Recent Dridex activity
Introduction
This week, I've seen a lot of malicious spam (malspam) pushing Dridex malware. Today's diary, provides a quick rundown on the types of malspam I've seen, and it also covers what an infected Windows host looks like.
The malspam
I've seen at least 3 different themes used during the first two days of this week from malspam pushing Dridex. One was a voicemail-themed email. Another used a DHL them. Finally, I saw a FedEx-themed email pushing Dridex. See the images below for examples.
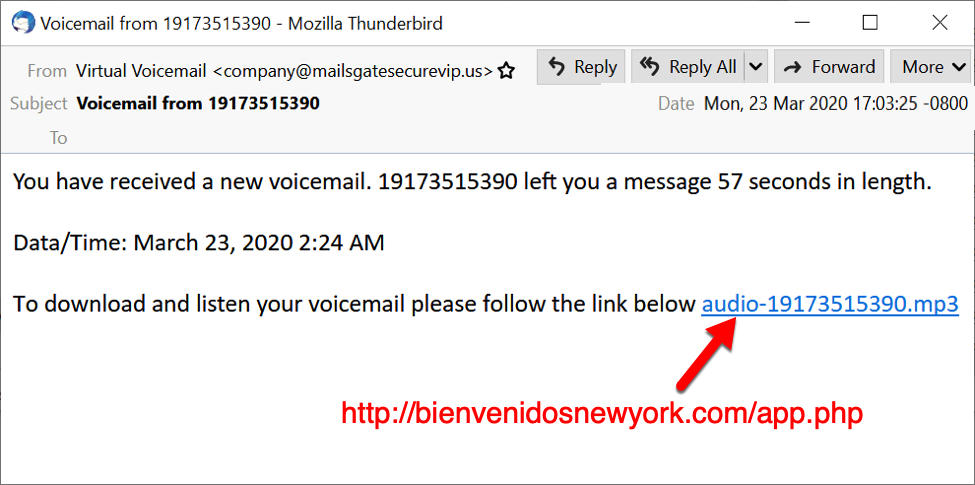
Shown above: Malspam using a voicemail theme to push Dridex.

Shown above: Malspam using a DHL them to push Dridex.
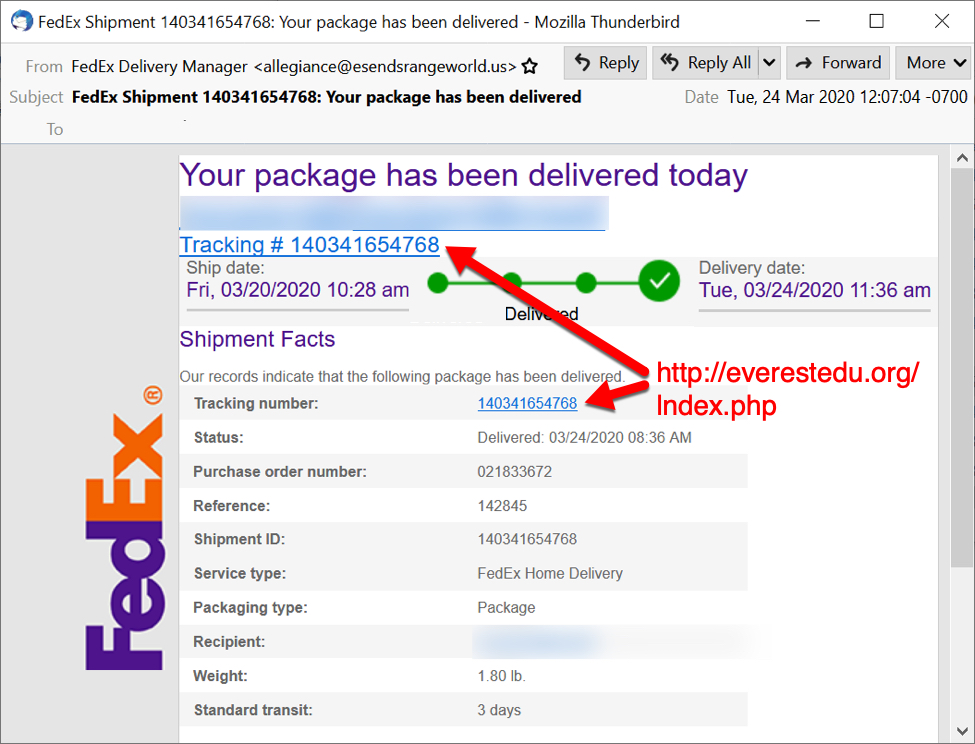
Shown above: Malspam using a FedEx theme to push Dridex.
An infected Windows host
I infected a lab host using a URL from one of the emails shown above. See images below for details.
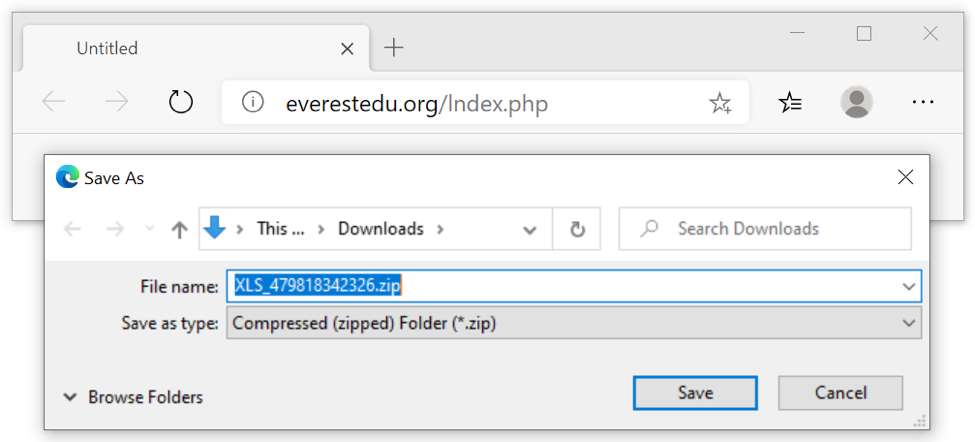
Shown above: Clicking on the link in the Fedex email.
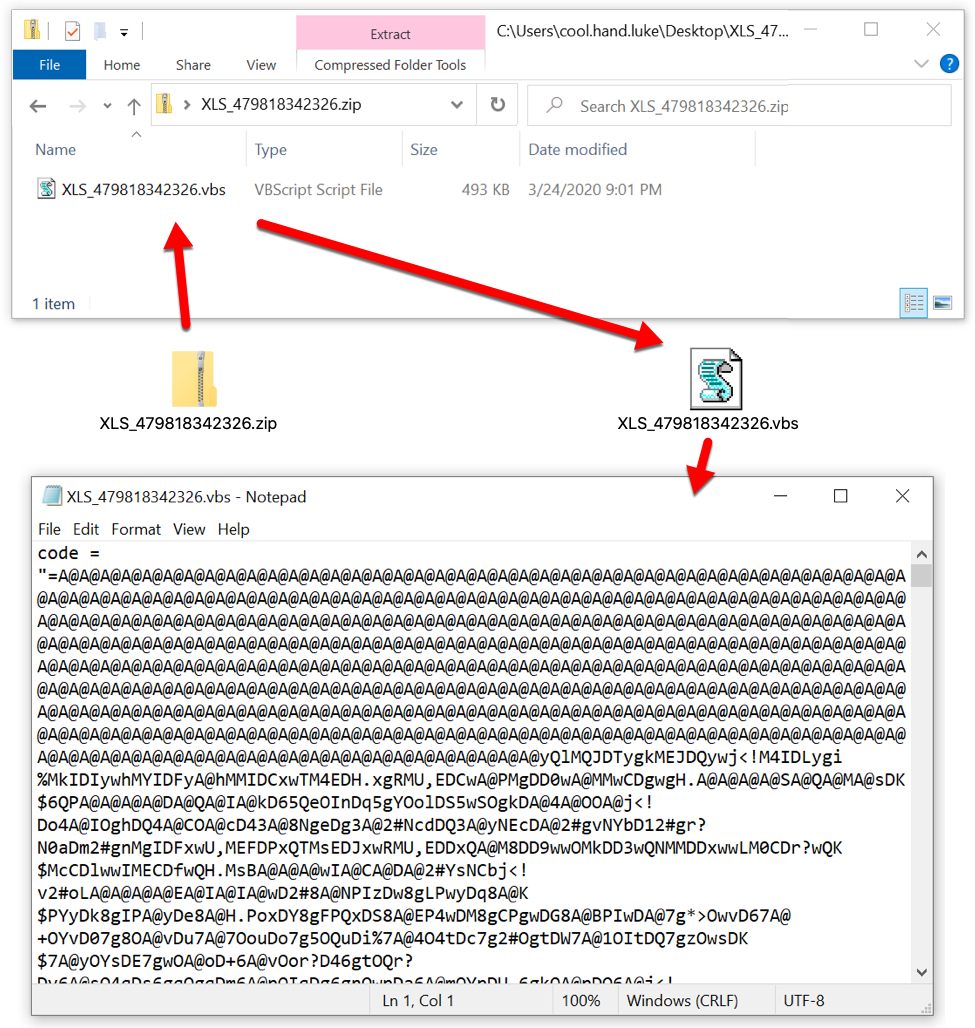
Shown above: Extracting a VBS file from the downloaded zip archive.
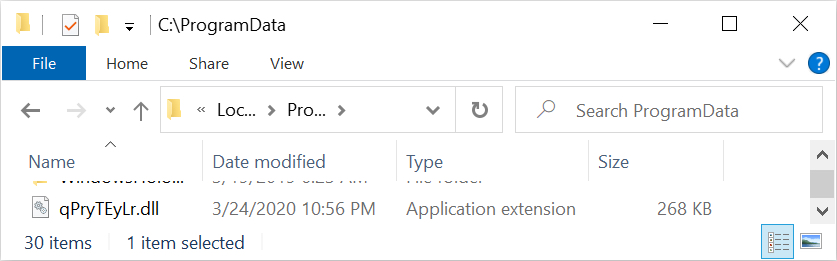
Shown above: Running the VBS file drops the initial DLL for Dridex.
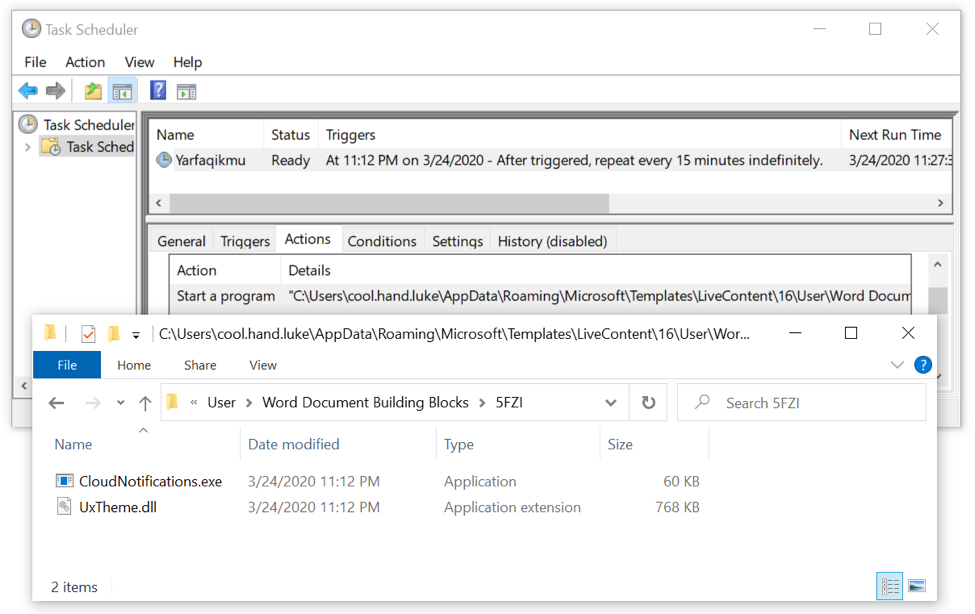
Shown above: Dridex persistence mechanism 1 of 3--a scheduled task.
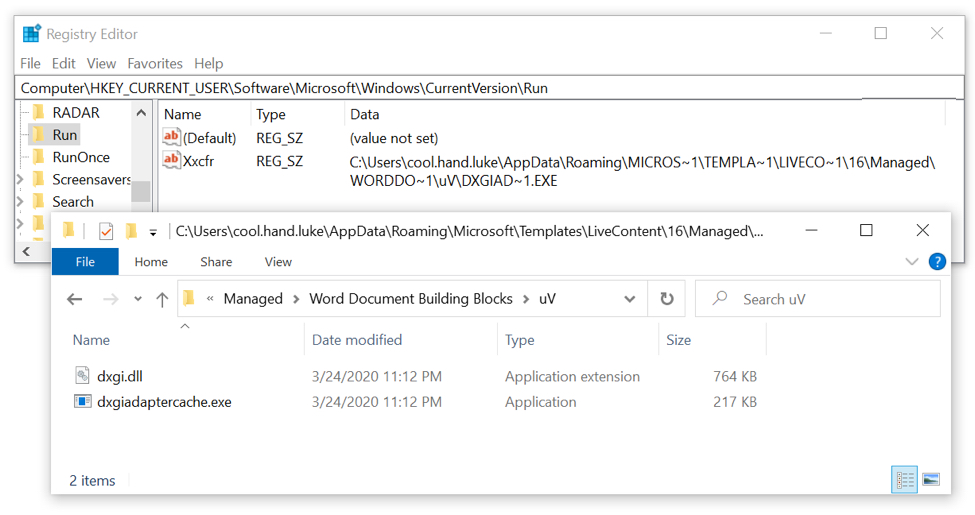
Shown above: Dridex persistence mechanism 2 of 3--a regisrty update.
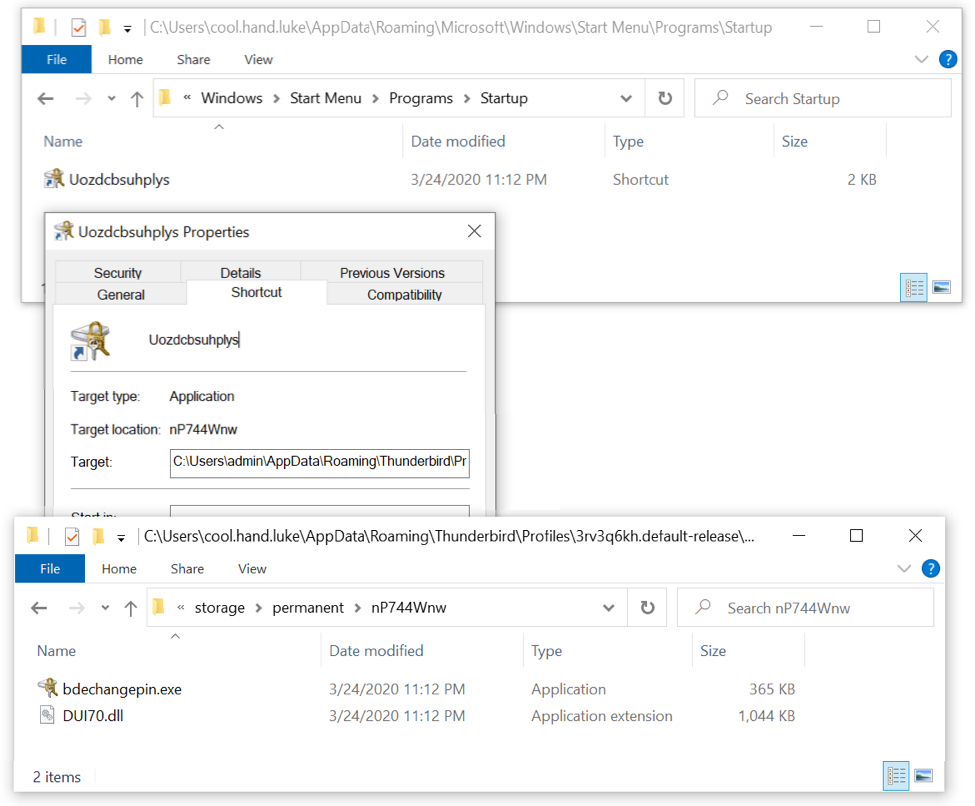
Shown above: Dridex persistence mechanism 2 of 3--a shorVcut in the Windows startup menu.
Indicators
URLs from the three email examples:
- hxxp://bienvenidosnewyork[.]com/app.php
- hxxp://photoflip[.]co[.]in/lndex.php
- hxxp://everestedu[.]org/lndex.php
Zip archive downloaded from link in one of the malspam:
- SHA256 hash: fc3da99b3bfd3fee81361dd0795e24f24a6b1362629ddc2e98b7d1490b0b4598
- File name: XLS_479818342326.zip
VBS file extracted from the above zip archive:
- SHA256 hash: cc1b8318bd30fa4f03e333ad34ae153ef3b5e42cbce95299d566ad755391313f
- File name: XLS_479818342326.vbs
Initial Dridex DLL seen after running VBS file:
- SHA256 hash: abf99a028dae6812f6f0ca633d7424ce9272dfcfbebf6b518c1e6c97f872f3e7
- File location: C:\ProgramData\qPryTEyLr.dll
File hashes for Dridex DLLs made persistent during the infection:
- SHA256 hash: 6712500bb0de148a99ec940160d3d61850e2ce3803adca8f39e9fa8621b8ea6f
- File name: DUI70.dll
- SHA256 hash: 86bcfce2dd342e9a1c04cfc65731d40ed1c397a4ec47bd9f5b41771297d81100
- File name: UxTheme.dll
- SHA256 hash: 005e77a55b8f1bf4049d6231c2349a01d019b46f47b6930103458a2aadd1bfa6
- File name: dxgi.dll
Final notes
Of note, zip archives from links in the emails appeared to be different names/sizes/hashes each time I downloaded one, even if it was from the same link. Also, when a Dridex-infected Windows host is rebooted, the locations, names, and file hashes of the persistent Dridex DLL files are changed.
Dridex remains a feature of our threat landscape, and it will likely continue to be, at least in the foreseeable future. Windows 10 hosts that are fully patched and up-to-date have a very low risk of getting infected from Dridex, so it pays to follow best security practices.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments