Hancitor malspam and infection traffic from Tuesday 2019-02-05
Introduction
Since 2018-12-17, malicious spam (malspam) pushing Hancitor malware (also known as Chanitor or Tordal) had been using Excel spreadsheets as decoy documents. Up through last week, a Hancitor executable file was embedded in these Excel spreadsheets. After opening the spreadsheet in Excel and enabling macros, the embedded Hancitor executable was dropped to a vulnerable Windows host. We saw this as recently as Monday 2019-01-28.
But this week on Tuesday 2019-02-05, the Hancitor campaign changed its decoy document. This campaign went back to using Word documents instead of Excel spreadsheets. After enabling macros, the Hancitor executable was retrieved from a web server hosted on the same IP address (but a different domain) as the initial Word document.
This diary provides a quick review of Hancitor malspam from Tuesday 2019-02-05.
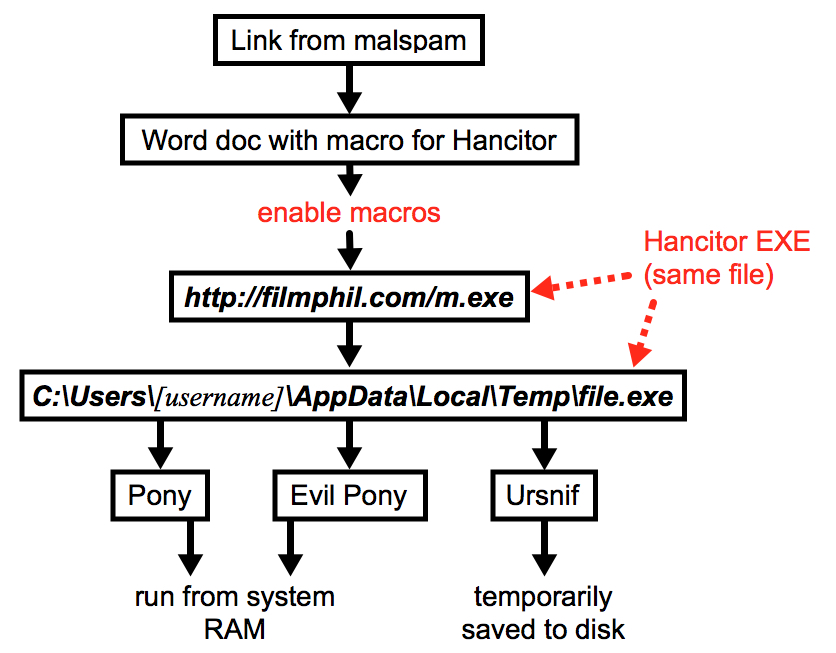
Shown above: Flow chart for the Hancitor infection on 2019-02-05.
The emails
This recent wave of Hancitor malspam used a HelloFax theme, and these emails had a link to download a malicious Word document. The Word document had a macro designed to infect a vulnerable Windows host with Hancitor. The macro did not run properly when I used Word 2007, but it appeared to work in Word 2010 and later versions. I'm not sure if this with Word 2007 issue was specific to my lab host.
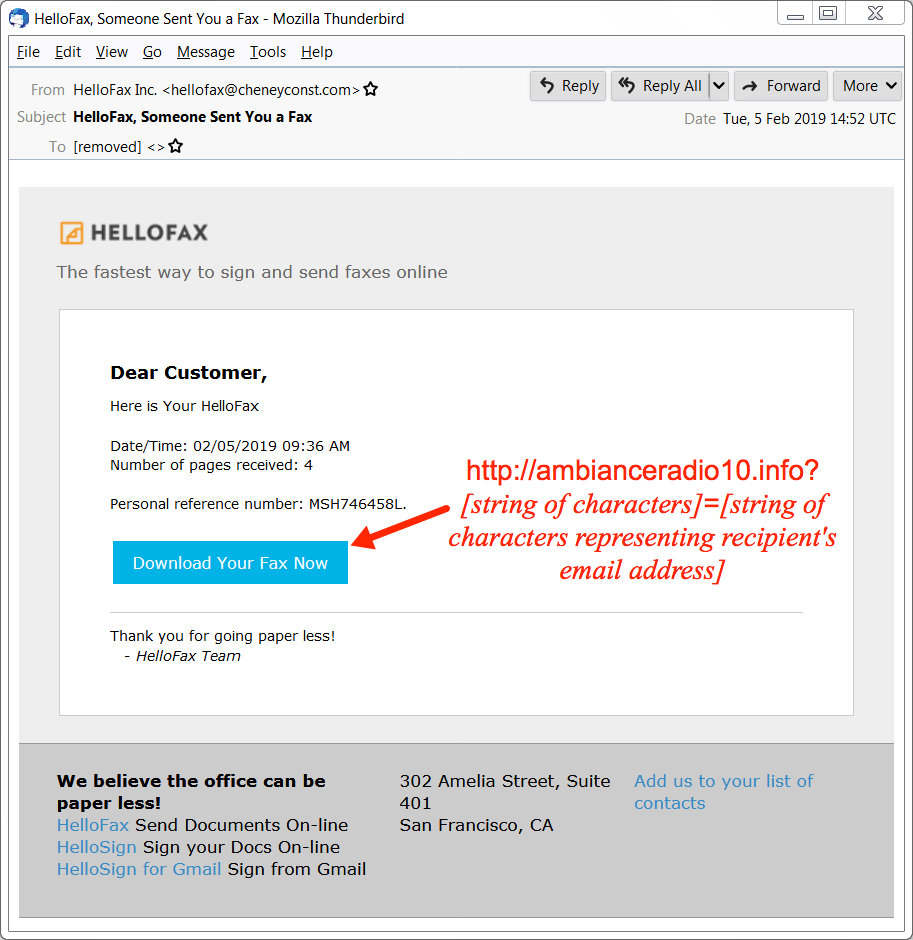
Shown above: Screenshot of an email from this wave of malspam.
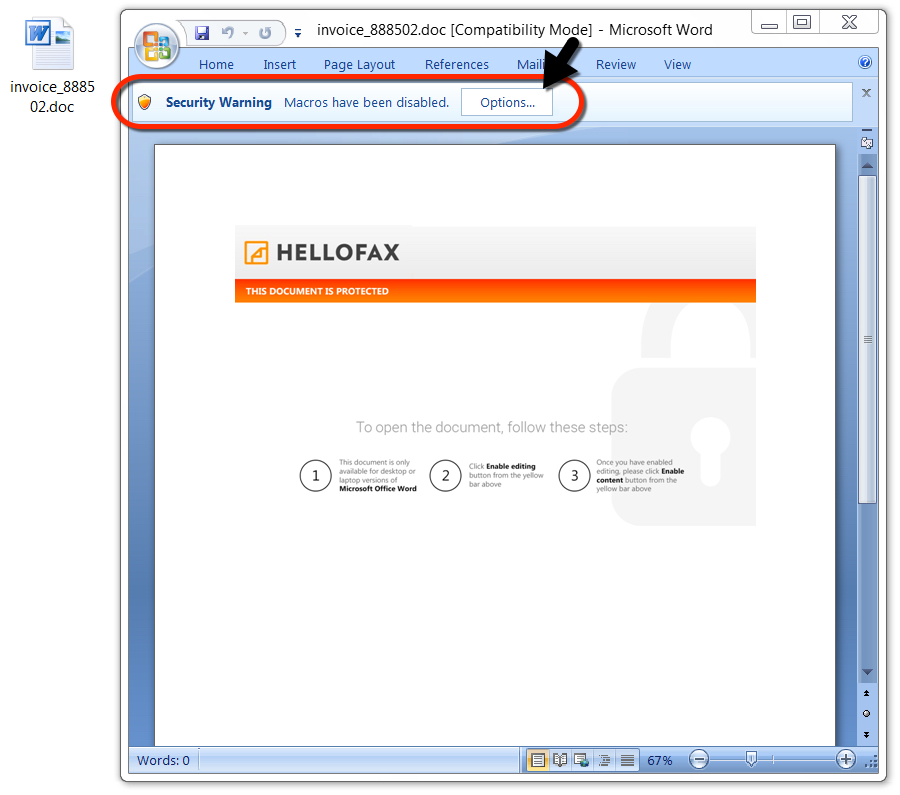
Shown above: The downloaded Word document.
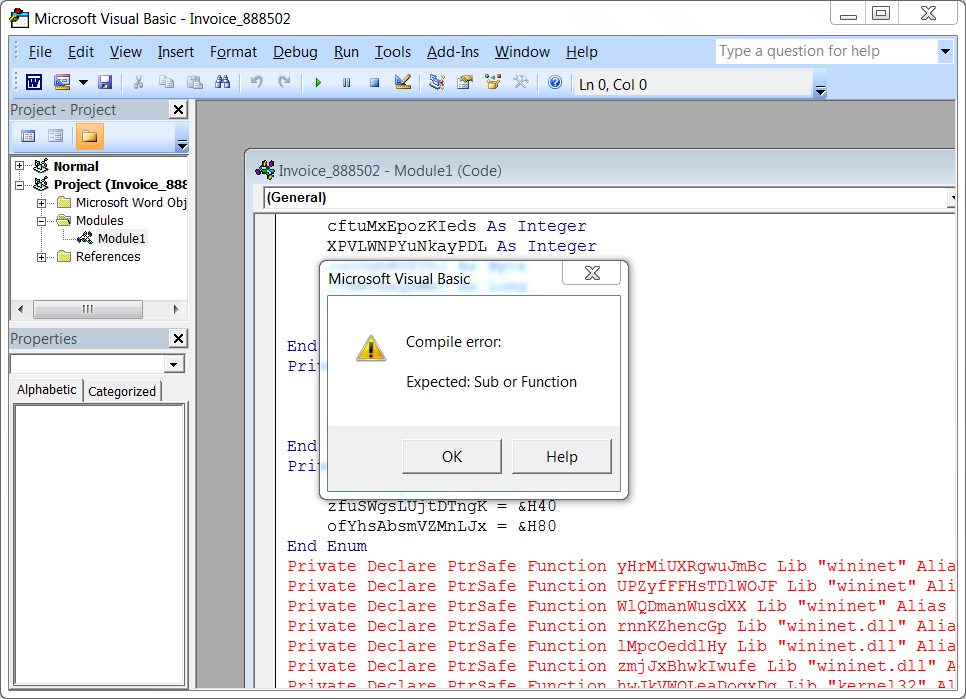
Shown above: Error when I enabled macros after opening the Word document in Word 2007.
The infection traffic
After @mesa_matt reported Tuesday's Hancitor domains on Twitter (link), @JayTHL reported these domains to the hosting provider, GoDaddy. By the time I tried generating some infection traffic, these domains had been taken off-line. To replicate the infection chain, I used a local server at 127.0.0.1 to host the Word document and Hancitor executable. Aside from the HTTP GET request to filmphil[.]com for m.exe, traffic patterns were remarkably consistent with previous Hancitor infections in recent weeks.
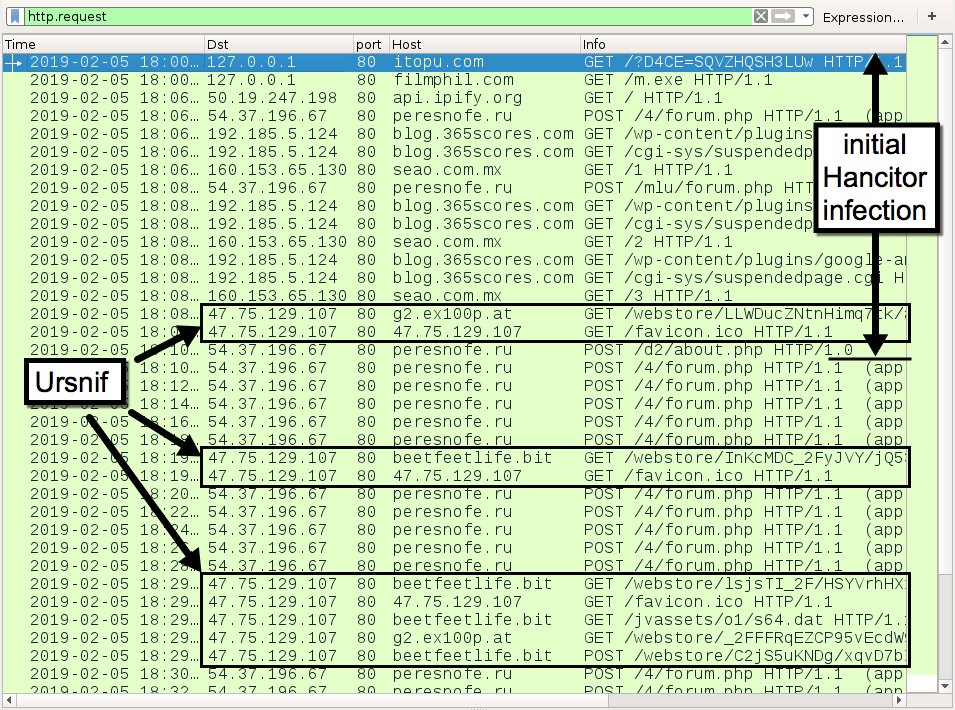
Shown above: Traffic from the infection filtered in Wireshark.
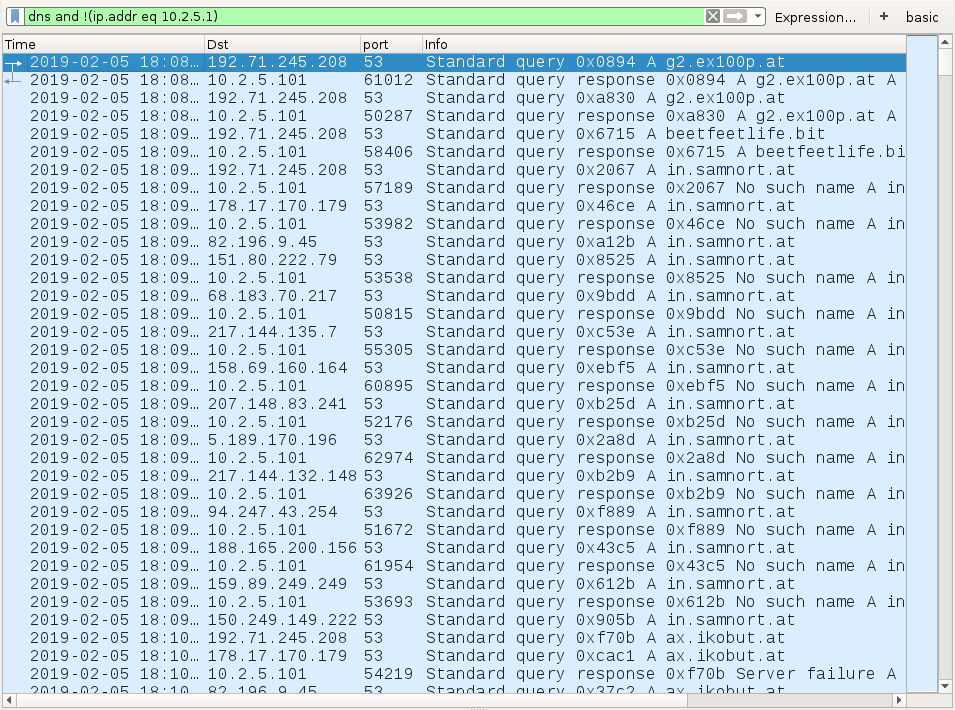
Shown above: DNS traffic to public IP addresses caused by Ursnif (Gozi IFSB).
Indicators of Compromise (IoCs)
Malspam information:
- Date: Tuesday 2019-02-05
- Sender (spoofed): hellofax@cheneyconst.com
- Theme: HelloFax
Malware information:
- From @mesa_matt: list of domains hosting Hancitor Word docs (link)
- From @James_inthe_box: URLs and file hashes for associated malware and c2 traffic (link)
- Twitter thread discussing Hancitor on 2019-02-05 (link)
Final words
A pcap of infection traffic for today's diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments