Ransomware as a Service
Hunting on the dark web is interesting to find new malicious activities running in the background. Besides the classic sites where you can order drugs and all kind of counterfeited material, I discovered an interesting website which offers a service to create your own ransomware! The process is straightforward, you just have to:
- specify your Bitcoin address to get the ransom,
- select the amount (minimum amount is 0.01 BTC, max 1BTC)
and you get a nice malicious PE file delivered a few seconds later:
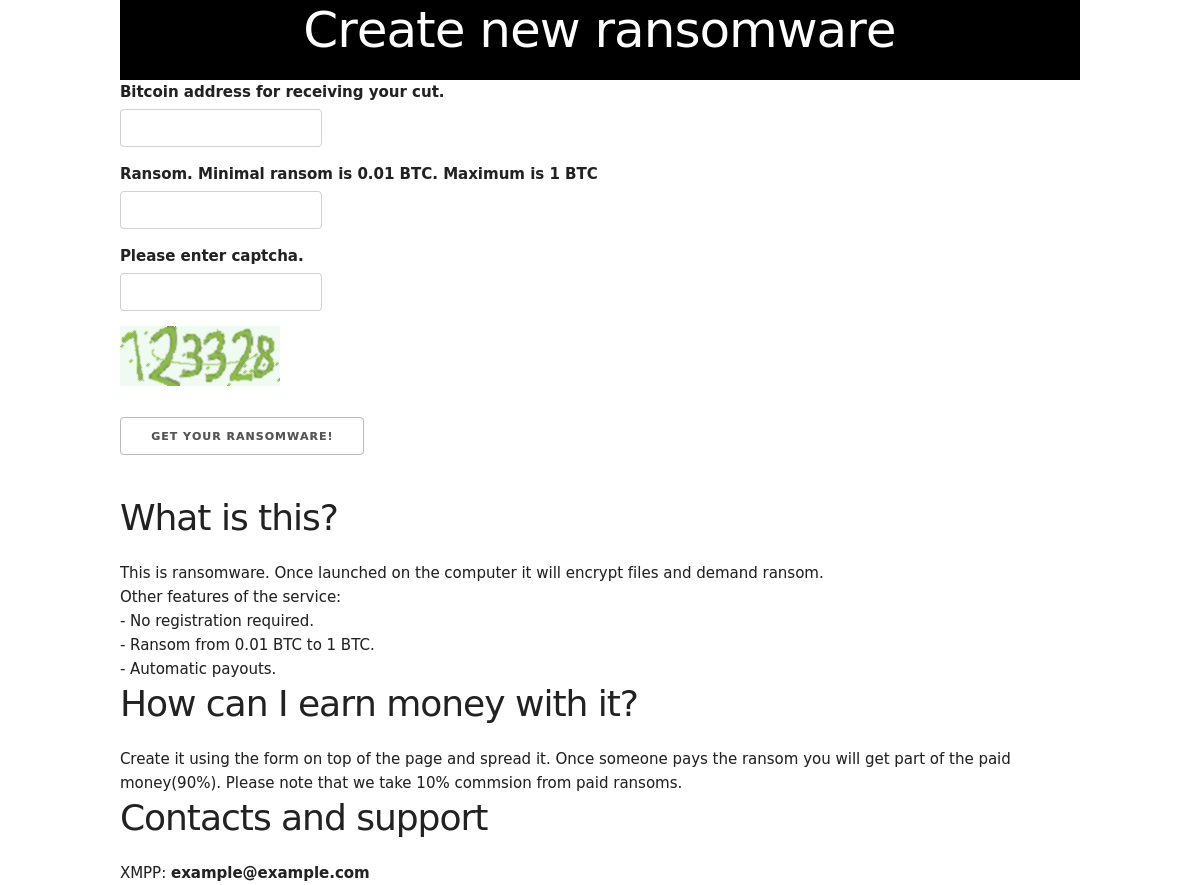
The business model behind the service is simple: the bad guys keep 10% of the ransom.
Based on the strange XMPP address provided on the webpage, I think that the service is not yet available or is just a proof of concept. However, it was really tempting so I generated my own ransomware sample. Note that a valid Bitcoin address must be provided. Thanks to Google, I found some “public” ones that I used for my test. The generated files is a 64bits PE file. I don’t know the reasons of this restriction.… 64 bits only is a real limitation to hit many victims.
+----------+----------------------------------------------------------------------------------------------------------------------------------+ | Key | Value | +----------+----------------------------------------------------------------------------------------------------------------------------------+ | Name | YzBvIyROuOZGbcf6sFl8CKGQzqDgbb7Rzua.exe | | Tags | ransomware, isc | | Path | /home/nonroot/workdir/binaries/7/0/0/5/7005535e034576fdb66b5b32eb198b48d7755758e77bd66909f8dd7288c1e069 | | Size | 5580288 | | Type | PE32+ executable (GUI) x86-64 (stripped to external PDB), for MS Windows | | Mime | application/x-dosexec | | MD5 | 493640f022a7ac07ad4e8d6f2cd3740e | | SHA1 | 4c4a1df308e415ab356d93ff4c5884f551e40cf5 | | SHA256 | 7005535e034576fdb66b5b32eb198b48d7755758e77bd66909f8dd7288c1e069 | | SHA512 | d29b40298f00ba619a59f4aa7cec1bb1ec753df948b9fa50e7e158150ca21801783d701c8ed32a8e3811f138ad948b4077c8cf2b7da5b25917ec8eebe7435c26 | | SSdeep | 49152:U6q9fOpwcf1pHot9E4IaCf1kin7N0Iu1YES/N4ggvewaFSenC00qTQeVptYt1dmT:ofk3oC9n7N0Iu19SV4ISeLQevtYVmS | | CRC32 | 29B4ED1C | | Parent | | | Children | | +----------+----------------------------------------------------------------------------------------------------------------------------------+
The file hash was of course unknown on VT. When I submitted it, the score was only 7/66[1]. This is quite good (from the attacker perspective). No big player was able to detect it.
I tested the ransomware in a sandbox running a Windows 7 64bits protected by the Microsoft AV and all security features enabled. A few minutes later, my files were encrypted.
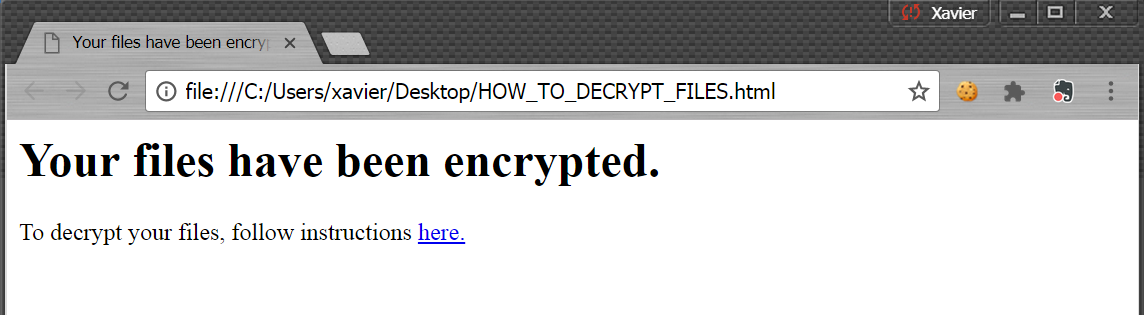
The communication with the victim is performed via a file on the desktop:
When you click on the link to are redirected to a website which discloses more details:
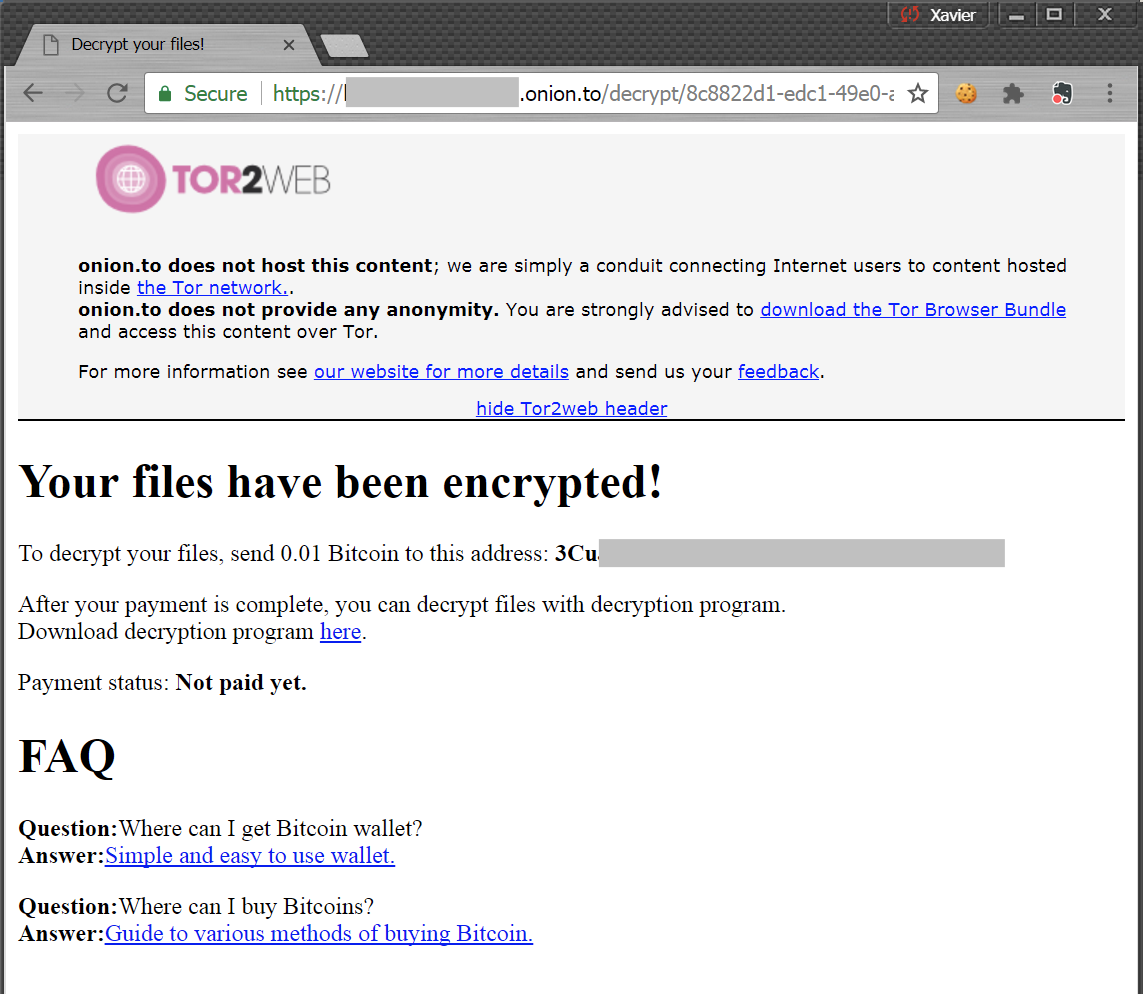
The webpage proposes to downloaded a decryption tool: +----------+----------------------------------------------------------------------------------------------------------------------------------+ | Key | Value | +----------+----------------------------------------------------------------------------------------------------------------------------------+ | Name | decrypter.exe | | Tags | ransomware, isc | | Path | /home/nonroot/workdir/binaries/c/b/7/3/cb73927aa749f88134ab7874b15df898c014a35d519469f59b1c85d32fa69357 | | Size | 5605888 | | Type | PE32+ executable (GUI) x86-64 (stripped to external PDB), for MS Windows | | Mime | application/x-dosexec | | MD5 | 3eadfae2ff4c4eb1c8e6ad48efdfff21 | | SHA1 | 5845d32cfae8f554847fa95d28d5c6849c416b84 | | SHA256 | cb73927aa749f88134ab7874b15df898c014a35d519469f59b1c85d32fa69357 | | SHA512 | 62efa2e1c8a8530b076b54e0e431492bf6a1d9d42addca8f95db1a1fce82e4288afe79a585d61831fc3d76f0d705b98324dc35e353cd19692779a3a8916f421f | | SSdeep | 49152:ymdRKnjBwhy1Bz/0RvVJr7eUBUr6DXxgqw5PgAXzzX691yW/0qTQN9sUL2z47tQ+:9RZaMoAxgqw5x691JQNmULd5L | | CRC32 | 9D8D2721 | | Parent | | | Children | | +----------+----------------------------------------------------------------------------------------------------------------------------------+
Communications with the C2 server are performed via HTTPS: kdvm5fd6tn6jsbwh[.]onion[.]to (185[.]100[.]85[.]150) located in Romania.
The encryption key is downloaded and stored in %APPDATA%\encryption_key
Here is a dump of the file I received:
00000000: 2455 e231 0f56 cae2 3bad 8fe7 a116 3a67 $U.1.V..;.....:g
00000010: 50b7 f761 2bcb 237a 4634 6fbc fd01 12f0 P..a+.#zF4o.....
00000020: e38f 6bbf 7b74 46f1 6b4f 7235 a44e b1e1 ..k.{tF.kOr5.N..
00000030: 5ce7 51a1 8b46 22fc 3e45 9e68 cc35 2613 \.Q..F".>E.h.5&.
00000040: 78bc 2a60 071c 9955 7aa5 8bd5 3161 d86d x.*`...Uz...1a.m
00000050: 5939 770a 2321 1815 4372 c307 5f6c e6c7 Y9w.#!..Cr.._l..
00000060: 0023 73e7 bcb6 2c08 545c 07c0 b5ce 437a .#s...,.T\....Cz
00000070: 332c 4f48 88d8 62d7 771d 45ce c24c 230a 3,OH..b.w.E..L#.
00000080: 57e3 de14 bf83 4931 673f e47f 5f71 f337 W.....I1g?.._q.7
00000090: fd57 e3f7 99c0 7fad 31da 2965 e9a1 a993 .W......1.)e....
000000a0: 16de aca8 eae6 9003 d0b3 186c 45c6 bced ...........lE...
000000b0: c10a 76ae aaa5 b699 8a1e fd51 bc06 993a ..v........Q...:
000000c0: 9dda 14e7 cfe1 67f1 e135 c9ad 1f69 850e ......g..5...i..
000000d0: 370c 0f50 16e6 8604 23bc fabb 6eee 3a1a 7..P....#...n.:.
000000e0: b3a5 655d 9327 2a4f fe75 c6d2 b2cb a192 ..e].'*O.u......
000000f0: ba87 6e06 02ca f460 8fbf ee4f 6ab4 f74c ..n....`...Oj..L
The PE file is not obfuscated and interesting strings can be found like the list of file extensions that I scanned to be encrypted:
*.arw*.bay*.cdr*.cr2*.crw*.csv*.dcr*.dng*.doc*.dwg*.dxf*.erf*.jpg*.kdc*.mef*.mrw*.nef*.nrw*.orf*.pdf*.pef*.png*.ppt*.psd*.ptx*.r3d*.raf*.raw*.rtf*.rw2*.rwl*.sr2*.srf*.srw*.svg*.txt*.xls
The following drives are tested to find network shares:
K:, L:, M:, N:, O:, P:, Q:, R:, S:, T:, U:, V:, W:
Encrypted files have a new extension ‘.cypher’. Based on the strings present in the PE file, it has been written in Go. Do you have more information about this kind of ransomware? (".cypher"), please share!
Xavier Mertens (@xme)
ISC Handler - Freelance Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments