Obfuscated Scans for Older Adobe Experience Manager Vulnerabilities
Adobe Experience Manager (AEM) is a complex enterprise-level content management system built around open-source products like Apache Sling, Jackrabbit/Oak, and Felix. Just last week, Adobe patched another XSS vulnerability in AEM. But the scans we see now target older vulnerabilities, likely a vulnerability 2-3 years old.
AEM includes "Dispatcher," which is responsible for load balancing but also has some web application firewall functionality. One of the "tricks" in exploiting AEM is to bypass this layer, and I think this is what may have been seen here.
For example, we do see in yesterday's and today's "First Seen" list two attempts:
/bin/wcm/..;/..;/bin/querybuilder.json.css
/bin/wcm/..;/..;/bin/querybuilder.json.css?path=/home&p.hits=full&p.limit=-1
They match common AEM exploits, but the /bin/wcm/...;/../; prefix may be meant to obfuscate the attack. Right now, I cannot pinpoint the particular vulnerability being exploited. If someone can help, please let me know. :)
Usually, the exploit URL looks like this:
/bin/querybuilder.json.css?p.hits=full&p.limit=-1&path=/home
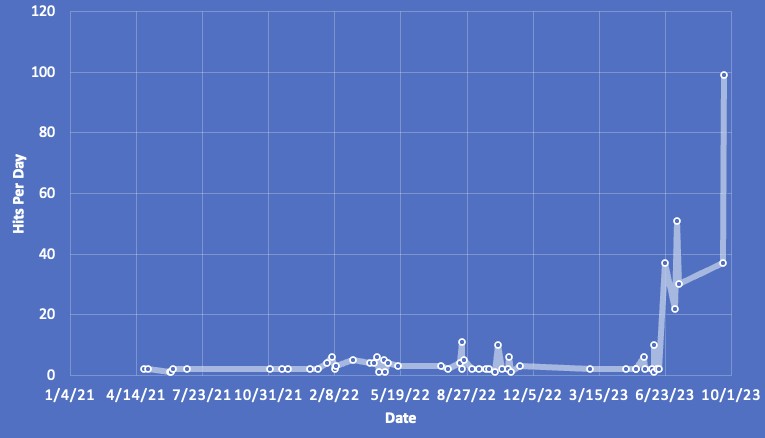
Queries for querybuilder.json.css are not very common. We have seen this so far in the last couple of years. There is certainly an increased interest in these vulnerabilities lately:
---
Johannes B. Ullrich, Ph.D. , Dean of Research, SANS.edu
Twitter|
| Application Security: Securing Web Apps, APIs, and Microservices | Orlando | Mar 29th - Apr 3rd 2026 |


Comments