.COM.COM Used For Malicious Typo Squatting
Today, our reader Jeff noted how domains ending in ".com.com" are being redirected to what looks like malicious content. Back in 2013, A blog by Whitehat Security pointed out that the famous "com.com" domain name was sold by CNET to known typo squatter dsparking.com [1]. Apparently, dsparking.com paid $1.5 million for this particular domain. Currently, the whois information uses privacy protect, and DNS for the domain is hosted by Amazon's cloud.
All .com.com hostnames appear to resolve to 54.201.82.69, also hosted by Amazon (amazon.com.com is also directed to the same IP, but right now results in more of a "Parked" page, not the fake anti-malware as other domains)
The content you receive varies. For example, on my first hit from my Mac to facebook.com.com , I received the following page:
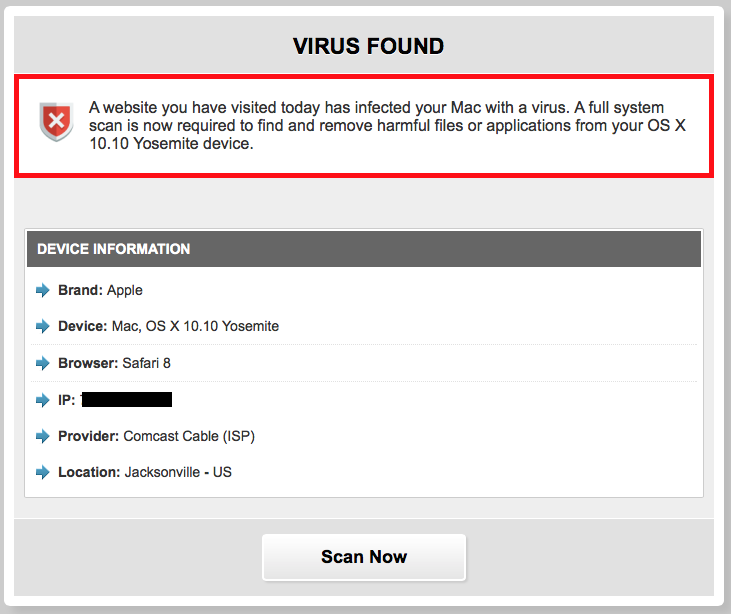
And of course the fake scan it runs claims that I have a virus :)
As a "solution", I was offered the well known scam-app "Mackeeper"
Probably best to block DNS lookups for any .com.com domains. The IP address is likely going to change soon, but I don't think there is any valid content at any ".com.com" host name.
The Whitehat article does speak to the danger of e-mail going to these systems. A MX record is configured, but the mail server didn't accept any connections from me (maybe it is overloaded?).
Amazon EC2 abuse was notified.
[1] https://blog.whitehatsec.com/why-com-com-should-scare-you/
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments
I understand why the browser makers do this, but it's about as good an idea as Site Finder was. (Remember Site Finder, back in 2003? It's how Network Solutions got themselves on my permanent shit-list.)
A second way, though useful only for someone running their own DNS server or cacheing resolver, would be to declare that it's authoritative for com.com, and respond to any such internally-originating queries either with localhost or some convenient dead-end system -- or even a monitored honeypot, if you have one handy.
Anonymous
Aug 10th 2015
1 decade ago
Anonymous
Aug 12th 2015
1 decade ago
I should note that this setting is deliberately hidden in Firefox, so you need to use about:config to change it. Look for the string "fixup", and change the boolean setting that enables this behavior to "false".
Anonymous
Aug 13th 2015
1 decade ago
For IE, the option has been obsolete since IE7 ( https://msdn.microsoft.com/en-us/library/ms536345(v=vs.85).aspx ).
Anonymous
Aug 18th 2015
1 decade ago