Scans for Apache OfBiz
Today, I noticed in our "first seen URL" list, two URLs I didn't immediately recognize:
/webtools/control/ProgramExport;/ /webtools/control/xmlrpc;/
These two URLs appear to be associated with Apache's OfBiz product. According to the project, "Apache OFBiz is a suite of business applications flexible enough to be used across any industry. A common architecture allows developers to easily extend or enhance it to create custom features" [1]. OfBiz includes features to manage catalogs, e-commerce, payments and several other tasks.
Searching for related URLs, I found the following other URLs being scanned occasionally:
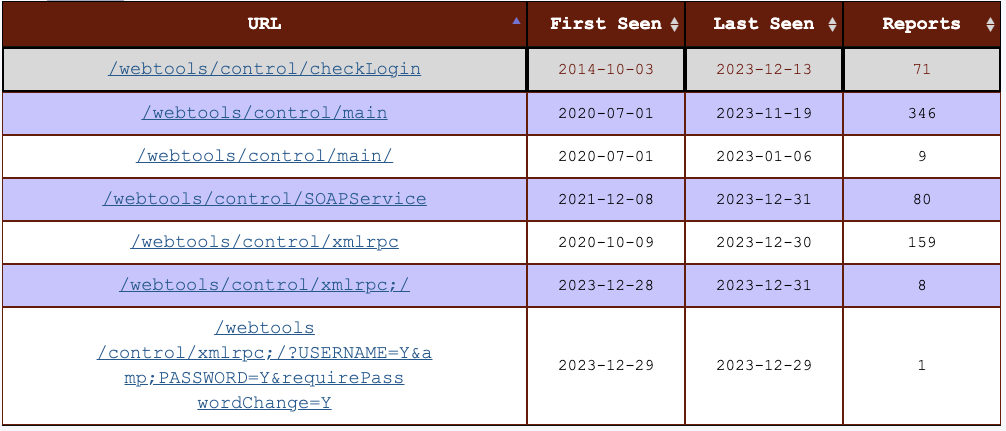
One recently patched vulnerability, CVE-2023-51467, sports a CVSS score of 9.8. The vulnerability allows code execution without authentication. Exploits have been available for a while now [3]. Two additional path traversal authentication bypass vulnerabilities have been fixed this year (CVE-2024-25065, CVE-2024-23946).
Based on the exploit, exploitation of CVE-2023-51467 is as easy as sending this POST request to a vulnerable server:
POST /webtools/control/ProgramExport?USERNAME=&PASSWORD=&requirePasswordChange=Y
{"groovyProgram": f'def result = "{command}".execute().text
java.lang.reflect.Field field = Thread.currentThread().getClass().getDeclaredField("win3zz"+result);'}
where "{command}" is the command to execute.
157.245.221.44 is an IP address scanning for these URLs as recently as today. The IP address is an unconfigured Ubuntu server hosted with Digital Ocean in the US. We started detecting scans from this server three days ago, and the scans showed a keen interest in OfBiz from the start.
[1] https://ofbiz.apache.org/
[2] https://issues.apache.org/jira/browse/OFBIZ-12873
[3] https://gist.github.com/win3zz/353848f22126b212e85e3a2ba8a40263
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments