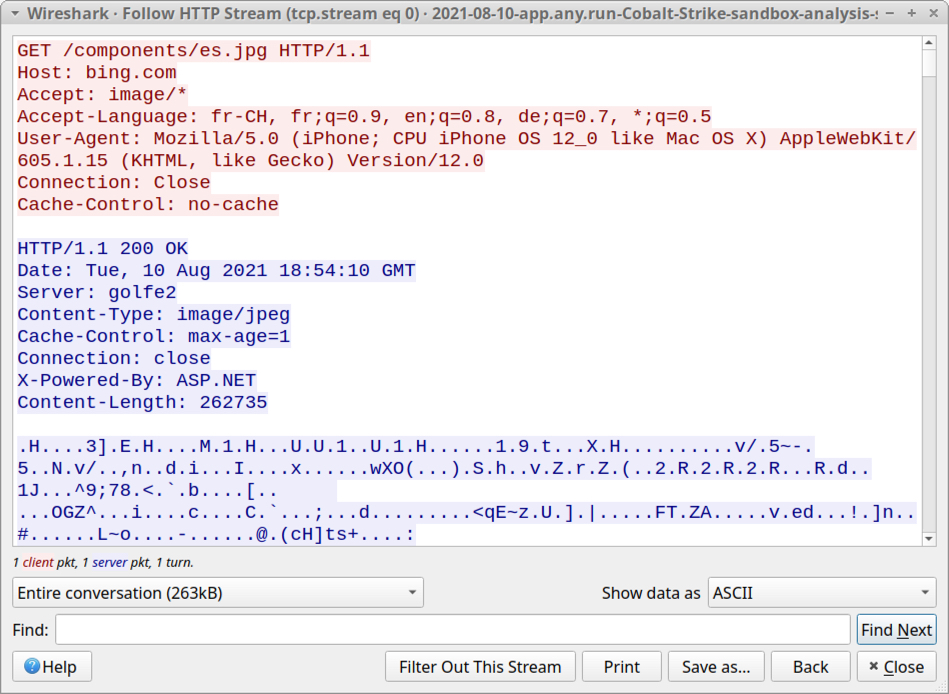
Shown above: HTTP stream for initial GET request caused by the Cobalt Strike sample.
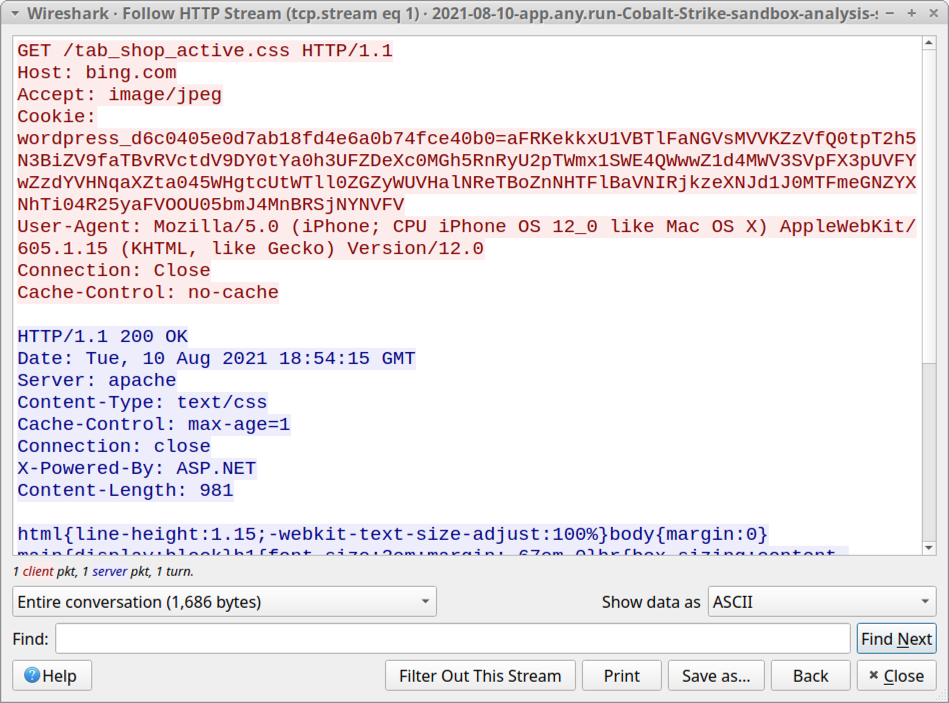
Shown above: HTTP stream for initial POST request caused by the Cobalt Strike sample.
We started seeing this HTTPS tunneling from Cobalt Strike samples this month (August 2021), but it might have started earlier. Here's a similar sample of Cobalt Stike from Monday 2021-08-09. It generated the same type of activity: URLs spoofing google.es tunneled through HTTPS traffic to gojihu[.]com and yuxicu[.]com, originally reported here.
Indicators of Compromise (IOCs)
The following are indicators of compromise from the wave of TA551 (Shathak) seen on Tuesday 2021-08-10.
10 examples of TA551 docs with macros for BazarLoader:
SHA256 hash: 03abdfb1bec53a41e952b2ecadeb2ff2c6506564507e425524f929e1c31f4147
File name: rule 08.010.2021.doc
SHA256 hash: 2222d8bee780ea651a40648ebc226b8541fcf12e686aa5a92eb558e9ab50f108
File name: instruct 08.21.doc
SHA256 hash: 42a9d7b02d5f84a43f481c981cef6a3107b6fb94fa8a03e513e4b056d37c77f8
File name: report.08.21.doc
SHA256 hash: 561459674b21852e97b6ea096765e743cec0a8d41e698ec1c9cbee4065860c32
File name: official paper-08.21.doc
SHA256 hash: 628de18eb4d1d7a66a7da82fc8b6bb20084849d3abf82ab3242843f07882f29e
File name: bid,08.21.doc
SHA256 hash: 63b3efe7c8fabbb2a40145b5895c8566c6d38989a36501c474f88ebe9b822633
File name: docs,08.010.2021.doc
SHA256 hash: 68ca31d0eab4fc980da110e4587466baa38bccd1553cb7b15bc73aee87947bc9
File name: statistics_08.21.doc
SHA256 hash: be11fbd281424569ace8deae52242d2bcd37dd731d5332b67bfdcbbfe4180e67
File name: specifics.08.21.doc
SHA256 hash: c5741adf2becca698d13c2e145aeb753b0f8a6d20ba20b5b56c521ca0dc07d87
File name: legal paper-08.21.doc
SHA256 hash: c90988e865d589eca9b278eaa270edfbd4b07bde3abc3719685f439c737a15d3
File name: material-08.21.doc
At least 6 domains hosting a malicious DLL for BazarLoader:
- 45.95.11[.]158 port 80 - cousinrentals2000b[.]com
- 45.95.11[.]151 port 80 - curtainbeild[.]com
- 45.95.11[.]157 port 80 - haleassetss[.]com
- 45.95.11[.]155 port 80 - parkerarrangeg[.]com
- 45.95.11[.]154 port 80 - operarentals2006b[.]com
- 45.95.11[.]153 port 80 - sunalvarezd[.]com
SHA256 hashes for 10 examples of .hta files:
- 075b550e1ab472416ed8cd45fda9e1ed194bbf268ea20d7b03577fb93ab11b5c
- 189f75a62956a637a9ab1bb4dbfdcbeaac9e8d6b16eddfa7d25d7cecc92e34e9
- 4d8621c7fc56bfe6b57c6b1fe305a6f7afa535fda62dee59cd1401f43e948b69
- 75e6b862569d4662d7566efa0191c2e7ca8190f5b485c6c39e2f14c72ea77c4e
- 99b2a4769b963931c29c937c5ab423bea32b787aea013a63a7d924ae480f754a
- a680355098ba1a88f4117497e215a95ac67a284b3f2561144d3afd92f795785b
- d062fca84a1027cb8beb58440b226507830eb296ea76926f43603a577e26cd74
- d6ba990044ba268188e0b289ea1fb85946c9068959ec2c445040cc18c6f940d1
- e2d52d6f12539b987113280d82297e64373841167c49fe3911d1c48ed1b9b716
- facd96aeb3e78f6b13f04b3f99cc47deaa002dd015784295420bbc80ef56f365
Location for the above .hta files:
- Dropped in the same directory as the Word document, all files named: .hta
SHA256 hashes for 10 examples of BazarLoader DLL files:
SHA256 hash: 029b714502283599a5efb86d41c48fd46751ab727b707bde620e517ec3aa3c39
File location: C:\Users\Public\installVideo.jpg
SHA256 hash: 612f74d0a1f2f90a5a4ae11889755ea68656967cf0401e15d9c375ddcfb1d9e7
File location: C:\Users\Public\mp3Mp4.jpg
SHA256 hash: 1f0f521ca8586846c9623f7bdbefbbbc84cec351ac3925dc66e8c59e44cb1713
File location: C:\Users\Public\mp4WavBefore.jpg
SHA256 hash: 3638e918a3f0dfa6a610bcf906e6bd2413be02621154800fc18a0dd15d43f142
File location: C:\Users\Public\playInstall.jpg
SHA256 hash: 36d4159d7d413fce963687f89ec4aec7ee8ab6fba05697e0ba0634db36a673a8
File location: C:\Users\Public\videoStopVideo.jpg
SHA256 hash: 41ee1d7254be06b34250d38fc6d0406a5febb22187e14fd50511e39069091391
File location: C:\Users\Public\stopStopDate.jpg
SHA256 hash: 5590123543c7e78af3c7911466b6c4147f1b39928f648a252132baf06f2b1153
File location: C:\Users\Public\videoInstall.jpg
SHA256 hash: 6ba18d4835c77ceb9dad64b870bb3becb041017c2ef59ffd417d9bcedbd1bfe5
File location: C:\Users\Public\installSetupStart.jpg
SHA256 hash: 92f08770e9d9c86ff5dc8384ca46a0bf70e407bebd4d3d5aaf5dcbcad05791d8
File location: C:\Users\Public\startMix.jpg
SHA256 hash: f4147b15de09f117235fa765c9796d6ff424f703d34acdbfcf2d1177b0f2df1a
File location: C:\Users\Public\stopPlay.jpg
Run method for the above DLL files:
- regsvr32.exe [filename]
Cobalt Strike binary from this infection:
SHA256 hash: 8438bfbb9c978de4f342a3ed19551f735343a9c1ed0c8610a332a83918cb5985
- File size: 24,064 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\382D.dll
- Run method: rundll32.exe [filename],Entrypoint
Bazar C2 traffic:
- hxxps://128.199.54[.]51/issue/web/html
- hxxps://161.35.152[.]204/issue/web/html
Cobalt Strike HTTPS tunnel:
- 23.106.223[.]174 port 443 - xagadi[.]com
URLs with spoofed domain used in HTTPS tunnel to xagadi[.]com:
- hxxps://bing[.]com/components/es.jpg
- hxxps://bing[.]com/tab_shop_active.css
Final words
For the past two months or so, I've seen more BazarLoader being pushed than ever before. BazarLoader is currently sent through at least three different campaigns:
- TA551 (Shathak) - example in this diary
- "Stolen Images Evidence" campaign - more info and a recent example here.
- BazarCall - more info here and here.
BazarLoader is commonly followed by Cobalt Strike when an infected host is part of an Active Directory (AD) environment. These infections reportedly deliver ransomware as a final payload in real-world environments (here is one such example).
But decent spam filters and best security practices can help you avoid BazarLoader. Default security settings in Windows 10 and Microsoft Office 2019 should prevent these types of infections from happening.
However, it's a "cat-and-mouse" game. Malware developers create new ways to circumvent security measures, while vendors update their software, applications, and endpoint protection to address these new developments. Furthermore, mass-distribution methods like malspam remain cheap and profitable for cyber criminals.
Malware samples from this wave of TA551 and pcaps from the associated traffic can be found at here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments
Anonymous
Aug 11th 2021
4 years ago
A colleague's Mac was infected with this Trojan recently, after she opened "report.zip" in an e-mail with the same text, yielding a password protected Word file with a similar name, and unfortunately assented to the Word dialog to enable macros.
The offending zip file and Word document were not detected by Cisco AMP for EndPoints (active on the computer) or by Malwarebytes. We notified Cisco, and it is now detected by their scanner.
A cybersecurity professional at our institution ran it in their sandbox and found that it crashed in current versions of Office. However, he could not tell us whether there would be any risk to an infected Mac (he guesses not).
Do you have any information that would speak to that?
I have not included specifics of the Trojan in the event that the actor(s) who promulgate it might be able to identify the Mac from the SHA hash, etc, and launch some sort of reprisal. I can convey these details confidentially, so long as they are not posted to your website.
Many thanks,
- bob
Anonymous
Aug 16th 2021
4 years ago
Thanks for the comment. The malware binary retrieved by the Word document's macro is Windows-specific, so it wouldn't be able to run on macOS. You shouldn't have anything to worry about if the Word document was run on a mac or macbook, as long as Windows isn't involved.
- Brad
Anonymous
Aug 16th 2021
4 years ago