Request for Packets and Logs - TCP 5358
Starting Sunday (22 Jan 17), there was a huge spike this week against TCP 5358. If anyone has logs o r packets (traffic) that might help identify what it is can submit them via our contact page would be appreciated. This is a snapshot as to what was reported so far this week in DShield.
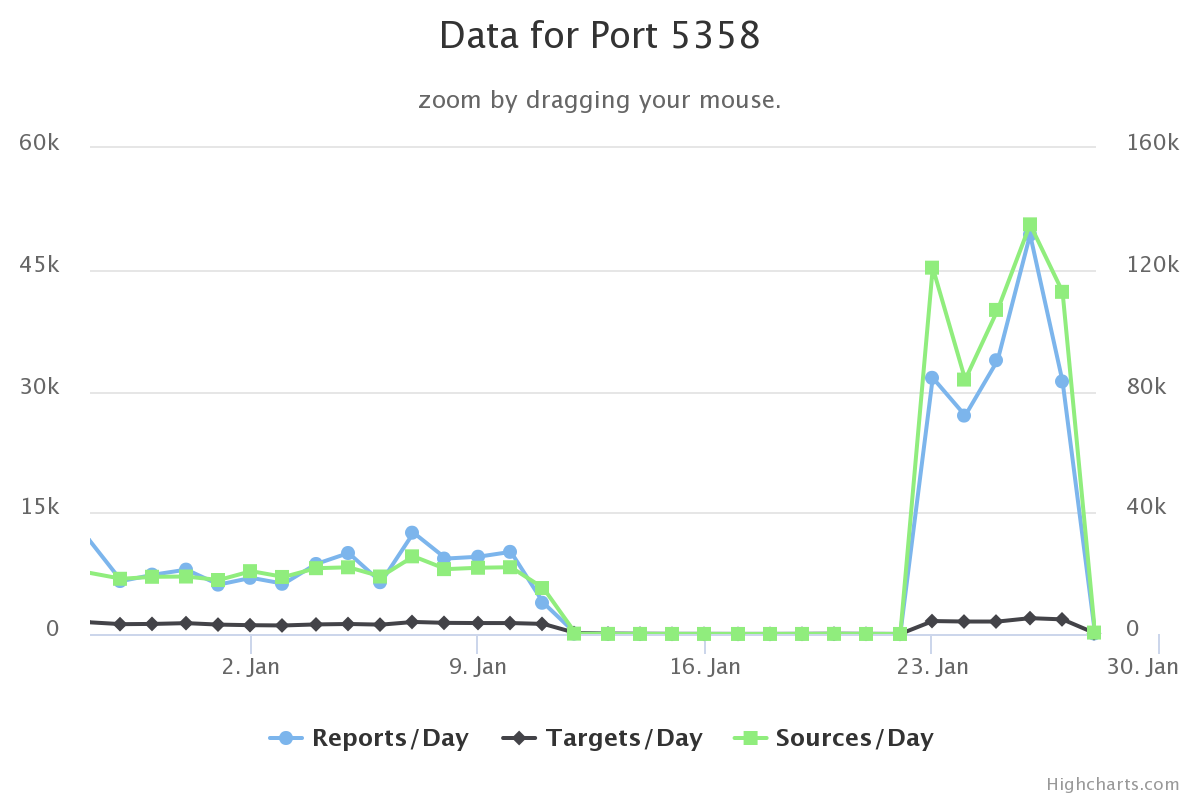
Update 1
We received information this port could be use by Web Service on Devices API (WSDAPI)[2] or potentially various version of DVR's and NVR's.
[1] https://isc.sans.edu/contact.html
[2] https://msdn.microsoft.com/en-us/library/windows/desktop/aa823078(v=vs.85).aspx
[3] https://msdn.microsoft.com/en-us/library/windows/desktop/aa385800(v=vs.85).aspx
-----------
Guy Bruneau IPSS Inc.
Twitter: GuyBruneau
gbruneau at isc dot sans dot edu
Keywords: TCP 5358 Unknown Port
2 comment(s)
×
![modal content]()
Diary Archives


Comments
Anonymous
Jan 28th 2017
9 years ago
that this is attributable to the hajime worm, a cousin of mirai.
Looks like lots of DVR devices have been hit.
Devices have a random high port open (usually >40k) where you can get the malware with netcat.
