A Quick Summary of Current Reflective DNS DDoS Attacks
DNS is still a popular protocol to amplify denial of service attacks. A rather small DNS query, sent to an open recursive resolver, can be used to trigger a large response. Over the last few years, DNS servers implemented many countermeasures to make it more difficult to launch these attacks and easier to mitigate them. It also has become easier (but not trivial) to defend against these attacks. But in the end, you still have to "buy your way out" of a denial of service attacks. For smaller organizations, even an average attack can be devastating.
One of our large honeypots acts as an open resolver (with some rate limiting and other precautions to make them less effective as an amplifier). I collected data these last two weeks to see what targets are being attacked and which DNS records are used in these attacks.
The top two records (by a far distance) for DNS amplification these two weeks have been "access-board.gov" and the name servers for the root zone ("Root Hints"). .gov domains are very popular for two reasons: First of all, .gov supports DNSSEC, and with that responses tend to be larger. With DNSSEC also comes EDNS0 support, which allows for responses via UDP exceeding 512 bytes. These large responses may be fragmented and more difficult to block. Secondly, ".gov" is often considered trusted or even essential and not blocked as a result.
This chart of the top 4 domains used shows how the "access-board.gov" and "root" queries dominated the traffic
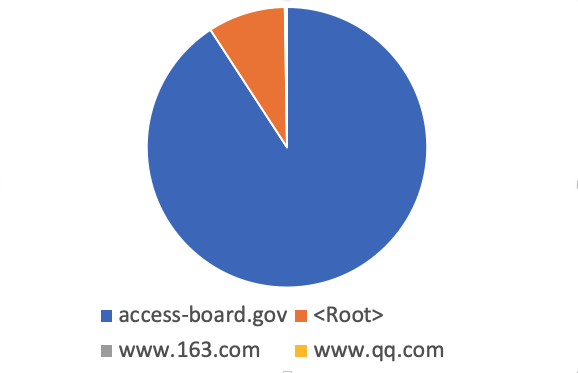
The access-board.gov ANY record is 2020 bytes long. It includes only one 'A' record. The remaining data is DNSSEC keys and signatures. Worse are domains like "peacecorp.gov". "peacecorp.gov" is also often used in DDoS attacks. the "ANY" record for peacecorps.gov is 3629 bytes long due to a number of TXT records that are included.
The Root NS record is not quite as long. But Windows DNS servers will respond to it by default which provides for a large set of possible reflectors. A short query (about 20 bytes) will result in 823 byte responses.
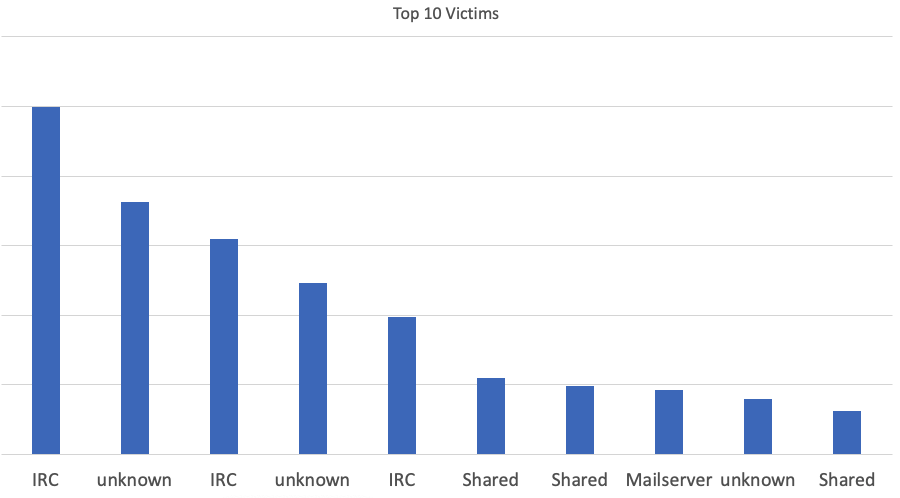
But who are the targets of these attacks? During these 2 weeks, we did see 368 targets. The top targets are IRC server. I guess some things never change, and IRC servers are still at the top of the DDoS list. What is probably more notable: The list is missing "household names" and appears more or less random. These attacks hit small businesses and home systems, not large banks and other "well known" services. Part of this is likely due to the fact that these larger companies have defenses in place to counter simple reflective DNS DDoS attacks. Smaller businesses are missing these defenses and are more vulnerable.
The top 10 victims ("Shared" means the server hosted multiple domains. "unknown" for servers that I couldn't reach (maybe as a result of the attacks) or a server where I couldn't figure out the purpose)
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS Technology Institute
Twitter|
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments