Enhancing pentesting recon with nmap
by Manuel Humberto Santander Pelaez (Version: 1)
You might have used nmap several times for recon using the conventional portscan functionality (Connect scan, SYN Scan, FIN scan, UDP scan, ...) but for gathering extra info like HTTP directories, DNS host enumeration without performing zone transfer, Microsoft SQL Server enumeration and SMB device info people usually uses additional tools. I will show you how nmap can provide that information without use of extra tools:
1. HTTP Directories
The http-enum script is able to test for the existence of some directories that are common to many webservers and could have potentially interesting information and vulnerabilities. This is an alternative to tools like nikto:
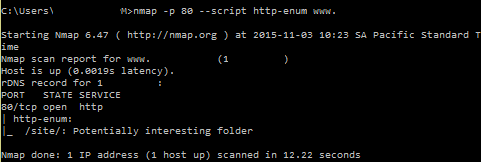
2. DNS Host Enumeration
Most DNS are correctly configured so they will not allow a zone transfer by default. Instead, the other available way is to query for specific known names common to exposed services like the common names used by Microsoft services. We can use the dnsbrute nmap script, which is a basic alternative to dnsrecon and not supporting all its functionalities:
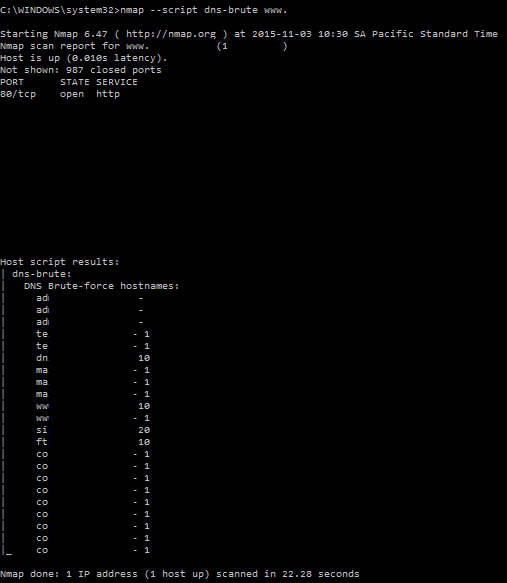
3. SMB device info
Windows devices got lots of information that can be gathered from nmap directly:
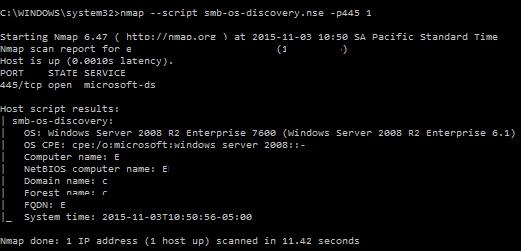
4. Microsoft SQL Server instances info
You can grab useful information of mysql instances in a server. This is an alternative to SQLRecon or SQLPing:
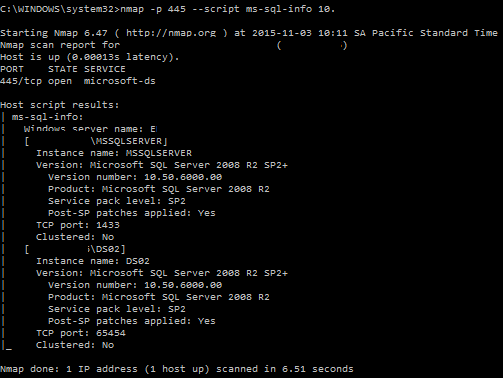
What I like about nmap recon scripts is they are fast, reliable and they minimize the load of tools you need to carry on. They will save you tons of time gathering valuable info so you can focus in compromising the assets. If you want to know more about the nmap scripts, please check https://nmap.org/nsedoc.
Manuel Humberto Santander Peláez
SANS Internet Storm Center - Handler
Twitter: @manuelsantander
Web:http://manuel.santander.name
e-mail: msantand at isc dot sans dot org


Comments