Quick Status of the CAA DNS Record Adoption
In 2017, we already published a guest diary[1] about "CAA" or "Certification Authority Authorization". I was curious about the status of this technique and the adoption level in 2020. Has it been adopted massively since this diary? The initial RFC describing CAA has been issued in 2013 (RFC6844[2]). Since 2019, it is obsolete and has been replaced by RFC8659[3]. Just a quick reminder about the purpose of this DNS record. It is used to specify which certificate authority(ies) (CAs) is(are) allowed to issue certificates for a domain. When the first diary was posted, not all DNS query tools supported CAA records by default. It was often required to query for a 'type257' record, then decode the output. Today, all tools support it pretty well:
$ dig rootshell.be caa ; <<>> DiG 9.10.6 <<>> rootshell.be caa ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 50111 ;; flags: qr rd ra; QUERY: 1, ANSWER: 1, AUTHORITY: 13, ADDITIONAL: 1 ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ;; QUESTION SECTION: ;rootshell.be. IN CAA ;; ANSWER SECTION: rootshell.be. 60 IN CAA 0 issue "letsencrypt.org" ;; AUTHORITY SECTION: . 3499 IN NS k.root-servers.net. . 3499 IN NS h.root-servers.net. . 3499 IN NS c.root-servers.net. . 3499 IN NS f.root-servers.net. . 3499 IN NS b.root-servers.net. . 3499 IN NS g.root-servers.net. . 3499 IN NS j.root-servers.net. . 3499 IN NS l.root-servers.net. . 3499 IN NS d.root-servers.net. . 3499 IN NS a.root-servers.net. . 3499 IN NS i.root-servers.net. . 3499 IN NS e.root-servers.net. . 3499 IN NS m.root-servers.net. ;; Query time: 48 msec ;; SERVER: 192.168.254.130#53(192.168.254.130) ;; WHEN: Thu Oct 29 16:56:51 CET 2020 ;; MSG SIZE rcvd: 286
This output means, based on the value of CAA record, that only letsencrypt.org is authorized to generate certificates for the domain rootshell.be (and its subdomains). As the RFC says: "CAA Resource Records allow a public CA to implement additional controls to reduce the risk of unintended certificate mis-issue". Great!
If it's so easy to implement, we can presume that most of the registered domains on the Internet have a CAA record, right? To verify this, I downloaded a copy of the good old Alexa top-1 million domains list. The list is not free anymore but it’s possible to find old versions. For all those domains, I tried to resolve potential CAA records then I generated some statistics. I wrote a quick script to automate this task. At the end of the execution, it resolved 744060 domains. Let's have a look at the numbers.
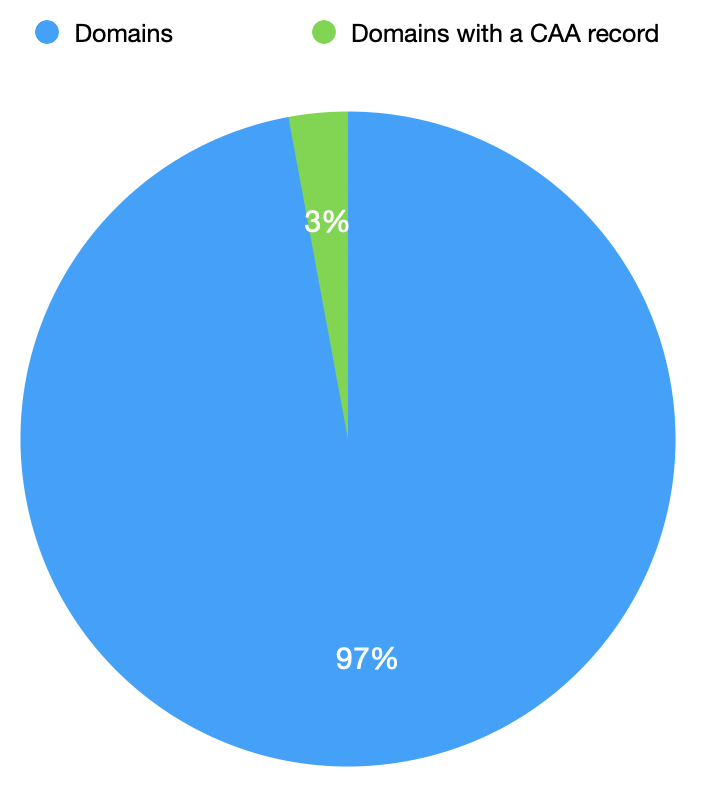
It's quite surprising that, still today, only 3% of the domains listed in the Alexa list implemented a CAA record.
They are 3 CAA 'properties' available:
- "issue" : Grant authorization to issue certificates related to the domain.
- "issuewild" : Grant authorization to issue wild certificates related to the domain.
- "iodef" : Specifies a means of reporting certificate issue requests or cases of certificate issue.
Here are the number of each property found:
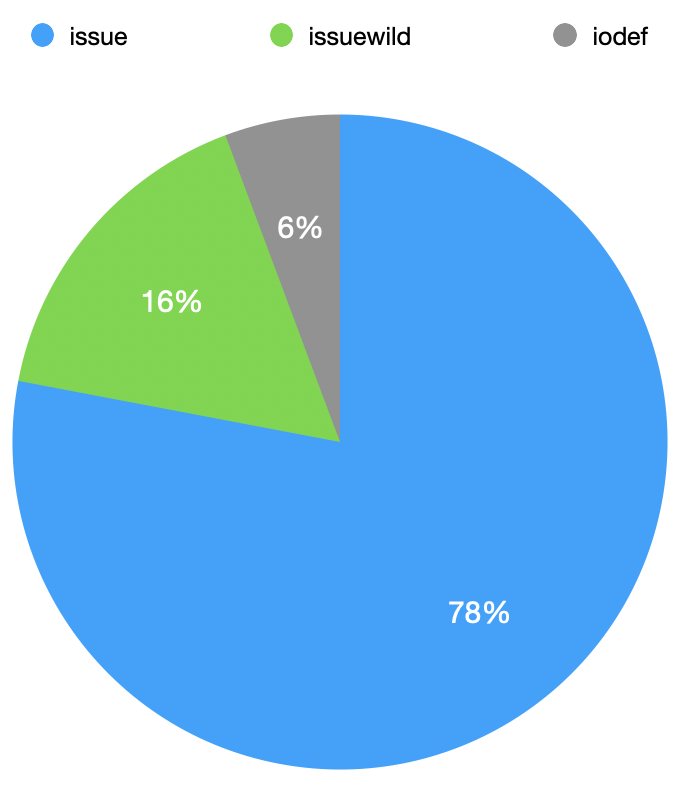
The property issue may contain one of more certificate authorities (separated with a ';') but it's also possible to give a single ';' character. Is this case, it means that NO certificate authority is allowed to generate a certiicate for the domain. I found 358(!) of such domains. (lun.com is one of these domains).
Now, let's have a look at the CA landscape. What are the most used?
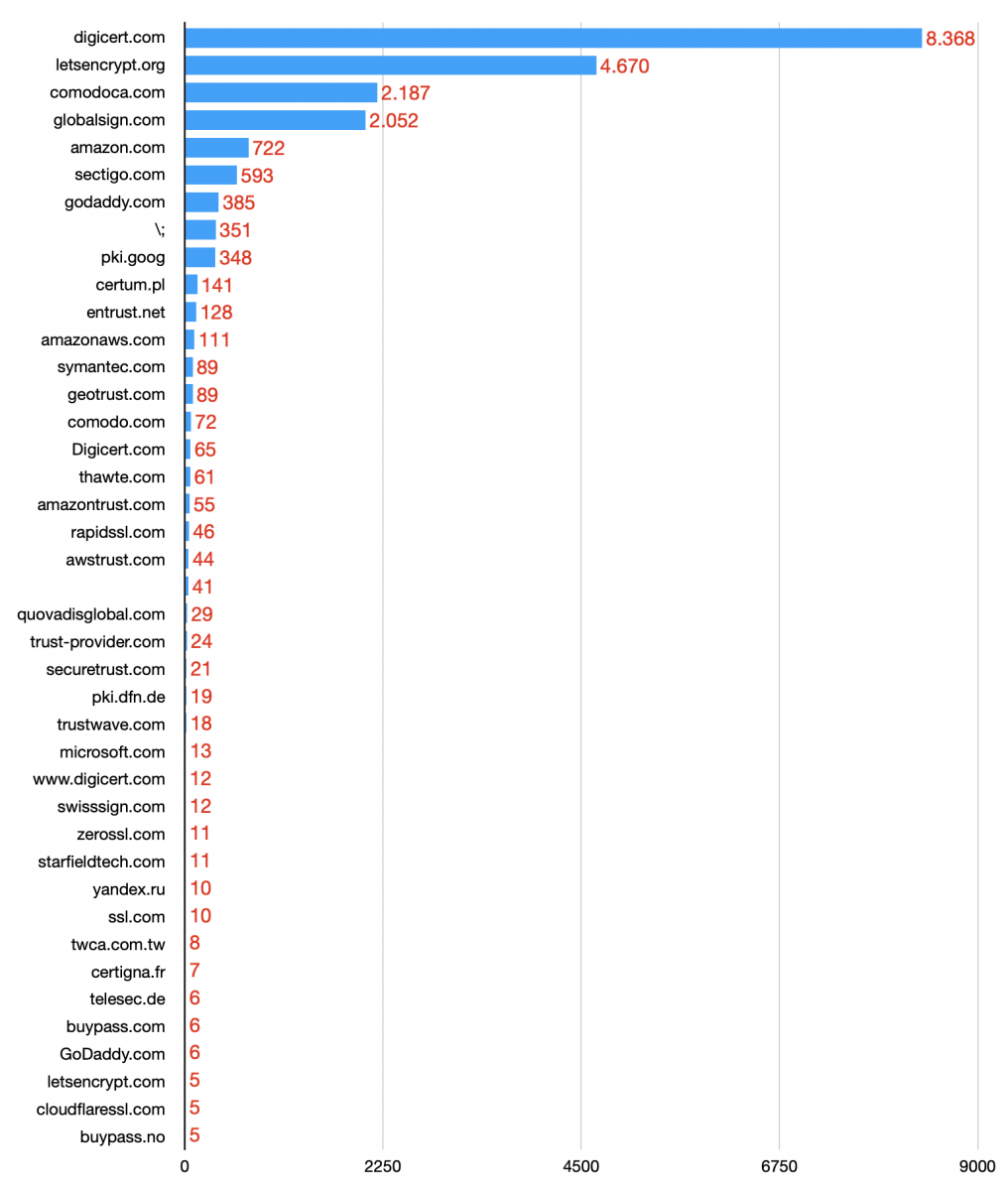
Note: To reduce the graph size, the listed CA are those that were used at least 5 times.
No surprise, we see Digicert and Let's Encrypt at the top. This CA has been adopted by many organisations or private people to generate free certificates. It is very popular also for attackers because it helps them to improve the quality of their phishing sites (just an example).
But, is Let's Encrypt also popular amongst the top domain owners? Let's have a look. Again, from the Alexa list, the first domain that returned a CAA record mentioning letsencrypt.org was at position 187 (deepl.com). It accepts two CA's:
;; ANSWER SECTION: deepl.com. 300 IN CAA 0 issue "letsencrypt.org" deepl.com. 300 IN CAA 0 issue "sectigo.com"
Let's draw the same graph has above but only for the 187 first domains who have at least one CAA record.
.png)
You can see those most popular websites do not use Let's Encrypt and prefer to rely on "popular" CA's or, like the monster Google, rely on your own.
If you did not implemented yet a CAA record, have a look at it. It's easy and most DNS providers support them out of the box. You should be able to create them in your classic DNS management interface.
[1] https://isc.sans.edu/forums/diary/CAA+Records+and+Certificate+Issuance/22342
[2] https://tools.ietf.org/html/rfc6844
[3] https://tools.ietf.org/html/rfc8659
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments