Hancitor/Pony malspam
Introduction
It's been one month since my last diary on malcious spam (malspam) with links to malicious Word documents containing Hancitor [1]. Back then, we saw Hancitor use Pony to download Vawtrak malware. Since then, I've seen indicators for this type of malspam on a near-daily basis.
Recently, these emails have stopped leading to Vawtrak. Instead, I'm now seeing malware that triggers alerts for Terdot.A [2, 3, 4, 5, 6, 7]. Tools from my employer identify this malware as DELoader, and a Google search indicates Terdot.A and DELoader are the same thing.
For now, I'm keeping my flow chart open on the final malware. With that in mind, let's take a look at some infection traffic generated on Thursday 2017-02-09 based on one of these emails.
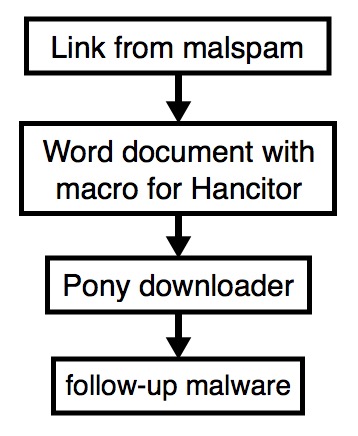
Shown above: Flow chart for the infection process.
The email
These emails generally have different subject lines each day, and they have spoofed sending addresses. The example I saw on 2017-02-09 was a fake message about a money transfer. It's similar to a wave of malspam seen the day before.
- Date: Thursday, 2017-02-09 16:05 UTC
- Received: from polsinelli.com [spoofed host name]
- Message-ID: <879081B3.F4FA76CC@polsinelli.com>
- From: "Polsinelli LLP" <mlemon@polsinelli.com> [spoofed sender]
- Subject: RE:RE: wife tf
The link from the email contains a base64-encoded string representing the recipient's email address. Based on that string, the downloaded file will have the recipient's name from the email address. I used a base64 string for a made-up email address and received a file named bofa_statement_marci.jones.doc.
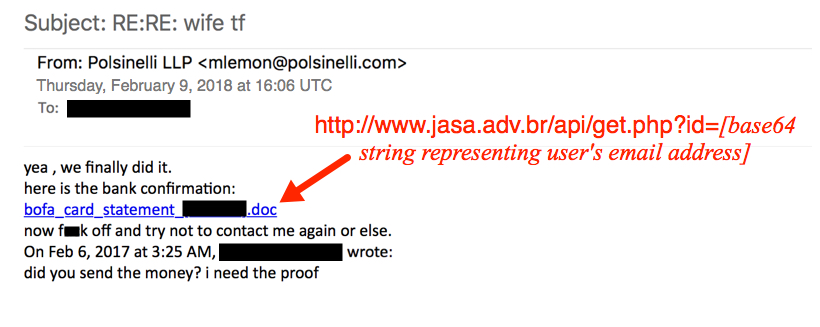
Shown above: Fake money transfer email with link to a Word document.
The link from the malspam downloaded a Microsoft Word document. The document contains a malicious VB macro described as Hancitor, Chanitor or Tordal. I generally call it Hancitor. If you enable macros, the document retrieves a Pony downloader DLL. At first, I thought Pony was retrieving the DELoader malware; however, another researcher told me it's Hancitor that grabs DELoader. I haven't had time to investigate; however, I probably need to update my flowchart.

Shown above: Retrieving the Hancitor Word document from the email link.
Shown above: Enabling macros will activate Hancitor.
The traffic
Pattern-wise, URLs from this infection are similar to previous cases of Hancitor/Pony malspam reported I've seen during the past week or two.
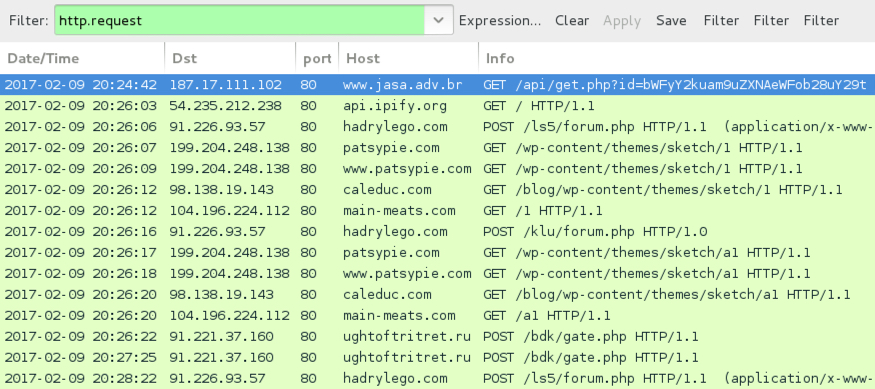
Shown above: Infection traffic after activating macros in the Word document.
Alerts show post-infection traffic for Terdot.A/Zloader, which is consistent with recent infections I've seen for malware identified as DELoader.

Shown above: Alerts on the traffic using Security Onion with Suricata and the ETPRO ruleset.
Indicators of Compromise (IOCs)
Email link noted on Thursday 2017-02-09 to download the Hancitor Word document:
- 187.17.111.102 port 80 - www.jasa.adv.br - GET /api/get.php?id=[base64 string]
Traffic after enabling macros on the Word document:
- api.ipify.org - GET / [IP address check]
- 91.226.93.57 port 80 - hadrylego.com - POST /ls5/forum.php [Hancitor callback]
- 91.226.93.57 port 80 - hadrylego.com - POST /klu/forum.php [Hancitor callback]
- 98.138.19.143 port 80 - caleduc.com - GET /blog/wp-content/themes/sketch/1 [call for Pony DLL]
- 104.196.224.112 port 80 - main-meats.com - GET /1 [call for Pony DLL]
- 199.204.248.138 port 80 - patsypie.com - GET /wp-content/themes/sketch/1 [call for Pony DLL]
- 98.138.19.143 port 80 - caleduc.com - GET /blog/wp-content/themes/sketch/a1 [call for DELoader]
- 104.196.224.112 port 80 - main-meats.com - GET /a1 [call for DELoader]
- 199.204.248.138 port 80 - patsypie.com - GET /wp-content/themes/sketch/a1 [call for DELoader]
- 91.221.37.160 port 80 - ughtoftritret.ru - POST /bdk/gate.php [DELoader callback]
Associated file hashes:
- SHA256 hash: 82d4b6676bbff17626aba1a65a9c6ec10ab036c101c8dc5e6e697693ec5a013f
- File size: 181,248 bytes
- Description: Word document from link to www.jasa.adv.br
- SHA256 hash: d2c79954335b579309957c22b1b7976359fd067691626f8beb99779143edaa69
- File size: 257,024 bytes
- Description: Terdot.A/DELoader
Final words
As this campaign progresses, IOCs will continue to change, and I'm sure traffic patterns will continue to evolve.
Pcap and malware for this diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net
References:
[1] https://isc.sans.edu/forums/diary/HancitorPonyVawtrak+malspam/21919
[2] http://malware-traffic-analysis.net/2017/01/25/index2.html
[3] http://malware-traffic-analysis.net/2017/01/30/index2.html
[4] http://malware-traffic-analysis.net/2017/01/31/index3.html
[5] http://malware-traffic-analysis.net/2017/02/01/index.html
[6] http://malware-traffic-analysis.net/2017/02/06/index2.html
[7] http://malware-traffic-analysis.net/2017/02/07/index.html


Comments