Loader activity for Formbook "QM18"
Introduction
In recent weeks, I've run across loaders related to GuLoader or ModiLoader/DBatLoader. I wrote about one in my previous diary last month. That loader for Remcos RAT was identified by @Gi7w0rm as GuLoader. Today I ran across another loader based on a tweet from @V3n0mStrike about recent Formbook activity.
Today's diary briefly reviews this activity based from an infection run on Tuesday 2023-07-11.
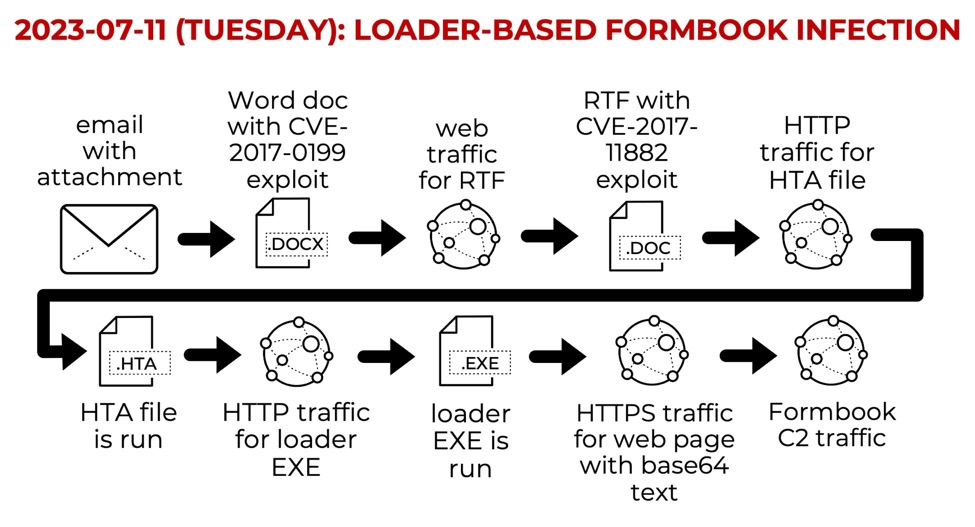
Shown above: Flow chart for this loader-based Formbook infection.
Email Distribution
After viewing the tweet from @V3n0mStrike, I searched through VirusTotal and found at least two emails with the associated .docx file attachment.
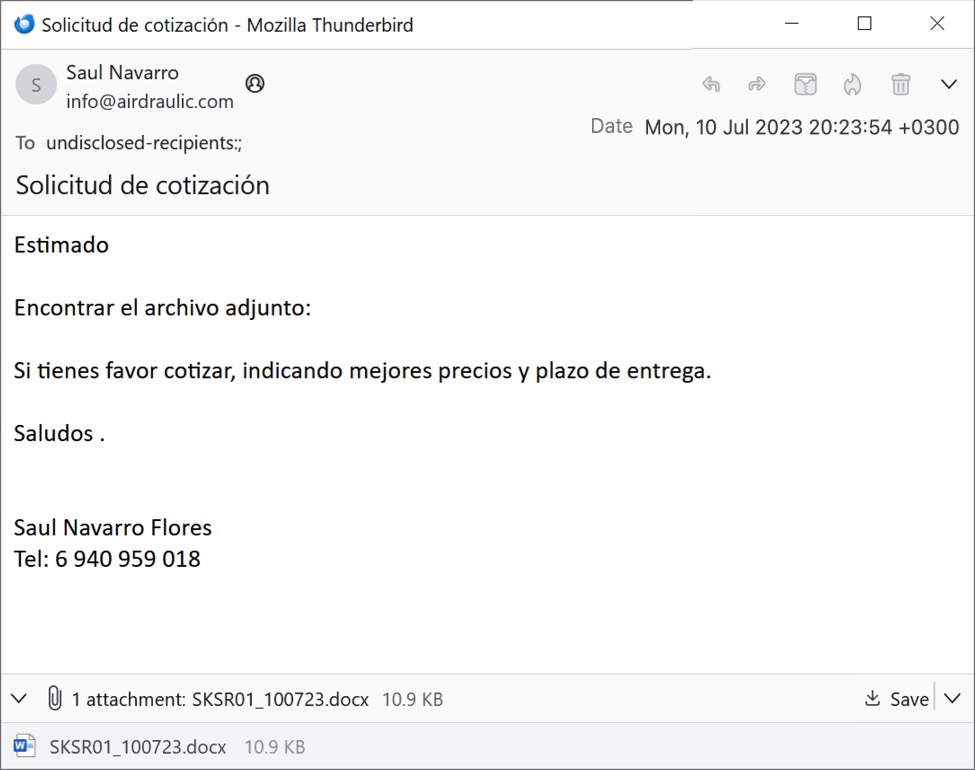
Shown above: First of two emails with the associated attachment.
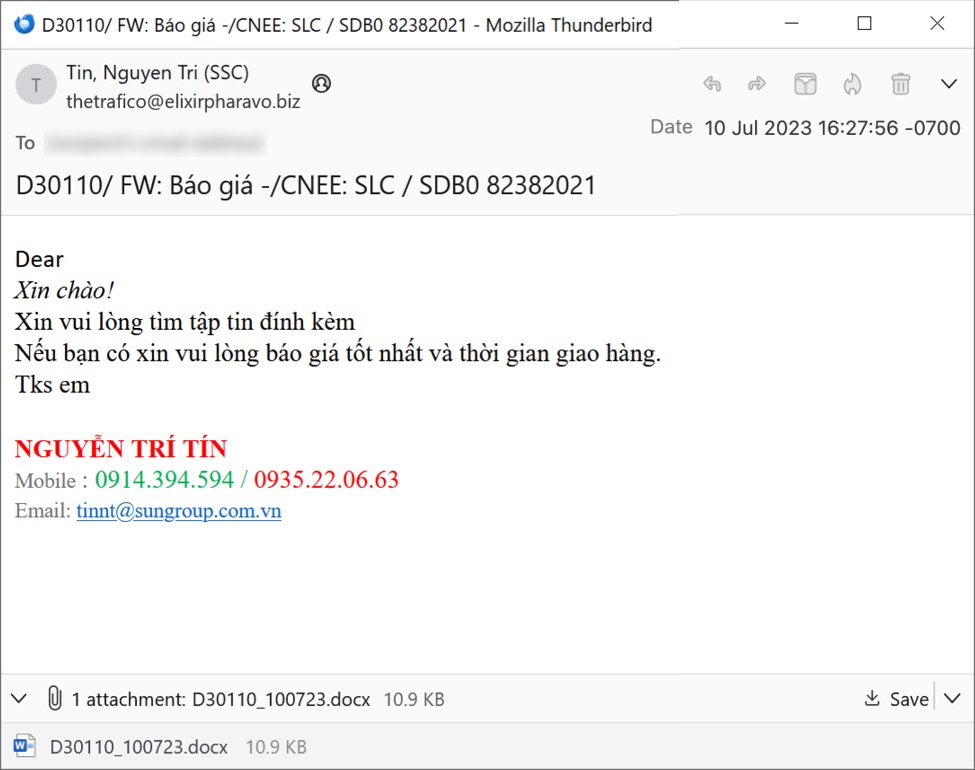
Shown above: Second of two emails with the associated attachment.
Indicators of Compromise
The following are indicators of compromise (IOCs) after using the .docx attachment to kick off an infection run.
SHA256 hash: 7f4fcb19ee3426d085eb36f0f27d8fd3d0242d0aa057daa9f4d8a7cd68576045
File size: 11,197 bytes
File name: SKSR01_100723.docx
File type: Microsoft Word 2007+
File description: Word document with exploit for CVE-2017-0199
SHA256 hash: d5f04bf7472599a893de61a21acb464ee11a9b7fbb2a20e348309857ee321691
File size: 27,527 bytes
URL for this file: hxxps://e[.]vg/LyLQRAip
Redirected to: hxxp://23.94.236[.]203/wq/wqzwqzwqzwqzwqzwqzwqzwqzwqz%23%23%23%23%23%23%23%23%23%23%23%23%23%23%23%23%23%23wqzwqzwqszwqa.doc
File type: ISO-8859 text, with very long lines (6432), with CR, LF line terminators (RTF)
File description: Retrieved by above .docx file, this is an RTF to exploit CVE-2017-011882
SHA256 hash: e09040ce96631cf7c1f7be6de48f961540e6fb8db97859c9fa7ae35f7fa9d930
File size: 3,850 bytes
File location: hxxp://23.94.236[.]203/wq/IE_NET.hta
Saved file location: C:\Users\[username]\AppData\Local\Temp\IE_NETS.hta
File type: HTML document text, ASCII text, with very long lines (3682), with CRLF line terminators
File description: Retrieved by above RTF, this is an HTA to retrieve and run an EXE
SHA256 hash: 576ef869c72f3afe6f4f5101f27aeb0d479cae8e5d348eea4e43e8af8252dfd0
File size: 218,112 bytes
File location: hxxp://23.94.236[.]203/235/win.exe
Saved file location: C:\Users\[username]\AppData\Local\Temp\IBM_Centos.exe
File type: PE32+ executable (GUI) x86-64 Mono/.Net assembly, for MS Windows
File description: Loader EXE retrieved and run by the above HTA
SHA256 hash: 90615cb1ec6ca6c93dfe44f414c0d00db4e200c5011304df2c652182b4b593e3
File size: 716,404 bytes
File location: hxxps://kyliansuperm92139124[.]shop/customer/959
File type: HTML document text, ASCII text, with very long lines (64470), with CRLF line terminators
File description: example of an HTML file retrieved by the above loader EXE
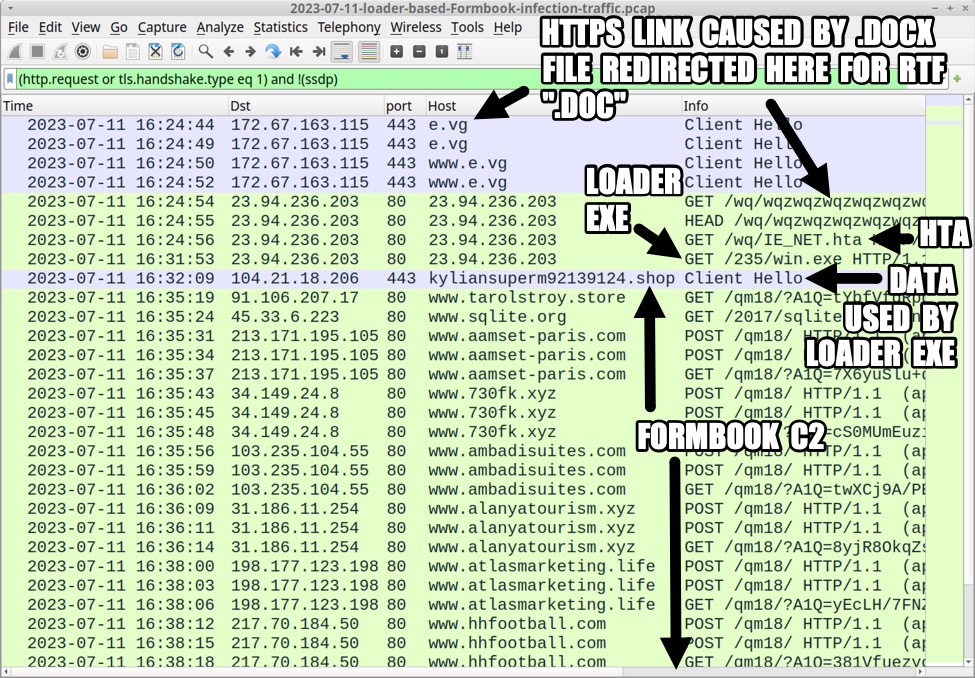
Shown above: Traffic from the infection filtered in Wireshark.
Domains used for Formbook HTTP GET requests only:
www.6882b[.]com
www.bluhenhalfte[.]xyz
www.iweb-sa[.]com
www.kalndarapp14[.]com
www.latabledelepicier[.]com
www.poultry-symposium[.]com
www.printmyride[.]store
www.smartinnoventions[.]com
www.tarolstroy[.]store
www.terrenoscampestres[.]com
www.test-kobewaterworks[.]com
www.uximini[.]com
www.vidintros[.]shop
www.woman-86[.]com
www.wyyxscc5856[.]com
www.yahialocation[.]com
Domains used for Formbook HTTP GET and POST requests:
www.730fk[.]xyz
www.aamset-paris[.]com
www.alanyatourism[.]xyz
www.ambadisuites[.]com
www.atlasmarketing[.]life
www.autolifebelt[.]com
www.collingswoodfd[.]com
www.fn29in[.]xyz
www.hhfootball[.]com
www.kdu21[.]com
www.lazarus[.]team
www.london168wallet[.]monster
www.personifycoach[.]com
www.r1381[.]xyz
www.theartboxslidell[.]com
www.windmarkdijital[.]xyz
www.zsys[.]tech
Notes: I ran the infection on a Windows 7 host with Office 2007. The HTA file generated a wget request for the loader EXE, but that did not work, so I retrieved the loader using PowerShell's Invoke-WebRequest function. I saw no artifacts for persistence, and the infection stopped after I logged out. I also found no files temporarily saved to disk for data exfiltration like I've seen in previous Formbook infections.
Final Words
The two emails, associated malware, and a packet capture (pcap) of the infection traffic are available here.
For more examples of recent Formbook activity, see my 30 days of Formbook posts completed earlier this month.
--
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments