Attackers Search For Exposed "LuCI" Folders: Help me understand this attack
In the last couple of days, some of our web honeypots detected scans for "LuCI," LuCI is a user interface used by the widespread OpenWRT open-source router/firewall implementation. Scans for it are not specifically new. As with all perimeter security devices, they are significant targets, and simple vulnerabilities, as well as weak credentials, are often exploited.
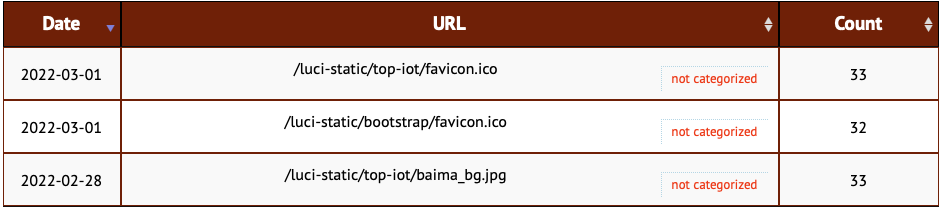
There appear to be three popular URLs among our honeypots:
/luci-static/top-iot/favicon.ico
/luci-static/bootstrap/favicon.ico
/luci-static/top-iot/baima_bg.jpg
The scan seems to check if the directories are present by verifying the existence of specific files. A quick Google search shows plenty of exposed "/luci-static" folders. But I haven't found any "top-iot" subdirectories and wonder what exploits may be used against this feature.
Can you help? If you are running OpenWRT (or are more familiar with it ... I haven't used it in a few years), do you know what "top-iot" contains? The name suggests some kind of IoT subsystem. I am mostly wondering what the attacker is exploiting here and what they would get from this request (to possibly better implement the response in our honeypots)
and remember: Never ever expose an admin interface to the internet!
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments
Anonymous
Mar 3rd 2022
3 years ago
However, I did find that a Chinese company called Baima Technologies manufacture a range of cellular IoT gateways; I'm guessing that these might use OpenWRT and that they've developed their own LuCI "application" for management purposes. https : // en.baimatech.com
Anonymous
Mar 4th 2022
3 years ago
Anonymous
Mar 4th 2022
3 years ago
Perhaps they're scanning for an openwrt based device which uses a custom theme?
Or they've found a vulnerability which these two themes introduce which isn't in the default theme?
Anonymous
Mar 7th 2022
3 years ago
I think it it may have something to do with the web site dubyadubyadubya.top-iot.com. They sell IOT hardware that uses OpenWRT. Perhaps if that file exists in that location it will identify a specific model or software version.
Anonymous
Mar 7th 2022
3 years ago