Looks like this in nmap:
==============NEXT SERVICE FINGERPRINT (SUBMIT INDIVIDUALLY)==============
SF-Port49648-TCP:V=6.47%I=7%D=2/7%Time=58999875%P=x86_64-redhat-linux-gnu%
SF:r(NULL,1104,"\x7fELF\x01\x01\x01\x03\0\0\0\0\0\0\0\0\x02\0\(\0\x01\0\0\
SF:0\x90&\x02\x004\0\0\0\0\0\0\0\x02\x02\0\x054\0\x20\0\x02\0\(\0\0\0\0\0\
SF:x01\0\0\0\0\0\0\0\0\0\x01\0\0\0\x01\0a7\x01\0a7\x01\0\x05\0\0\0\0\0\x01
SF:\0\x01\0\0\0\xfc\x06\0\0\xfc\x06\x05\0\xfc\x06\x05\0\0\0\0\0\0\0\0\0\x0
SF:6\0\0\0\0\0\x01\0\xef\x8c\xc4c\xf5\x96\xa4\xb5\xf0\x10\r\x17\0\0\0\0\xd
SF:0\xa6\x02\0\xd0\xa6\x02\0\xd4\0\0\0i\0\0\0\x0e\0\0\0\x1a\x03\0\?\x91E\x
SF:84h;\xde\xde\xa6\x0f#\xf0\xd4\$\x19u\xd8FO\xb5\xdd\xea\xce\xe0J\xbeHz!\
SF:xaeZ\t\xa1\0\xf1\xa1\+\x89~K\x0c6,\x9b\?/\]\x8aTd\x04D\x07V:\xa8\xe1\xb
SF:c\x20\xc6\x93qw&\xc1\xa4\xe2\.\xae\xb2\x0f\xd7\t\xfe\xa2\xa3\xc4\x0c\x8
SF:a\rK\xc9&0=\^J;\xbbZ\x8cb#\xe3\xce;\xc7XTN\xc0\x20\x0c\x99\x02\0\xdb#\x
SF:01\0\x0eP\0\0\x1a\x03\0\x06\xb0\x8fm\xa7\x01\xaat\x15O\xe8&\x11e\xf9\xd
SF:1\xf7\xb7A\xf6,\xa8\xd7\xbb:4\xf4\xc8\x94\x0eS\\\xd6\x10\xad\x99\xf3i!\
SF:xf9\xe4\xa7\xa1\xa5\xbd#\xdd\x90\x0e\xcdT\x87\xcb\x18\xb1@\xe1\]\r\xdc\
SF:x04\xf0\xe8cx\x833\x90f\xc2\\r\xa9\x8c\x08\xfeMX\x98\xc5\x01\xba\x0b\r\
SF:x89\x01G\xae\xf3a\x14\xd7N\xae}p'\r\x11U\xb3o\\=2\xe0\xc9Kt\xbe\x83j\xd
SF:a\xd4\x95\xf2\x15\$\xf0\xac\xdf<\x85\x83\xa9\x94<\xcd\xf2\xb7i\xa8F\x1f
SF:q\xc6S\x9b;\x80U}\xc9b\xbe1\xab8\x19z\xb9\xba\xcd\xbd\xee\x06\xc6\x89\x
SF:e4\x16\xdd\xd7\x08\xe2\xf9aX\xe8TJFT\x7fBz\xd8a\x15\"sJ\xdeV\xc7\xc5\xe
SF:8\xc4\x1e\x9d\xe445\*\x96\xb9\x19m\x9b\x07\[\x86E\x07SY\xd0\x98\x89\xfe
SF:bl\+\+\xf6\xf7\x87K2\xf4\x98Q\xd3\*\xb0qo\x91\xb6\xe1\)hg\x0b\xce\xf2\x
SF:96j>\xeb\x90\xdd\x12\x82\x94<\x18\x91\x86\xbc\xa8<\xc9}\$\xfdi\xec\xdb\
SF:x15\xb1HOJ1\x92L\xdc\xf7\xad\|\x832\xfd0\x9f\xaa\xa8\xb6\x8dx\xc2\xb1\x
SF:af\xff\.\xc6\xa7\xa3\xc4c\x16\xd0\xcdaj%\x108\xdb1\xa3\xda\xee\n\n\x84\
SF:xc1\xf1\xf0:Y/\xef\x1f\xe01\x8d\xb7\x0e\xc1\)\x87\|\x02\xb3\xaf\xff\xbd
SF:\x1dIw\xc9\xa5\x8d\?\x08\xd6\xabhA\xc7\xf4\|\x85N\"%3\x8d\xafn\x1f\xfbK
SF:\xde~V\xf7\xc3\t\xcah0\xf0\xee\xd8\x95\xc0;\[E\xb5\xb4\xa7S\xa1#}D&Q\x1
SF:6JG&\x12&\xba\x93\xe3q\xc9}\x86m\x8dbH\x9b\xa7:\xb8\x92\xa7`a\xfbJ\x16\
SF:xf6\)\x93\xf1\x02\xfa\rJ\x88K\x94\[\xc7\xe6\xce\x9dq\x9f\xe5p\xf7\x19o\
SF:x02YMj\x08\x08\x082\xa6\xf3:\xab\x0b\xc2\xdfF\x1d\xe2\x7f\x1ea/\x1br5\x
SF:b9W\xe8%2~\xb7#\x930\xf7\xdf\xe6Mb\x99\xa6\x9cM\xdb\xd4\xf0z\xe2Zt\x16y
SF:Q\xa5\x8f;!\x18\xa2\xf5r\xdcl\xc3K\xcd\xcf\x1c\x90\xe4c}s\xb9LK\x07\xb8
SF:/\xf5=\xe2\x11\x13H5\xf1\xe1\xf8\xf2\xe0\.;\x14\xfa\x0b\xc5\x06Zh\xf7\x
SF:0e\xa1\+\xbcz\xe4\xd3\t0!>\xc3\xaemf\x1d=~\xd6B\x9f:\0pT\xd7\xd3\x9a-\x
SF:bf\xe7'<A\x06\xf1\xdf\xf6\x1e\xb7TT\xc3\xccC\xb1\xfc\xd7Z\x04\xd4\xb8\x
SF:a3`\?\xec`G\x95\x18\xc6\xf0oV\x0cmf\xd9\xab\xf4\x10\xd7\xd9\xb7gs\x97\x
SF:f9\xaa>`\*\x17\xf3W\xad\xfe\x9d\x1a'\x90\x16\x11\x1e");
Anonymous
Feb 7th 2017
9 years ago