Recent example of MedusaHTTP malware
Introduction
On Monday 2019-08-12, I had captured a malware payload sent through Rig Exploit Kit (EK), and it generated post-infection traffic that I was unfamiliar with. I asked what the malware was over Twitter, and @fletchsec identified it as MedusaHTTP. Thanks to everyone who responded to my original tweet!
In 2017, Arbor Networks (now part of NETSCOUT) published a blog about MedusaHTTP using a sample originally reported by @Zerophage1337 which was also seen after an infection through Rig EK.
Today's ISC diary reviews the MedusaHTTP malware sample I found on Monday 2019-08-12.
The malware family
According to NETSCOUT, MedusaHTTP is an HTTP-based malware written in .NET used to create a distributed denial of service (DDoS) botnet. MedusaHTTP first appeared in 2017, and it's based on earlier malware called MedusaIRC. In 2017, command and control (C2) communications for MedusaHTTP were in clear text. The sample I found used base64 strings for much of its C2 traffic. Data used in the base64 strings were encoded or otherwise encrypted, so I could not determine the actual data.
Infection traffic
The image below displays traffic from the original infection on Monday 2019-08-12 filtered in Wireshark. First is Rig EK traffic, followed by post-infection traffic caused by MedusaHTTP malware.
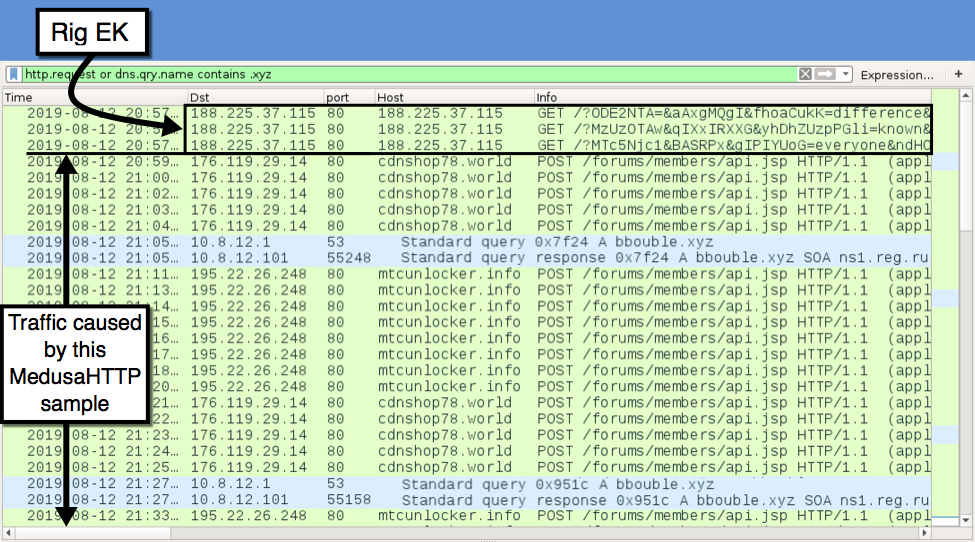
Shown above: Traffic from the original infection filtered in Wireshark.
Much like traffic from the 2017 sample, HTTP POST requests from an infected Windows host to a C2 server returned HTTP/1.1 100 Continue. The infected Windows host then sent a string starting with xyz= followed by what looks like a base64 string. During my initial infection traffic, the C2 server replied with cookie data that started with btst= and included the public IP address of the infected Windows host and some Unix-based timestamps as shown below.
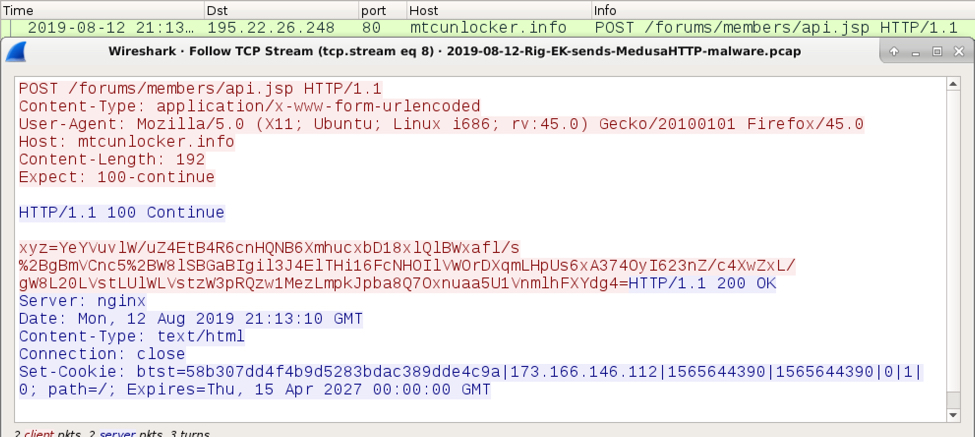
Shown above: C2 traffic generated by MedusaHTTP after my initial infection.
The base64 string in the POST data after xyz= was different for every HTTP request. Cookie data returned from the C2 server included a string of hex characters that changed with every response.
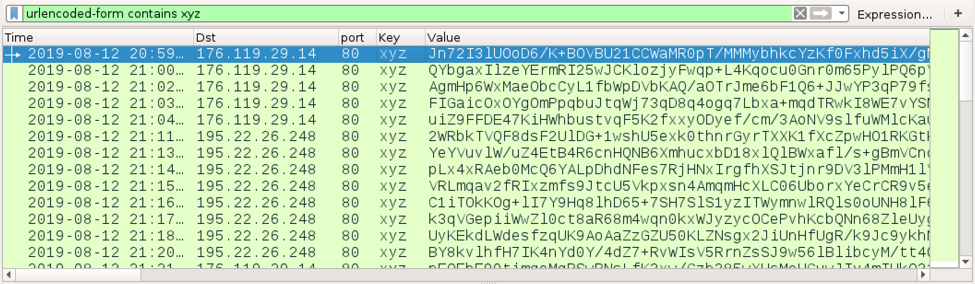
Shown above: Base64 strings after xyz= in the POST requests.
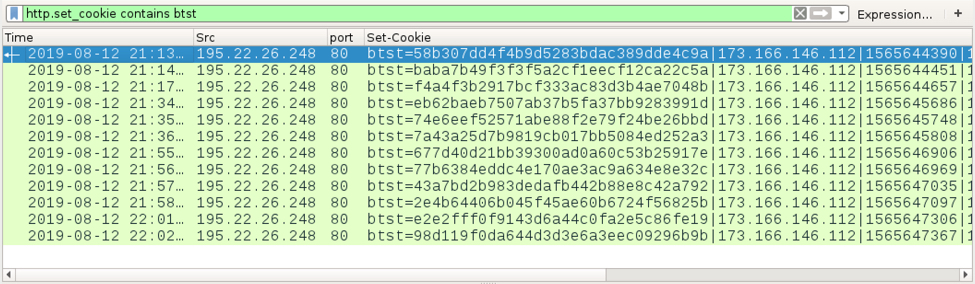
Shown above: Hex strings in cookies returned by the C2 server.
I infected another Windows host less than 24 hours after the initial infection with the same MedusaHTTP sample. This time, I saw web traffic to various casino-related domains, and the C2 server responded with data as a base64 string and no cookies.
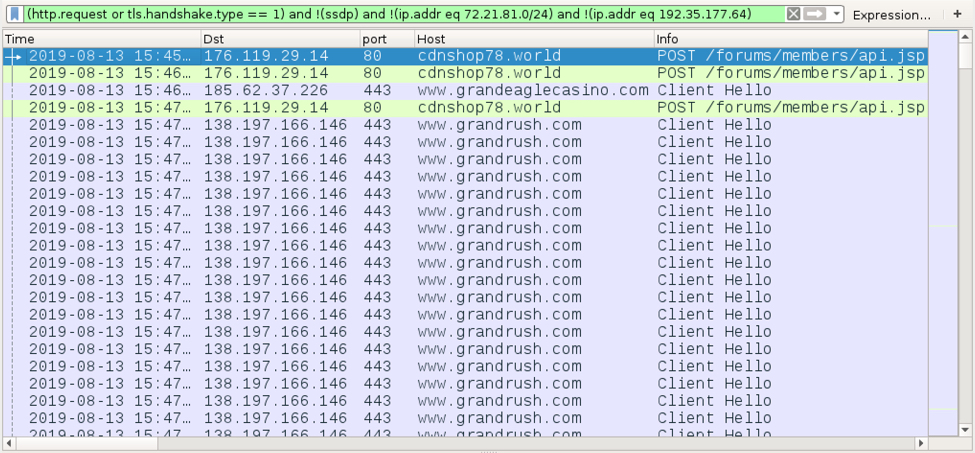
Shown above: Traffic from my follow-up infection caused by MedusaHTTP filtered in Wireshark (1 of 2).
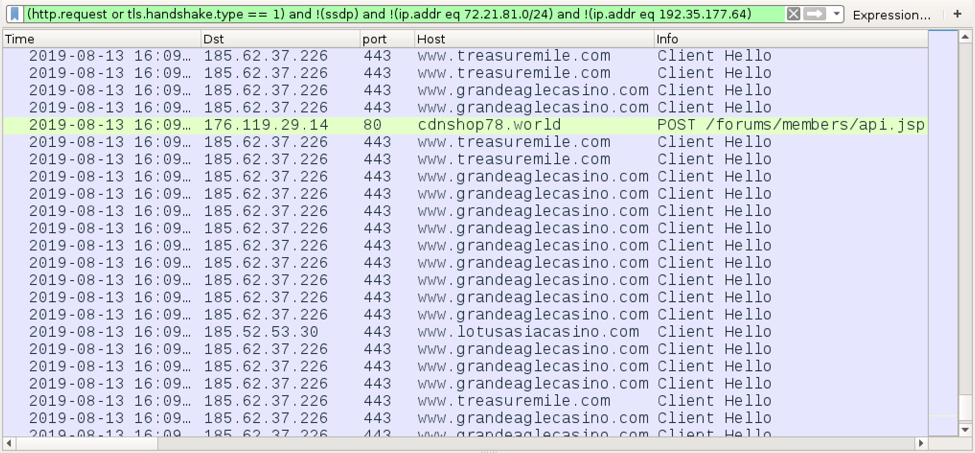
Shown above: Traffic from my follow-up infection caused by MedusaHTTP filtered in Wireshark (2 of 2).
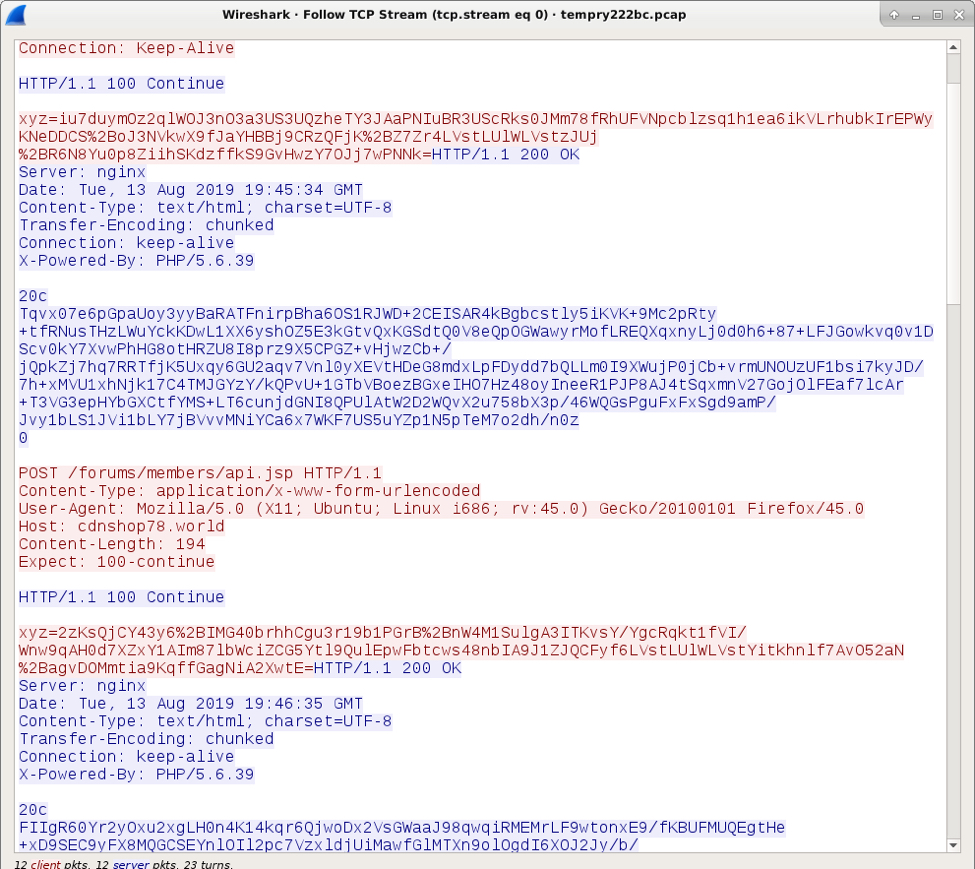
Shown above: MedusaHTTP C2 traffic from my follow-up infection.
Post-infection forensics
MedusaHTTP updates the Windows registry to maintain persistence after a reboot. The EXE for MedusaHTTP was saved under the infected user's AppData\Roaming folder.
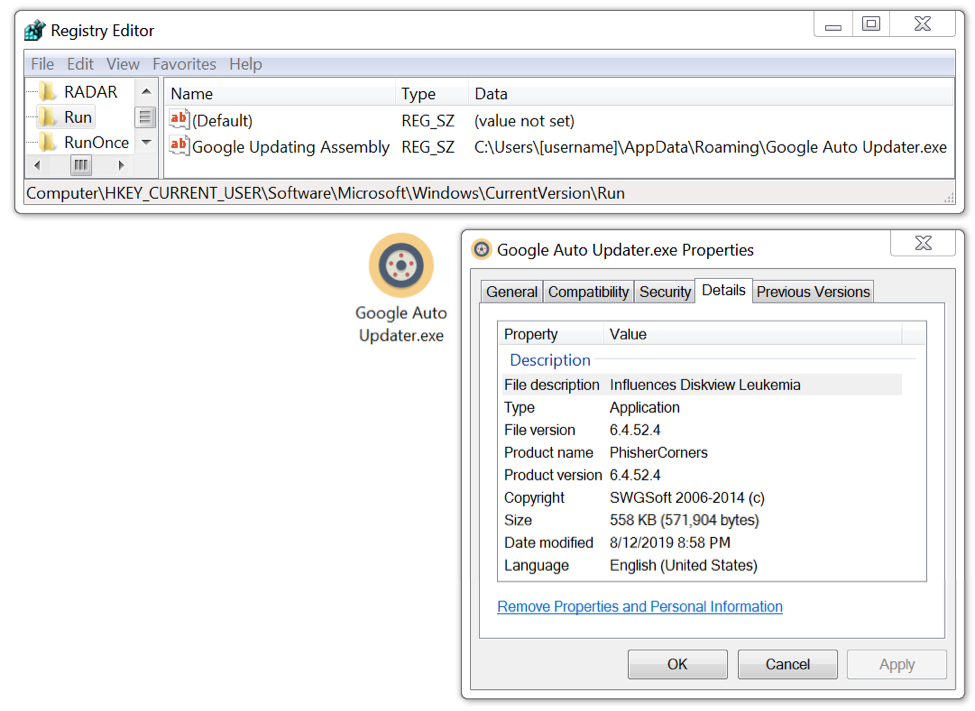
Shown above: MedusaHTTP malware persistent on my infected Windows host.
Indicators of compromise (IoCs)
SHA256 hash: 17901948c9c9f2f0d47f66bbac70592a7740d181f5404bf57c075ed6fa165b67
- File size: 571,904 bytes
- File location: C:\Users\[username]\AppData\Roaming\Google Auto Updater.exe
- File description: MedusaHTTP malware persistent on an infected Windows host
Post-infection C2 traffic:
- 176.119.29[.]14 port 80 - cdnshop78[.]world - POST /forums/members/api.jsp
- 195.22.26[.]248 port 80 - mtcunlocker[.]info - POST /forums/members/api.jsp
- DNS queries for bbouble[.]xyz - Standard query responses: A bbouble[.]xyz SOA ns1.reg.ru
Final words
This specific sample of MedusaHTTP appears to be targeting casino domains. Since MedusaHTTP is DDoS botnet malware, web traffic to casino domains from my infected Windows host was likely targeting these domains in conjunction with other infected Windows hosts.
Pcaps and malware for this diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments