Malspam using password-protected Word docs to push Remcos RAT
Introduction
Malicious spam (malspam) using attached password-protected Word documents to evade detection is nothing new. I've documented it as early as March 2017, and this style of malware distribution started years before then. This particular campaign has pushed a variety of malware, including IcedID (Bokbot), various types of ransomware, and Nymaim. This diary from 2018 has a list of different types of malware seen from this campaign during that year.
At times, this resume-themed malspam can disappear for several weeks, but I always see it return. This most recent wave began as early as Wednesday 2019-08-28. When I checked on Tuesday 2019-09-03, this infection chain pushed Remcos RAT.
Today's diary reviews characteristics of this infection chain.
Malspam
Recent malspam looks similar to a diary I wrote in March 2019 and a blog I posted almost two months later in May. This time, the sending addresses were all probably spoofed, and they all end with @t-online.de. Attachment names all end with resume.doc. I've pasted the dates, times, sending addresses, subject lines, and attachment names here.
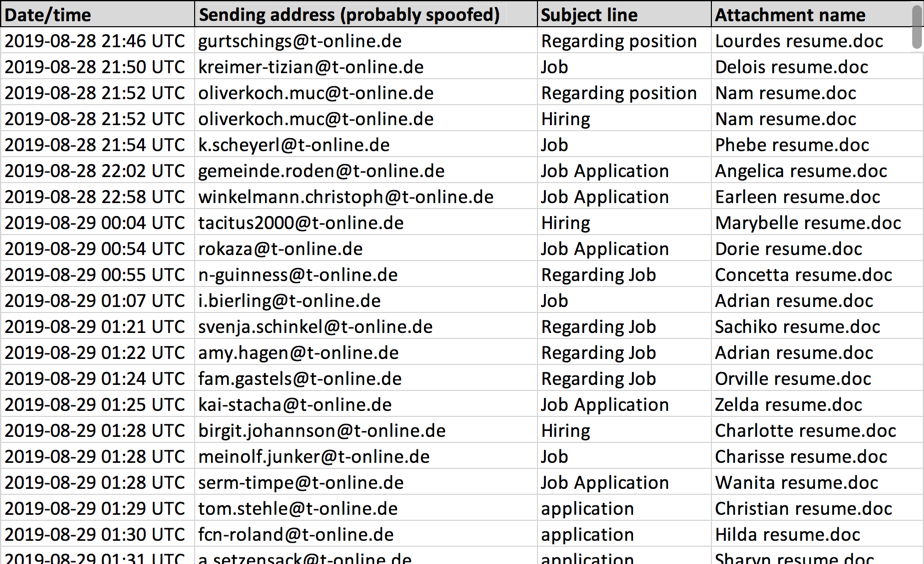
Shown above: Dates, times, senders, subject lines, and attachment names for recent malspam from this campaign.
I was not able to find an example of the malspam from this most recent wave of emails; however, the image below shows what these emails typically look like.
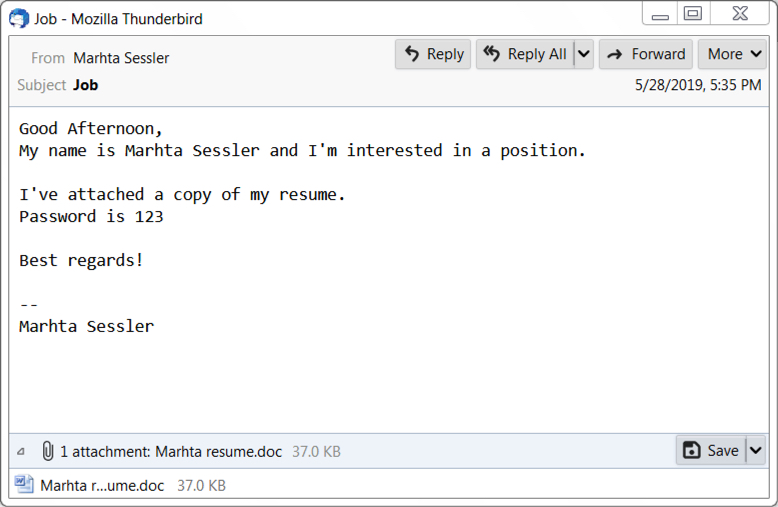
Shown above: What this malspam typically looks like.
Attached Word documents
The attached Word documents use 123 as the password. These Word documents have macros, and the visual template looks remarkably similar to previous examples I've reviewed.
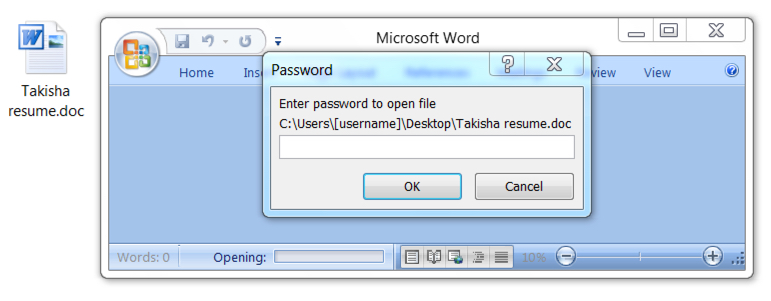
Shown above: Recent example of an attached Word document from this malspam campaign. The password is 123

Shown above: The Word document after it is unlocked by the password.
Infection traffic
Infection traffic was similar to what I've seen before from this campaign. First was an HTTP request that returned a Windows executable file. In this case, the initial URL ended in .jpg. This was followed by post-infection traffic over TCP ports 2404 and 2405. When I ran the same Word document through an Any.Run sandbox, it also generated two DNS queries not seen during my infection traffic.
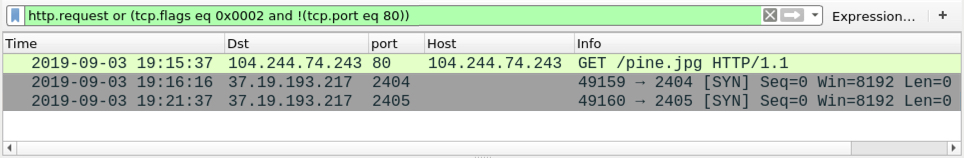
Shown above: Traffic from an infection in my lab, filtered in Wireshark.
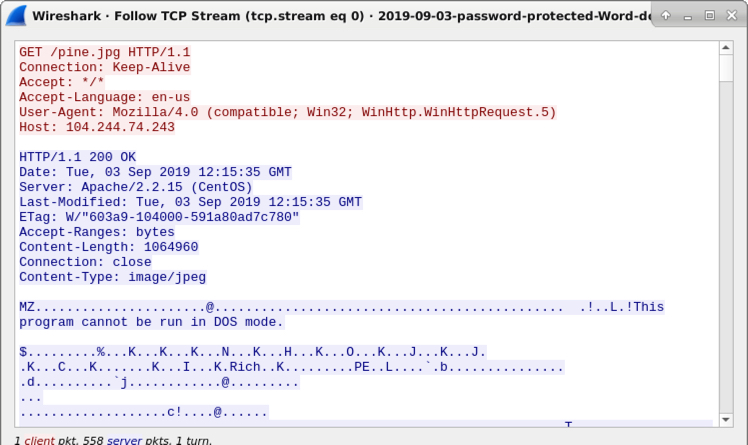
Shown above: The initial HTTP request returned a Windows executable file.
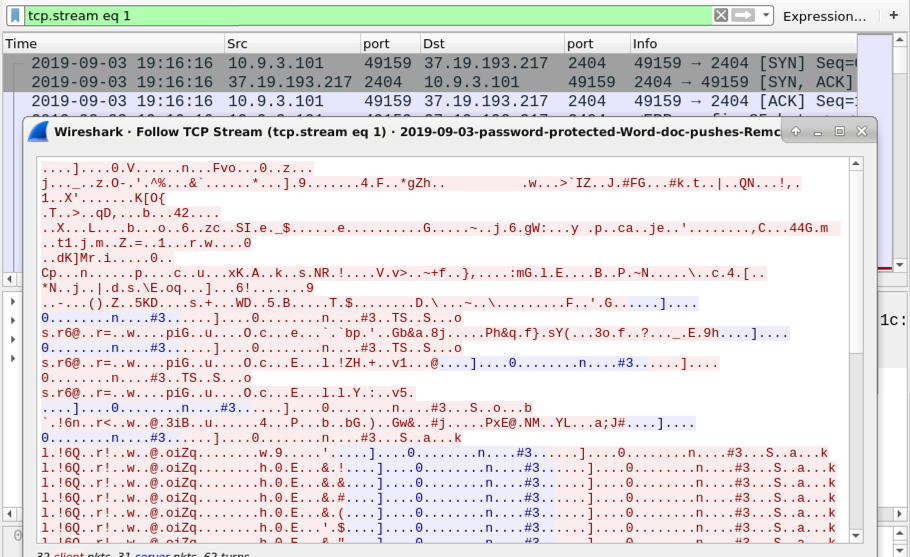
Shown above: Post-infection traffic generated by Remcos RAT (1 of 2).
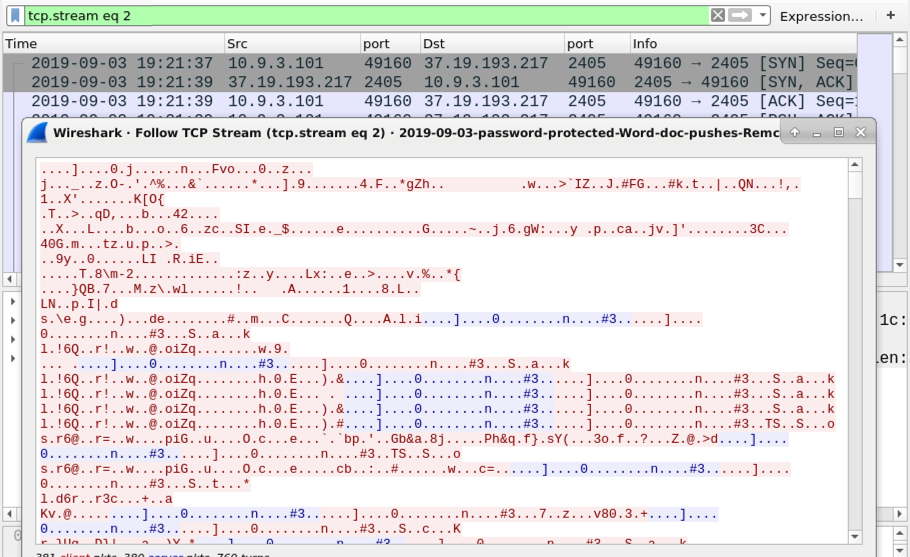
Shown above: Post-infection traffic generated by Remcos RAT (2 of 2).

Shown above: Traffic caused by running the Word document in the Any.Run sandbox (link).
Forensics on the infected Windows host
The initial Windows executable (EXE) file was saved to the user's AppData\Local\Temp directory. It generated an EXE that was slightly over 400 MB, which kept Remcos RAT persistent on the infected Windows host. This Remcos RAT sample also updated the Windows registry to stay persistent after a reboot.
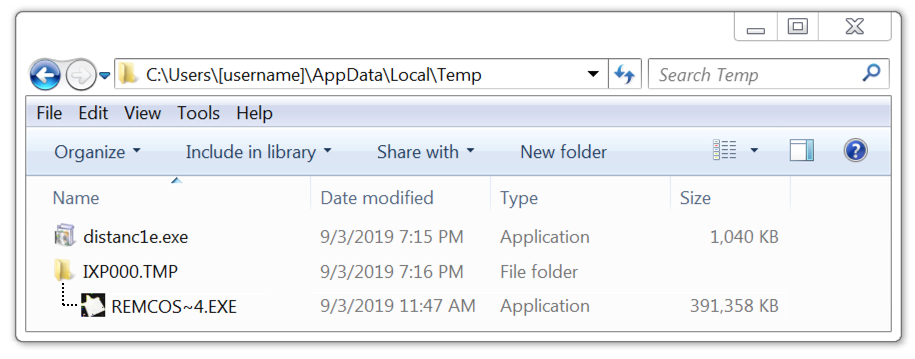
Shown above: Windows executable files associated with this Remcos RAT infection.
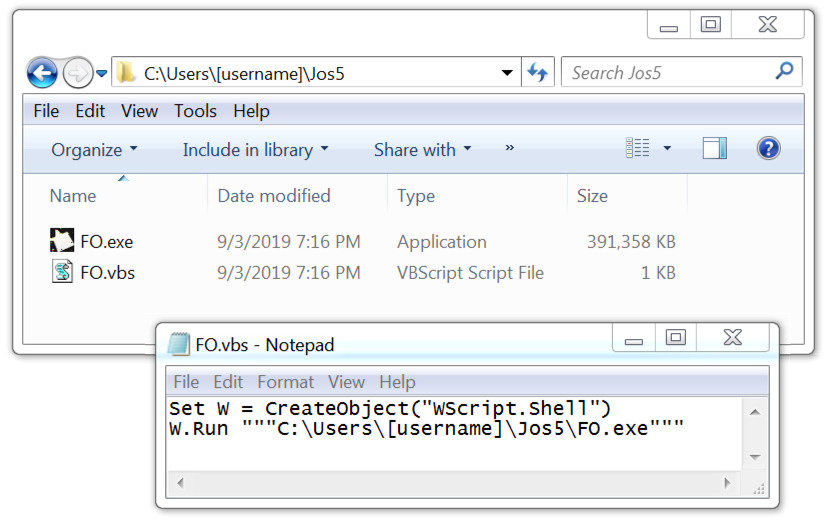
Shown above: Remcos RAT persistent on the infected Windows host.
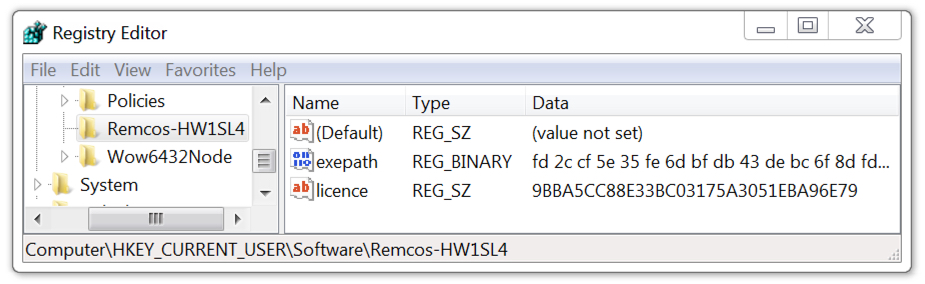
Shown above: Windows registry updates caused by this Remcos RAT sample.
Indicators of Compromise (IoCs)
Infection traffic:
- 104.244.74[.]243 port 80 - 104.244.74[.]243 - GET /pine.jpg
- 37.19.193[.]217 port 2404 - encoded TCP traffic caused by Remcos RAT
- 37.19.193[.]217 port 2405 - encoded TCP traffic caused by Remcos RAT
- 209.141.40[.]183 port 2404 - toptoptop3[.]online - attempted TCP connection (caused by Remcos RAT)
- 209.141.40[.]183 port 2404 - toptoptop3[.]site - attempted TCP connection (caused by Remcos RAT)
Associated files:
SHA256 hash: 932505acc15faede0993285532ed6d5afb27ce1c591a0819653ea5813d11cd55
- File size: 37,752 bytes
- File name: Takisha resume.doc
- File description: Password-protected Word doc -- Password: 123
SHA256 hash: fa9a94b32f7fa1e1e3eef63d3fb9003fda8d295e1f1a3e521691725e4c7da9f3
- File size: 1,064,960 bytes
- File location: hxxp://104.244.74[.]243/pine.jpg
- File location: C:\Users\[username]\AppData\Local\Temp\distanc1e.exe
- File description: initial installer EXE for Recmos RAT, retrieved by macro from the above Word doc
SHA256 hash: c866c269cd1617ee739216e24ba7cd1b392684b441bcdf10a6c0fdba073fbc28
- File size: 400,749,569 bytes
- File location: C:\Users\[username]\AppData\Local\Temp\IXP000.TMP\REMCOS~4.EXE (deleted itself)
- File location: C:\Users\[username]\Jos5\FO.exe
- File description: Remcos RAT
Final words
Remcos RAT is not the only malware distributed by this campaign. In previous months, other families of malware have been seen from this malspam, most recently IcedID (Bokbot). Detection rates on the attached Word documents are very low, since they are encrypted and use password protection. However, spam filters and proper system administrative practices like Software Restriction Policies (SRP) or AppLocker will easily prevent these types of infections on Windows-based systems.
Pcap and malware for this diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments