Emotet infection with IcedID banking Trojan
Introduction
Emotet malware is distributed through malicious spam (malspam), and its active nearly every day--at least every weekday. Sometimes the criminals behind Emotet take a break, such as a one month-long hiatus from early October through early November, but the infrastructure pushing Emotet has been very active since Monday 2018-11-05.
As Symantec and others have reported, the group behind Emotet has evolved from maintaining its own banking Trojan, and it now also distributes malware for other groups. I commonly see follow-up malware like Trickbot and Zeus Panda Banker during Emotet infections generated in my lab environment.

Shown above: Chain of events for recent infections caused by Emotet malspam.
Today's diary examines an Emotet infection on Wednesday 2018-11-14 with the IcedID banking Tojan as its follow-up malware.
Details
A quick check of URLhaus showed me several URLs tagged emotet and heodo, which is another name for Emotet. After you've seen enough of these URLs, you get a feel for their patterns and can identify an Emotet URL by looking at it.
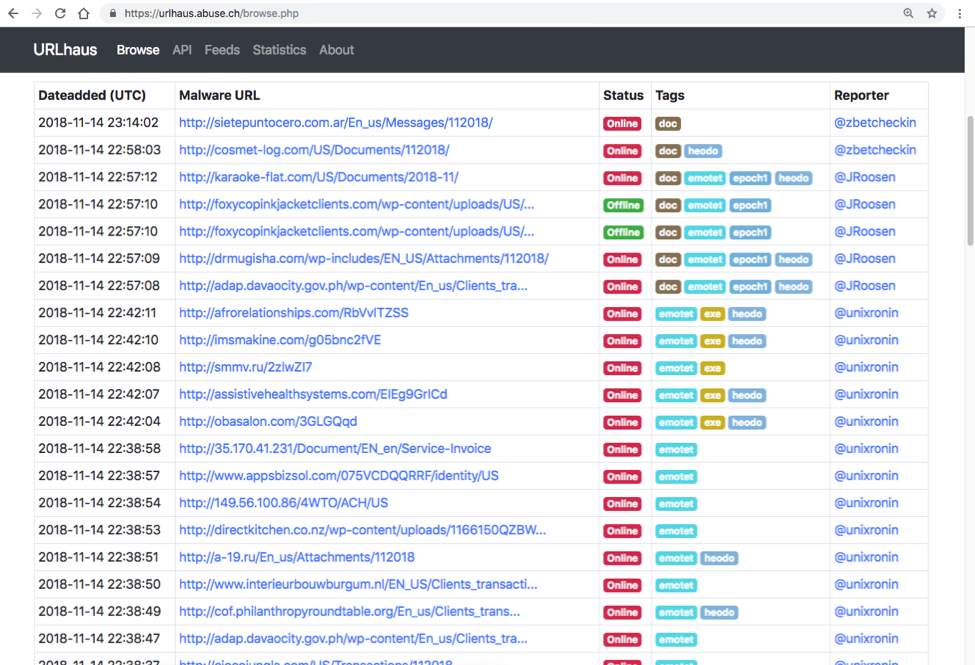
Shown above: Several Emotet URLs I saw on URLhaus.
Using a vulnerable Windows host, I picked an Emotet URL to download a Word document. I opened the document, enabled macros, and saw the expected infection traffic.
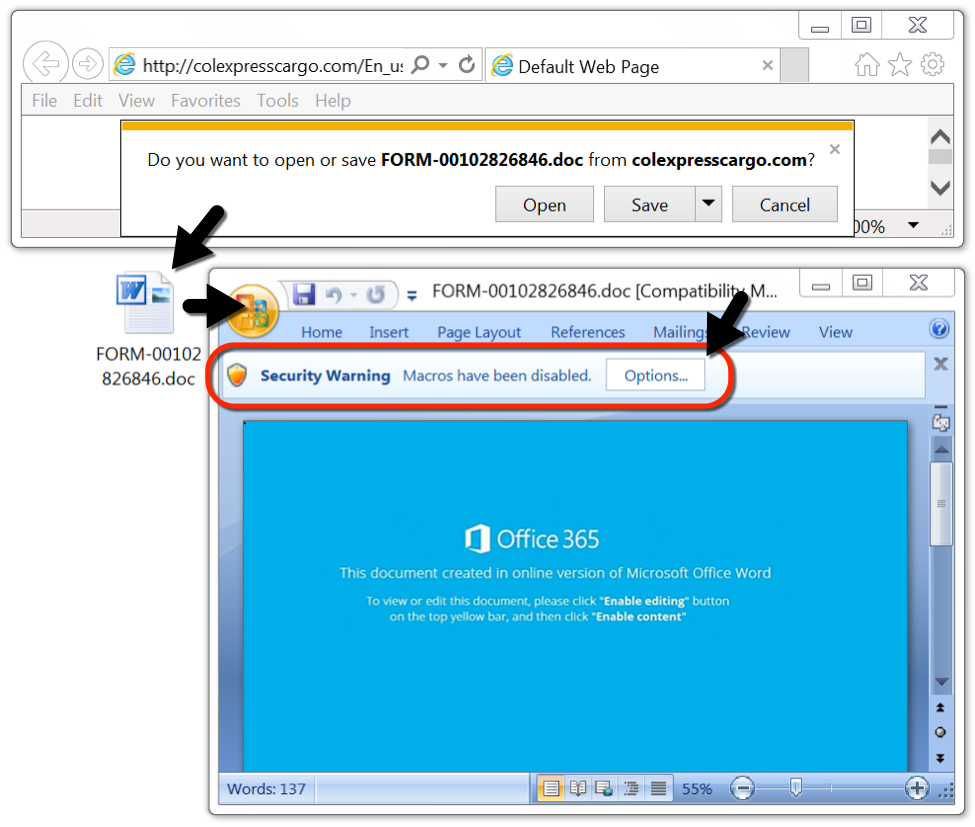
Shown above: Example of a Word document downloaded from an Emotet URL.

Shown above: Traffic from an infected Windows host filtered in Wireshark.
Forensics on the infected Windows host
After reviewing the infection traffic, I checked my infected Windows host for malware. Malware binaries for both Emotet and the IcedID banking Trojan were in the same places I've seen them before.
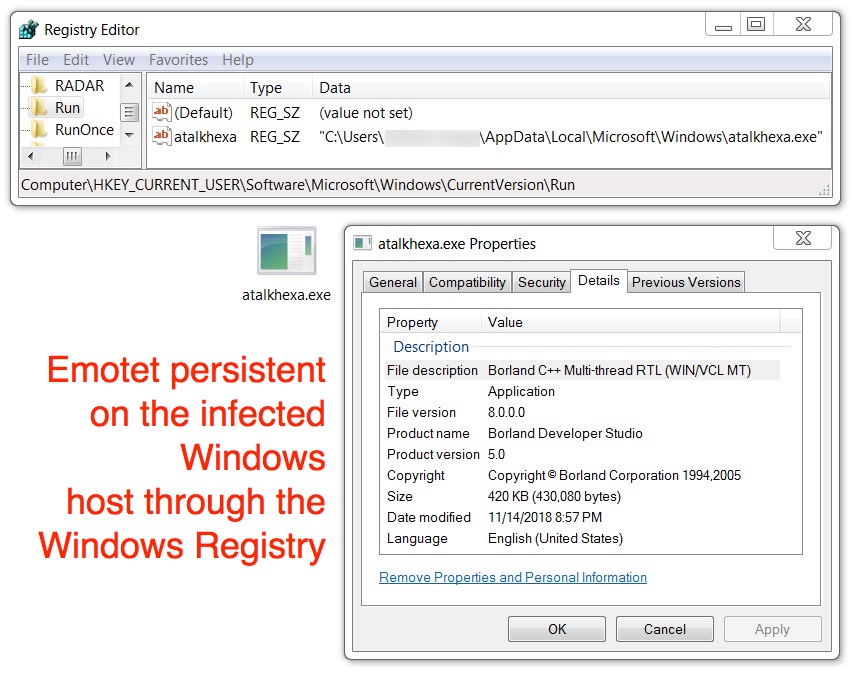
Shown above: Emotet persistent on my infected Windows host.
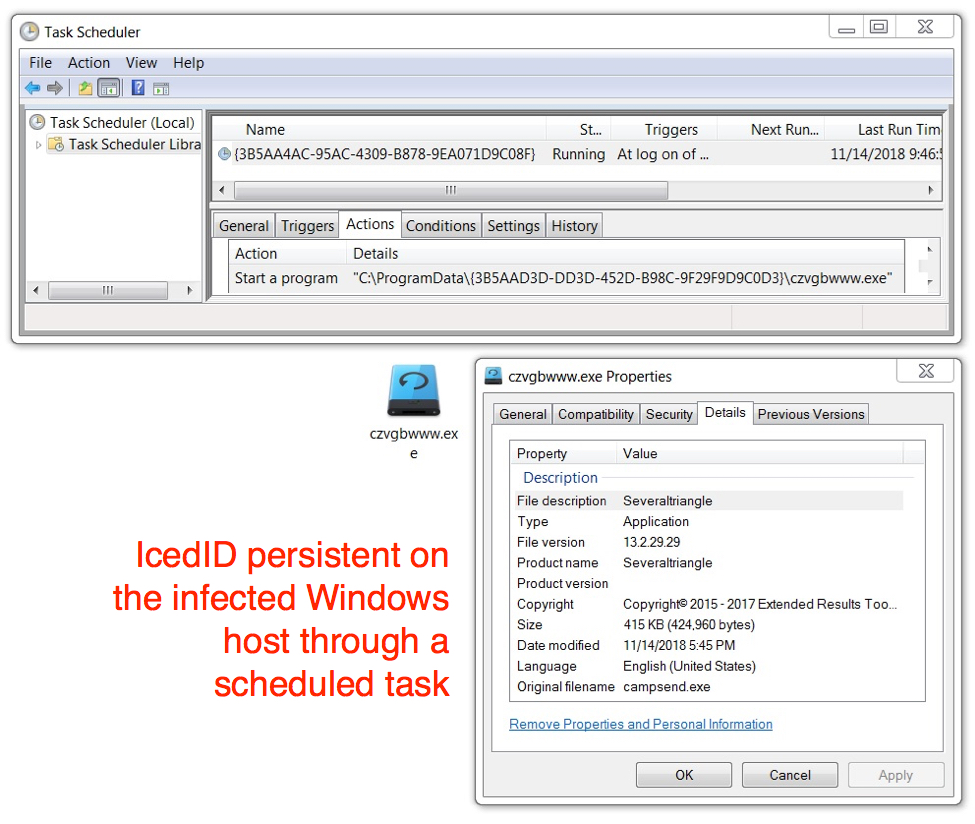
Shown above: IcedID persistent on my infected Windows host.
Indicators of Compromise (IoCs)
Malware from my infected Windows host:
SHA256 hash: 045e15c1df7c712dcac94c720b81df08fd0ff4e4c177d231d5cdcd7b4d096f95
- File size: 94,592 bytes
- File name: form-363439590633444.doc (random file names depending on the download URL)
- File description: Downloaded Word doc with macro for Emotet
SHA256 hash: d6dd56e7fb1cc71fc37199b60461e657726c3bf8319ce59177ab4be6ed3b9fb4
- File size: 430,080 bytes
- File location: C:\Users\[username]\AppData\Local\Microsoft\Windows\[random name].exe
- File description: Emotet malware binary on the infected Windows host
SHA256 hash: 667cda76b582c0771f85ad12167238e0f4bb12f479030d99c8a15d7f08eb9975
- File size: 421,888 bytes
- File location: C:\Users\[username]\AppData\Local\Microsoft\Windows\[random name].exe
- File description: updated Emotet malware binary on the infected Windows host
SHA256 hash: cb04718694115b94b4d8bde2be0a4daf802c7a4c94f9b81811872e4e7126e813
- File size: 424,960 bytes
- File location: C:\ProgramData\OFyKiE6aak4yfFf.exe
- File description: IcedID banking Trojan retrieved by Emotet
SHA256 hash: 63e348c05cd94f4488f7f1707ba901ddfa8ec04b4626a46ae2d9d0a83ae291ae
- File size: 424,960 bytes
- File location: C:\ProgramData\{3B5AAD3D-DD3D-452D-B98C-9F29F9D9C0D3}\czvgbwww.exe
- File description: IcedID banking Trojan persistent on the infected Windows host
Traffic from my infected Windows host:
Traffic that returned the initial Word document:
- 78.135.65.15 port 80 - bysound.com.tr - GET /En_us/Documents/11_18/
Traffic that returned the Emotet malware binary:
- 50.62.194.30 port 80 - c-t.com.au - GET /PspAMbuSd2
- 50.62.194.30 port 80 - c-t.com.au - GET /PspAMbuSd2/
Post-infection traffic caused by Emotet:
- 5.9.128.163 port 8080 - Attempted TCP connections, no response from the server
- 12.222.134.10 port 7080 - Attempted TCP connections, no response from the server
- 23.254.203.51 port 8080 - Attempted TCP connections, no response from the server
- 24.201.79.34 port 8080 - 24.201.79.34:8080 - GET /
- 37.120.175.15 port 80 - Attempted TCP connections, no response from the server
- 49.212.135.76 port 443 - 49.212.135.76:443 - GET /
- 50.78.167.65 port 7080 - 50.78.167.65:7080 - GET /
- 69.198.17.20 port 8080 - Attempted TCP connections, no response from the server
- 71.163.171.106 port 80 - 71.163.171.106 - GET /
- 71.58.165.119 port 443 - 71.58.165.119:443 - GET /
- 71.58.165.119 port 443 - 71.58.165.119:443 - GET /whoami.php
- 76.65.158.121 port 50000 - 76.65.158.121:50000 - GET /
- 81.86.197.52 port 8443 - 81.86.197.52:8443 - GET /
- 86.12.247.149 port 80 - Attempted TCP connections, no response from the server
- 109.170.209.165 port 8080 - 109.170.209.165:8080 - GET /
- 133.242.208.183 port 8080 - 133.242.208.183:8080 - GET /
- 138.207.150.46 port 443 - 138.207.150.46:443 - GET /
- 139.59.242.76 port 8080 - Attempted TCP connections, no response from the server
- 159.65.76.245 port 443 - Attempted TCP connections, no response from the server
- 160.36.66.221 port 990 - 160.36.66.221:990 - GET /
- 165.227.213.173 port 8080 - Attempted TCP connections, no response from the server
- 173.11.47.169 port 8080 - 173.11.47.169:8080 - GET /
- 173.19.73.104 port 443 - Attempted TCP connections, no response from the server
- 173.160.205.161 port 990 - 173.160.205.161:990 - GET /
- 173.160.205.162 port 443 - 173.160.205.162:443 - GET /
- 177.242.156.119 port 80 - Attempted TCP connections, no response from the server
- 186.18.236.83 port 8080 - 186.18.236.83:8080 - GET /
- 189.134.18.141 port 443 - Attempted TCP connections, no response from the server
- 189.244.86.184 port 990 - 189.244.86.184:990 - GET /
- 192.155.90.90 port 7080 - Attempted TCP connections, no response from the server
- 198.199.185.25 port 443 - Attempted TCP connections, no response from the server
- 200.127.55.5 port 80 - 200.127.55.5 - GET /
- 205.185.187.190 port 80 - 205.185.187.190 - GET /
- 210.2.86.72 port 8080 - 210.2.86.72:8080 - GET /
- 210.2.86.94 port 8080 - Attempted TCP connections, no response from the server
Post-infection traffic caused by the IcedID banking Trojan:
- 185.129.49.19 port 443 - therebes.biz - SSL/TLS traffic caused by IcedID
- 185.129.49.19 port 80 - freshwallet.at - GET /data2.php?0123456789ABCDEF (different hex characters depending on the infected host)
Final words
Both Emotet and IcedID have remained fairly consistent in their behavioral patterns, so nothing here is unusual. This diary is yet another reminder the criminals behind Emotet remain active, and they continue to push follow-up malware like the IcedID banking Trojan.
A pcap of the infection traffic and the associated malware from today's diary can be found here.
---
Brad Duncan
brad [at] malware-traffic-analysis.net


Comments