New (to me) nmap Features
Welcome to my first ever shift as an ISC Handler and my first ever handler diary entry!
I spent a little time today catching up on some emails I filed away for future reading. One of the emails that caught my attention was a write up on Fyodor's announcement at Defcon of new features in the new version of Nmap (was 4.75, 4.76 is out now) and the subsequent email from Fyodor on the nmap-hackers list. A few of these features caught my attention.
The first one is -top-ports. Essentially Fyodor and company spent the summer scanning the Internet and doing some research classified all the TCP and UDP ports by frequency found open.
According to their research
nmap -top-ports 10 <target>
will give you about 50% of the open ports and
nmap -top-ports 1000 <target>
will give you approximately 94% of the open ports.
The biggest difference is from a reconnaissance point of view. With the older nmap versions if you just let nmap loose with the default set of ports
nmap -sS -sU <target>
it would scan over a thousand TCP and UDP ports. It wasn’t quick against one IP, it was interminably slow against a large IP range. For this reason most pentesters have a small range of 20-50 ports they used to discovery scans. With – top-ports this is largely superfluous, although their may be reasons you might want to add extra ports based on the environment being scanned.
Another option that came out of this research is the Fast Scan option (-F).
nmap -F <target>
is perfect for discovery scans. It scans the top 100 ports of each protocol, increasing the speed from the default behaviour by an order of magnitude.
Taking a slightly different direction...I have always been an nmap command line bigot. This is partly because I have used nmap from the days when all that was available was the command line. Another reason is that I have never found an nmap GUI that I liked. Some of the new features in Zenmap have me re-evaluating that.
The two that got my attention are scan aggregation and mapping.
Nmap is finally capable of generating maps. More Info on the Zenmap mapping is available at http://nmap.org/book/zenmap-topology.html. Personally, I think the maps are still a little lightweight, but it is an outstanding start.
In short, scan aggregation is a feature that combines all scans performed from the same Zenmap window. This permits incremental scans, and analysis of the combined scan. Here is a screen shot of a couple of scans aggregated in Zenmap:
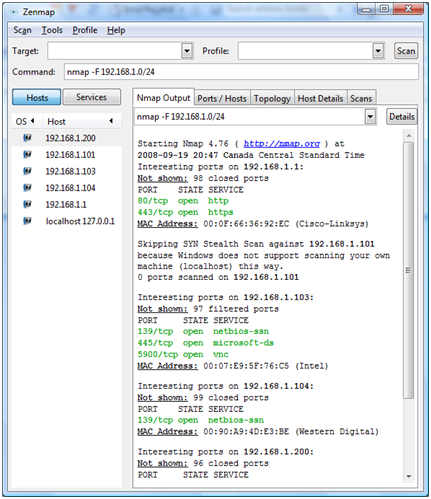
The mapping feature I still find a little lightweight, but it is an outstanding start. Here is the map from the same scan.
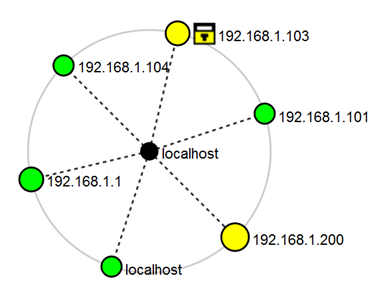
Some more detailed sample maps and a feature description are available at http://nmap.org/book/zenmap-topology.html.
Now if I can just get past my fear that nmap on Windows is somehow less accurate than nmap on *nix.
---
Rick Wanner - rwanner at isc dot sans dot org


Comments
With XP SP2 Microsoft introduced a limit on incomplete outbound TCP connections. XP SP2 has a limit of 10, Vista Home has a limit of 3.
So if nmap is making more than 3 outbound connections at a time, all but 3 will drop.
For XP SP2 there is a simple patch to fix this, for Vista the solution is very difficult.
nog_lorp
Sep 21st 2008
1 decade ago