Port 3389 / terminal services scans
Thanks to Pat for pointing out a sharp increase in the number of sources scanning for port 3389 [1].
Port 3389 / TCP is used by Microsoft Terminal Services, and has been a continuing target of attacks. If you have any logs you want to share, please submit them via our contact page . In particular if you observed anything different the last couple days.
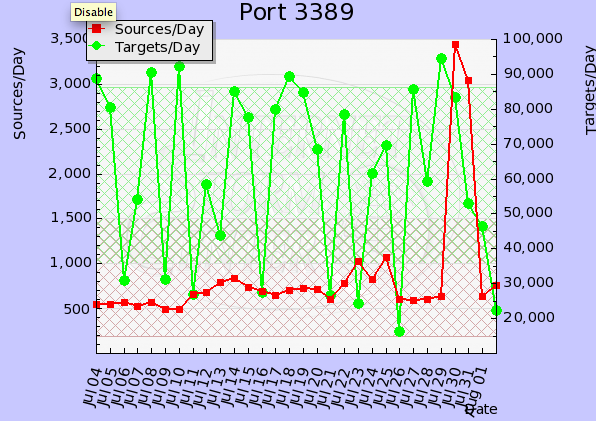
[1] https://isc.sans.edu/port.html?port=3389
------
Johannes B. Ullrich, Ph.D.
SANS Technology Institute
Twitter
My next class:
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |
×
![modal content]()
Diary Archives


Comments
2011-07-31 00:04:20 174.46.126.2
2011-07-26 08:07:39 217.41.13.152
We have a public domain-joined RDP server.... I know, it wasn't me - everyone knows it's crazy, and they have my comments in writing. I had & have nothing to do with it.
The usernames attempted in these two instances were as follows. One of the sessions was firewalled off mid-flow, so this won't be a complete list.
There are of course other random infrequent attempts, but they just "smell" different and are fairly basic and brief.
1
123
a
actuser
adm
admin
admin1
admin2
administrator
aspnet
backup
console
david
guest
john
office
owner
reception
root
server
sql
support
support_388945a0
sys
test
test1
test2
test3
user
user1
user2
user3
user4
user5
smuck
Aug 3rd 2011
1 decade ago
HackDefendr.com
Aug 4th 2011
1 decade ago
sforslev
Aug 4th 2011
1 decade ago
Yin
Aug 4th 2011
1 decade ago
altonius
Aug 10th 2011
1 decade ago